Microsoft Entra ID Vulnerability Exposes Privilege Escalation Risk
Cybersecurity experts have identified a case of privilege escalation linked to a Microsoft Entra ID application, formerly known as Azure Active Directory, exploiting an abandoned reply URL.
Secureworks Counter Threat Unit (CTU) recently released a technical report detailing the discovery of this vulnerability. By exploiting the unused URL, attackers could redirect authorization codes to themselves, exchanging these codes for access tokens. Subsequently, threat actors could utilize a middle-tier service to invoke Power Platform API, thereby gaining elevated privileges.
Following responsible disclosure on April 5, 2023, Microsoft promptly addressed the issue with an update released the following day. In response to this revelation, Secureworks has also provided an open-source tool designed to assist other organizations in scanning for abandoned reply URLs.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The term “reply URL,” also referred to as a redirect URI, denotes the location to which the authorization server redirects users after successful app authorization, granting an authorization code or access token.
Secureworks CTU’s investigation unveiled an abandoned Dynamics Data Integration app reply URL associated with the Azure Traffic Manager profile. This configuration permitted the invocation of Power Platform API through an intermediate service, allowing potential manipulation of environment configurations.
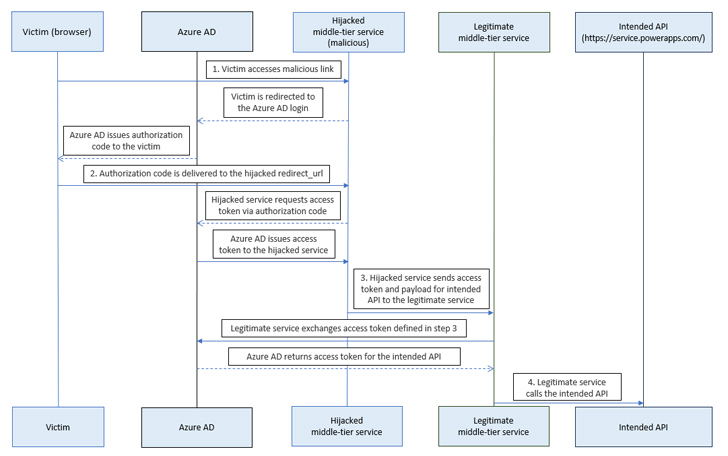
In a hypothetical attack scenario, this vulnerability could enable the acquisition of the system administrator role for an existing service principal. Subsequently, attackers could send requests to delete an environment and exploit the Azure AD Graph API to gather information about the target for further malicious activities.
Trending: Offensive Security Tool: BruteSpray
The attack scenario relies on the possibility of a victim clicking on a malicious link, leading to the delivery of an authorization code issued by Microsoft Entra ID to a hijacked redirect URL controlled by the attacker.
Coinciding with this revelation, Kroll reported an increase in DocuSign-themed phishing campaigns exploiting open redirects. These tactics enable adversaries to distribute specially crafted URLs that redirect victims to malicious websites upon clicking. By utilizing trustworthy websites, cybercriminals can deceive users and bypass network security measures designed to detect malicious content. This manipulation redirects victims to malicious sites aimed at extracting sensitive information, including login credentials, credit card details, and personal data.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com












