Microsoft Patches Windows Zero-Day Exploited to Spread Ransomware

Microsoft patches zero-day vulnerability exploited in ransomware attacks
Microsoft has recently patched a zero-day vulnerability discovered in the Windows Common Log File System (CLFS) that was being actively exploited by cybercriminals to escalate privileges and deploy Nokoyawa ransomware payloads. The flaw, tracked as CVE-2023-28252, affects all supported versions of Windows servers and clients and can be exploited by local attackers in low-complexity attacks without user interaction. If successfully exploited, threat actors could gain SYSTEM privileges and fully compromise targeted Windows systems. Security researchers with Kaspersky’s Global Research and Analysis Team (GReAT) have also found the CVE-2023-28252 flaw exploited in Nokoyawa ransomware attacks. Nokoyawa ransomware is a strain that emerged in February 2022, targeting 64-bit Windows-based systems in double extortion attacks, where the threat actors steal sensitive files and threaten to leak them online unless a ransom is paid.
In response to the ongoing exploitation of the vulnerability, CISA has added the CVE-2023-28252 Windows zero-day to its catalog of Known Exploited Vulnerabilities, ordering Federal Civilian Executive Branch (FCEB) agencies to secure their systems against it by May 2nd. Microsoft patched this zero-day and 96 other security bugs as part of this month’s Patch Tuesday, including 45 remote code execution vulnerabilities. Redmond has patched at least 32 local privilege escalation vulnerabilities in the Windows CLFS driver since 2018, with three of them (CVE-2022-24521, CVE-2022-37969, and CVE-2023-23376) also exploited in the wild as zero-days, according to Kaspersky.
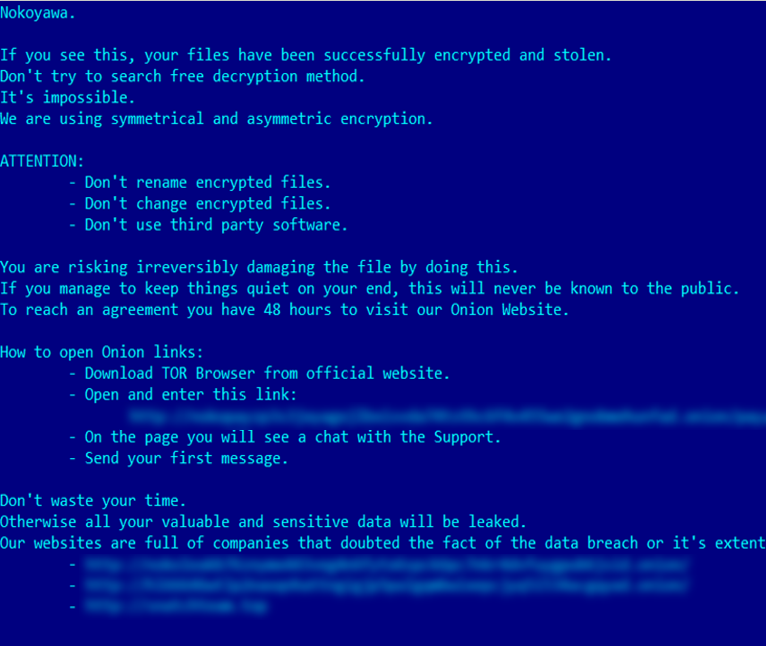 Nokoyawa ransom note (Kaspersky)
Nokoyawa ransom note (Kaspersky)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Nokoyawa ransomware gang
Kaspersky’s researchers uncovered the vulnerability in February as a result of additional checks into a number of attempts to execute similar elevation of privilege exploits on Microsoft Windows servers belonging to different small and medium-sized businesses in the Middle Eastern and North American regions. The Nokoyawa ransomware gang has used other exploits targeting the Common Log File System (CLFS) driver since June 2022, with similar yet distinct characteristics, linking them all to a single exploit developer. The group has used at least five more CLFS exploits to target multiple industry verticals, including but not limited to retail and wholesale, energy, manufacturing, healthcare, and software development.
Trending: Offensive Security Tool: Mythic
The Evolution of Nokoyawa Ransomware
Lead security researcher Boris Larin warns that cybercrime groups are becoming increasingly more sophisticated, using zero-day exploits in their attacks. Previously, zero-day exploits were primarily a tool of Advanced Persistent Threat actors (APTs), but now cybercriminals have the resources to acquire zero-days and routinely use them in attacks. Nokoyawa ransomware has been rewritten in Rust as of September 2022, in a switch from the initial version, which was developed using the C programming language. The hackers used a newer version of Nokoyawa that is quite distinct from the JSWorm codebase.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












