Microsoft SQL servers hacked with FARGO ransomware attacks

Reading Time: 3 Minutes
Vulnerable Microsoft SQL servers are being targeted in a new wave of attacks with FARGO ransomware, security researchers are warning.
MS-SQL servers are database management systems holding data for internet services and apps. Disrupting them can cause severe business trouble.
BleepingComputer has reported similar attacks in February, dropping Cobalt Strike beacons, and in July when threat actors hijacked vulnerable MS-SQL servers to steal bandwidth for proxy services.
The latest wave is more catastrophic, aiming for a quick and easy profit by blackmailing database owners.
See Also: So you want to be a hacker?
Complete Offensive Security and Ethical Hacking Course
FARGO ransomware, a.k.a. TargetCompany
Security researchers at AhnLab Security Emergency Response Center (ASEC) say that FARGO is one of the most prominent ransomware strains that focus on MS-SQL servers, along with GlobeImposter.
This malware family has been referred to as “Mallox” in the past because it used to append the “.mallox” extension to the files it encrypts.
Also, this strain is the same that Avast researchers named “TargetCompany” in a report in February, highlighting that files encrypted by it may be recovered for free in some cases.
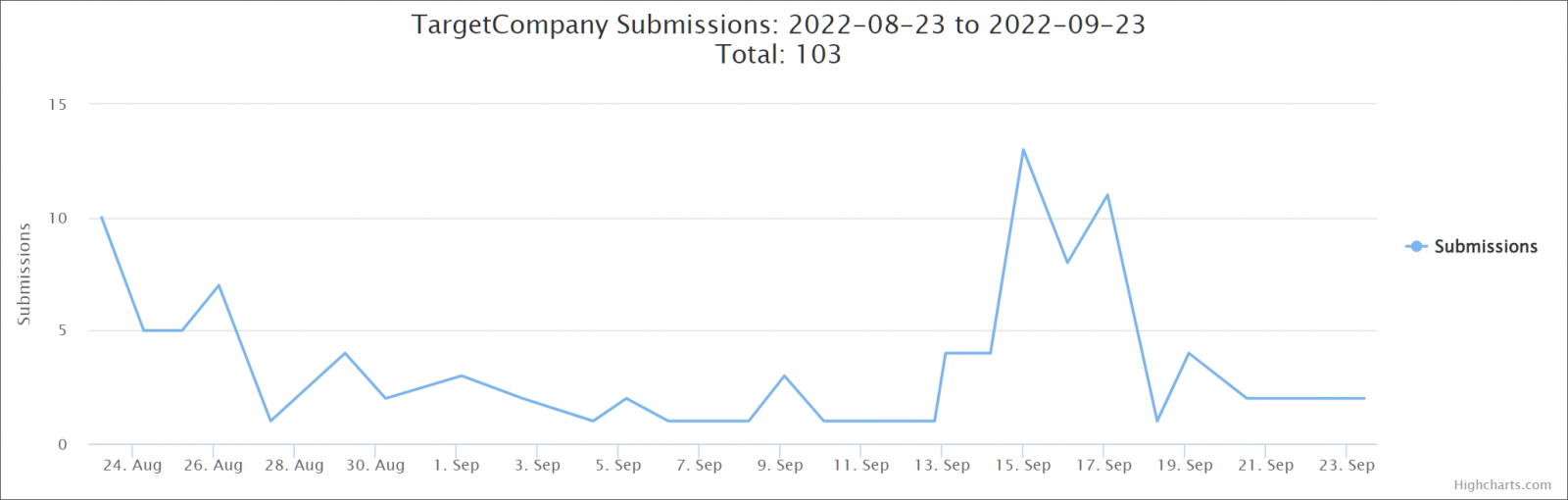
Statistical data about ransomware attacks on the ID Ransomware platform indicate that the FARGO family of file-encrypting malware is quite active.
Trending: OSINT Tool: Social Hunter
Infection and execution
The researchers note that the ransomware infection starts with the MS-SQL process on the compromised machine downloading a .NET file using cmd.exe and powershell.exe.
The payload fetches additional malware (including the locker), generates and runs a BAT file that terminates specific processes and services.
Next, the ransomware payload injects itself into AppLaunch.exe, a legitimate Windows process, and tries to delete the registry key for the open-source ransomware “vaccine” called Raccine.
Additionally, the malware executes the recovery deactivation command and terminates database-related processes to make their contents available for encryption.
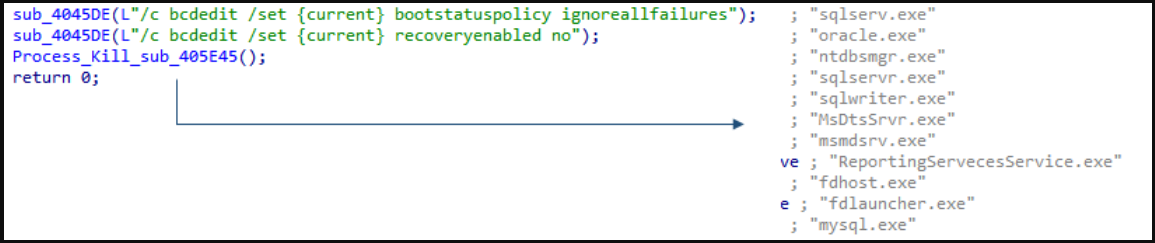
The FARGO ransomware strain excludes some software and directories from encryption to prevent the attacked system from becoming completely unusable.
Exempt from encryption are several Microsoft Windows system directories, the boot files, Tor Browser, Internet Explorer, user customizations and settings, the debug log file, or the thumbnail database.
After the encryption completes, the locked files are renamed using the “.Fargo3” extension, and the malware generates the ransom note (“RECOVERY FILES.txt”).
.png)
Victims are being threatened with leaking the stolen files on the threat actor’s Telegram channel, unless they pay the ransom.
Database servers are often compromised through brute-force and dictionary attacks that are successful against accounts protected with weak credentials. Alternatively, cybercriminals try to exploit known vulnerabilities that the target has not patched.
The recommendation for MS-SQL server administrators is to make sure that they use strong enough and unique passwords. Additionally, keeping the machine up-to-date with the latest fixes for security vulnerabilities is advice that never goes out of fashion.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












