Microsoft Uncovers Evidence of Russian Hackers Exploiting Outlook Vulnerability

Critical Flaw in Outlook Could Lead to Theft of NTLM Hashes
Microsoft has issued guidance to help its customers detect the indicators of compromise (IoCs) associated with a recently fixed Outlook vulnerability. The critical flaw, tracked as CVE-2023-23397, allowed attackers to carry out privilege escalation, enabling them to steal NT Lan Manager (NTLM) hashes and stage a relay attack without any user interaction. The vulnerability was fixed by Microsoft in March 2023 as part of its Patch Tuesday updates. However, it had been weaponized by Russian-based threat actors who attacked various government, transportation, energy, and military sectors in Europe. Microsoft’s incident response team found evidence of potential exploitation of the shortcoming as early as April 2022.
Source: thehackernews.com
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
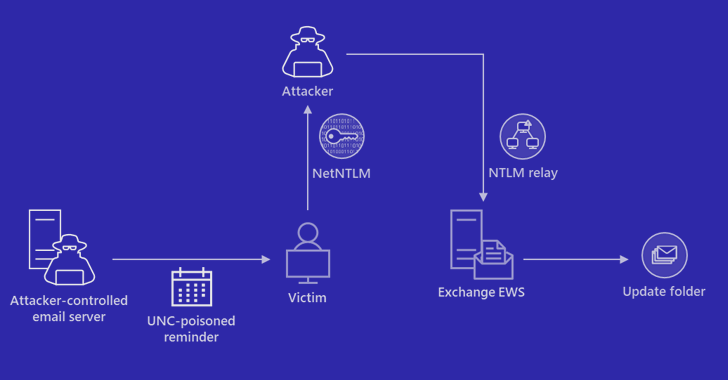
Net-NTLMv2 Relay attack chain
Microsoft described a successful Net-NTLMv2 Relay attack chain, which enabled the attackers to gain unauthorized access to an Exchange Server and modify mailbox folder permissions for persistent access. The compromised email account was used to extend the adversary’s access within the compromised environment by sending additional malicious messages to target other members of the same organization.
Microsoft recommends reviewing SMBClient event logging, Process Creation events, and other available network telemetry to identify potential exploitation via CVE-2023-23397.
Trending: Offensive Security Tool: OpenRediWrecked
Untitled Goose Tool by CISA
To help detect signs of malicious activity in Microsoft cloud environments, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has released a new open-source incident response tool called Untitled Goose Tool.
The Python-based utility provides novel authentication and data gathering methods to analyze Microsoft Azure, Azure Active Directory, and Microsoft 365 environments. Microsoft has also urged its customers to keep their on-premises Exchange servers updated and take steps to bolster their networks to mitigate potential threats.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com












