Microsoft Visual Studio Flaw Enables Impersonation of Trusted Publishers

Varonis Threat Labs has discovered a significant user interface (UI) bug (CVE-2023-28299) in Microsoft Visual Studio’s extension installer. This vulnerability allows attackers to manipulate extension signatures, effectively impersonating any publisher. Microsoft promptly addressed the issue by releasing a patch for CVE-2023-28299 on April 11, 2023.
Failure to apply the patch leaves systems susceptible to targeted attacks, as threat actors can distribute malicious extensions to compromise vulnerable systems.
Why is this a matter of concern? Visual Studio, the second most popular Integrated Development Environment (IDE) in the market, boasts a substantial user base of over thirty thousand customers, commanding a significant 26% market share.
Visual Studio’s appeal lies in its extensive collection of extensions, which range from integrating GitHub and SQL servers to simple productivity tools like spell checks and code snippets. The most popular extensions often accumulate millions of downloads. However, the UI bug discovered by Varonis Threat Labs (CVE-2023-28299) exposes a critical risk: threat actors can impersonate well-known publishers and distribute malicious extensions to compromise targeted systems. These malicious extensions have been known to facilitate data theft, unauthorized code access and alteration, and even complete system takeover.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The nature of the bug revolves around Visual Studio’s prevention of newline characters within an extension’s name, specifically by blocking user input in the “Product Name” extension property. However, this restriction can be easily bypassed by opening the VSIX file as a ZIP archive and manually adding newline characters to the “<DisplayName>” tag in the “extension.vsixmanifest” file.
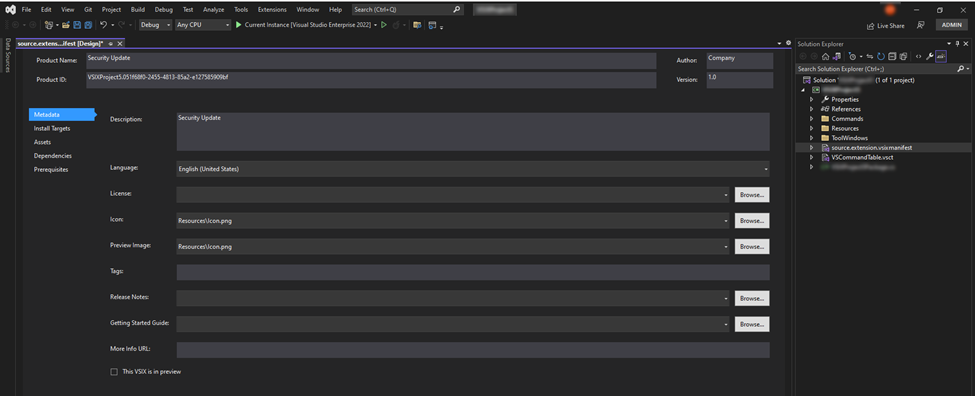 Creating a new C# project and editing its property
Creating a new C# project and editing its property
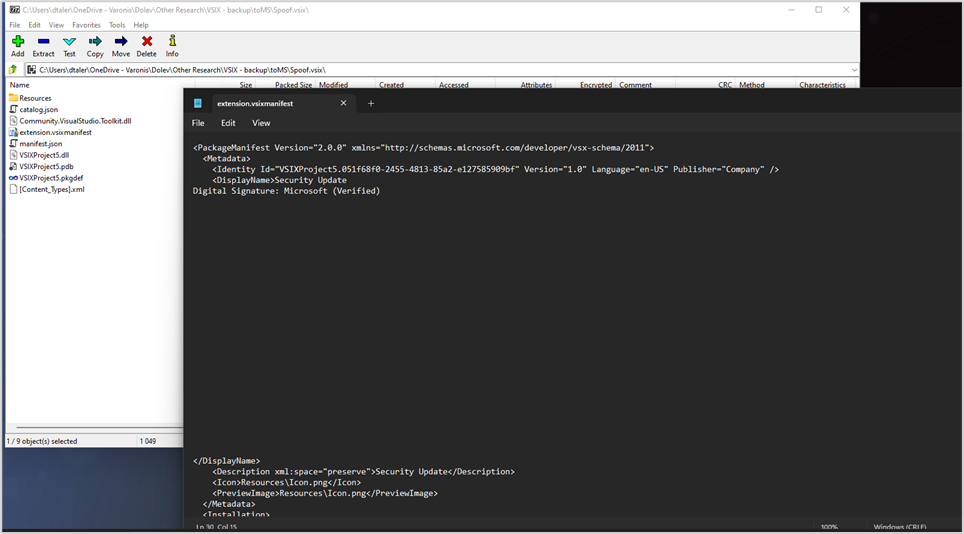 Editing in 7zip
Editing in 7zip
By adding a sufficient number of newline characters, the extension’s name pushes down the remaining text in the Visual Studio installation prompt, effectively concealing the warning “Digital Signature: None.”
Spoofing Signatures
This exploit allows threat actors to create a spoofed extension that appears legitimate but lacks a digital signature, a critical indicator of authenticity. Furthermore, the threat actor gains control over the extension’s signature area, enabling them to insert fake “Digital Signature” text that appears genuine to the user.
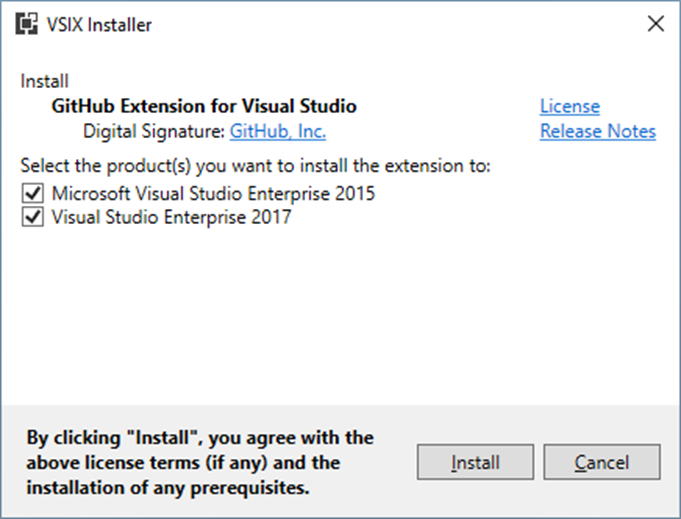 Real extension with digital signature
Real extension with digital signature
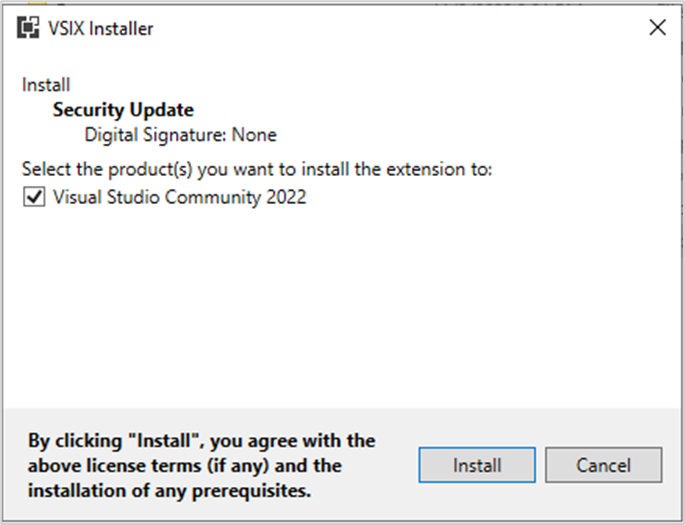 Extension without digital signature
Extension without digital signature
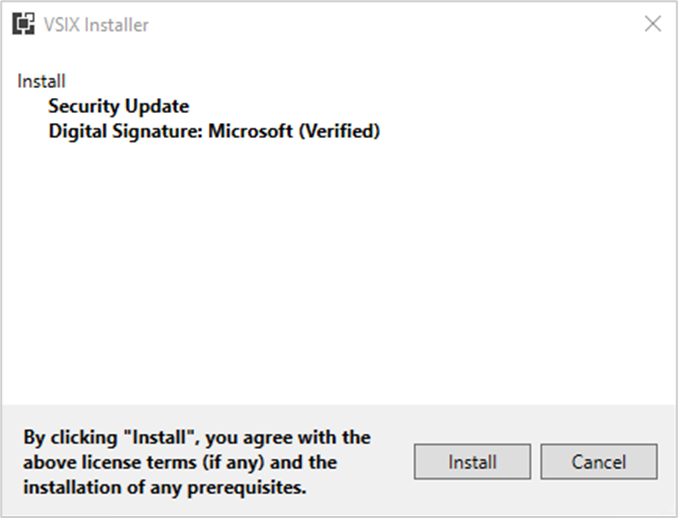 Extension with spoofed signature
Extension with spoofed signature
Trending: Offensive Security Tool: Pypykatz
The attack scenario unfolds primarily through phishing techniques. Here’s an example:
- The attacker disguises an email as a legitimate software update, targeting company developers.
- The email includes the spoofed VSIX extension, mimicking the appearance of a genuine update.
- Unable to differentiate the malicious VSIX from a legitimate signed update, the victim unknowingly installs the malicious extension.
- Once the crafted payload within the extension takes effect, the attacker gains a foothold in the victim’s machine, establishing an initial access point within the organization.
- With this initial access, the threat actor can proceed to move laterally within the compromised organization, potentially stealing intellectual property (IP), confidential data, and causing further business impact.
Microsoft responded promptly to this exploit, assigning it the CVE-2023-28299 identifier and including a fix in the Patch Tuesday update released on April 11, 2023. Varonis Threat Labs delayed the publication of this article to ensure that a fix was made available.
It is strongly recommended that all systems susceptible to this vulnerability apply the patch provided by Microsoft and remain vigilant for any suspicious activity.
In summary, CVE-2023-28299 highlights a critical UI bug in Microsoft Visual Studio, a leading IDE, which enables the spoofing of publisher digital signatures. The ease of exploitation, coupled with the potential consequences, makes this vulnerability a significant concern. Threat actors can exploit this flaw to distribute malicious extensions, posing a serious risk to compromised systems. Microsoft has acknowledged this vulnerability and addressed it through the release of a patch as part of their April 11, 2023, Patch Tuesday update.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: www.varonis.com












