Microsoft Warns of North Korean Hacking Groups Exploiting TeamCity Vulnerability

Microsoft’s Threat Intelligence Team has detected concerning activity involving North Korean hacking groups exploiting a critical security flaw in TeamCity servers. This vulnerability, identified as CVE-2023-42793, allows unauthenticated attackers to remotely execute code.
TeamCity serves as a continuous integration and deployment server, integral to software development infrastructure. The CVE-2023-42793 vulnerability, rated 9.8/10 in severity, was promptly addressed by TeamCity. However, it appears that malicious actors have been quick to exploit this weakness, thereby breaching corporate networks.
The specific intent behind these attacks remains undisclosed, but Microsoft has expressed concerns about the potential for software supply chain attacks. In past operations, North Korean threat actors, including Diamond Sleet and ZINC, have successfully conducted software supply chain attacks by infiltrating build environments.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The attack vectors in these operations involve the deployment of backdoors and the establishment of persistence on the compromised network. Lazarus, for instance, has been witnessed deploying the ForestTiger malware, which serves as a backdoor for executing commands on the compromised server.
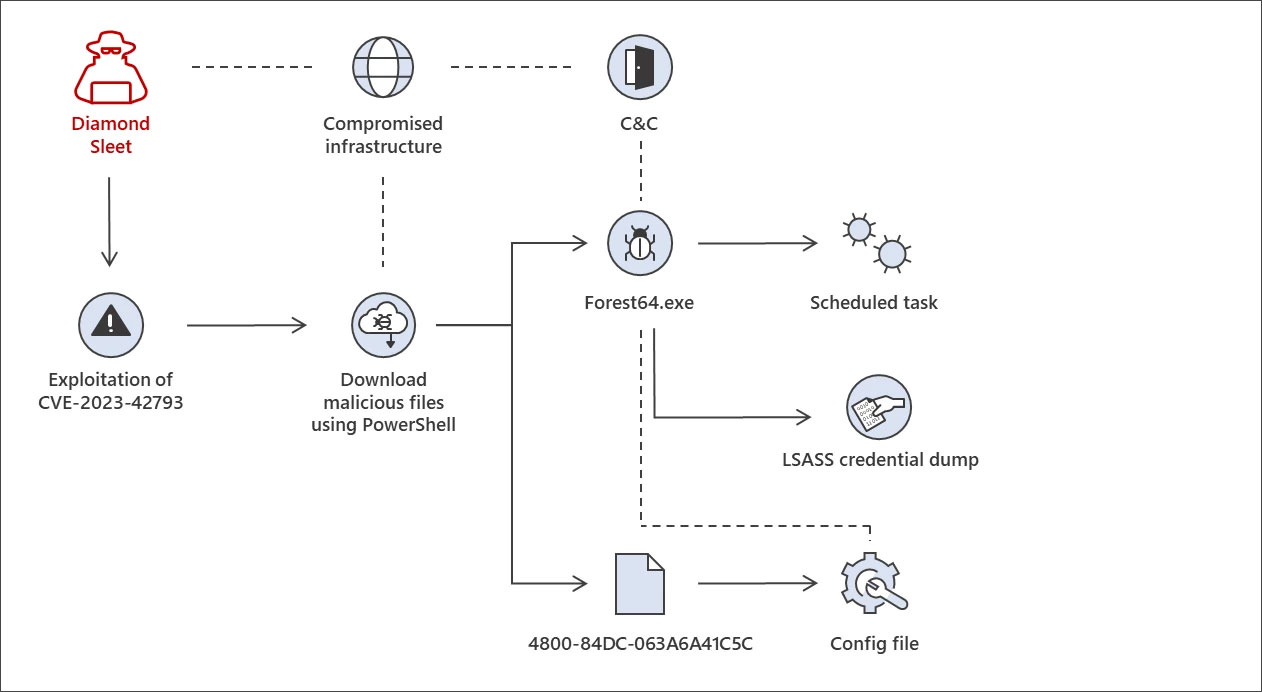 A Lazarus attack chain was seen after exploiting the TeamCity flaw
A Lazarus attack chain was seen after exploiting the TeamCity flaw
Source: Microsoft
Another attack chain involves DLL search order hijacking attacks, leading to the deployment of a remote access Trojan (RAT) via a malware loader called FeedLoad.
Andariel, a subgroup of Lazarus, adopts a more hands-on approach. They create an ‘krtbgt’ admin account on the compromised server and run commands to collect system information. Ultimately, a payload is deployed, installing the HazyLoad proxy tool, ensuring a persistent connection between the compromised server and Andariel’s infrastructure.
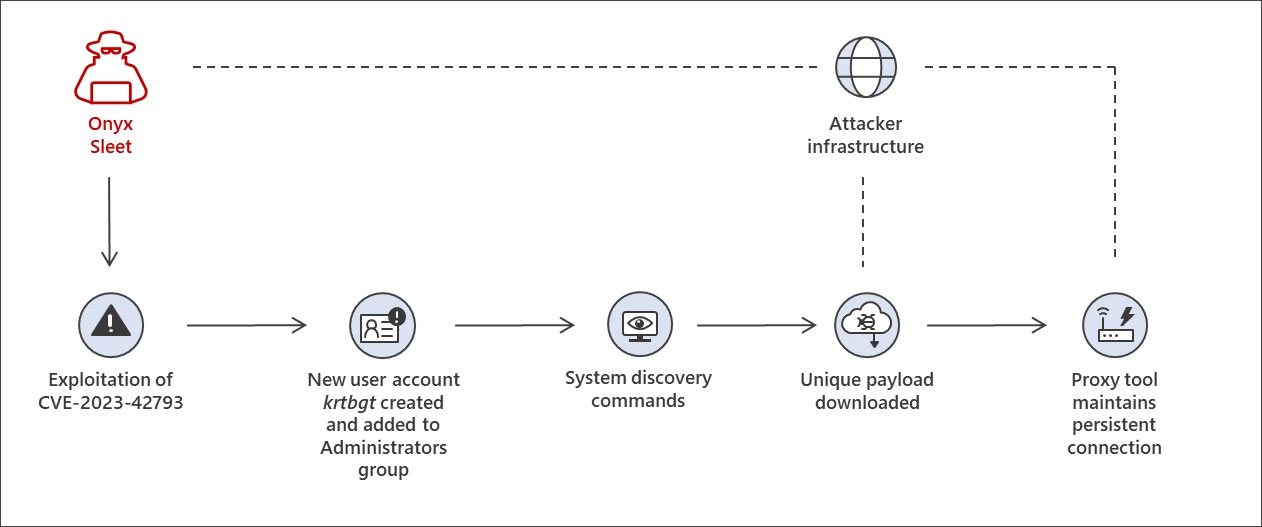 Andariel attack chain seen in breaches
Andariel attack chain seen in breaches
Source: Microsoft
The common thread across these attack chains is the exfiltration of credentials from LSASS, which is likely used to propagate laterally within the compromised network. Microsoft shared more details of the attack chain along with indicators of compromise in this article.
Trending: Recon Tool: fetchmeurls
Both Lazarus and Andariel are state-sponsored North Korean hacking groups. While their activities benefit the North Korean government, their objectives can vary.
Lazarus has been involved in espionage, data theft, and financial gain activities, whereas Andariel primarily targets defense and IT service entities, engaging in cyber espionage, data theft, destructive attacks, and even ransomware campaigns.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












