Microsoft’s Misconfigured Application Allowed for Real-Time Breach Attempts on Bing.com

BingBang Flaw
Microsoft has fixed a security flaw that could have allowed malicious actors to modify Bing.com search results and potentially breach the accounts of Office 365 users. The flaw was discovered by Wiz Research, which dubbed the attack “BingBang.”
According to Wiz researchers, the security issue arose due to a misconfigured Microsoft application that allowed users to log in and make modifications in real-time. The researchers found that when creating an application in Azure App Services and Azure Functions, it could be mistakenly configured to allow users from any Microsoft tenant, including public users, to log in to the application.
This configuration setting is called ‘Support account types’ and lets developers specify if a specific tenant multi-tenant, personal accounts, or a mix of multi and personal accounts should be allowed to access the application.
This configuration option is offered for legitimate cases where developers must make their apps available across organizational boundaries. However, if a developer mistakenly assigns looser permissions, it could cause unwanted access to the application and its features.
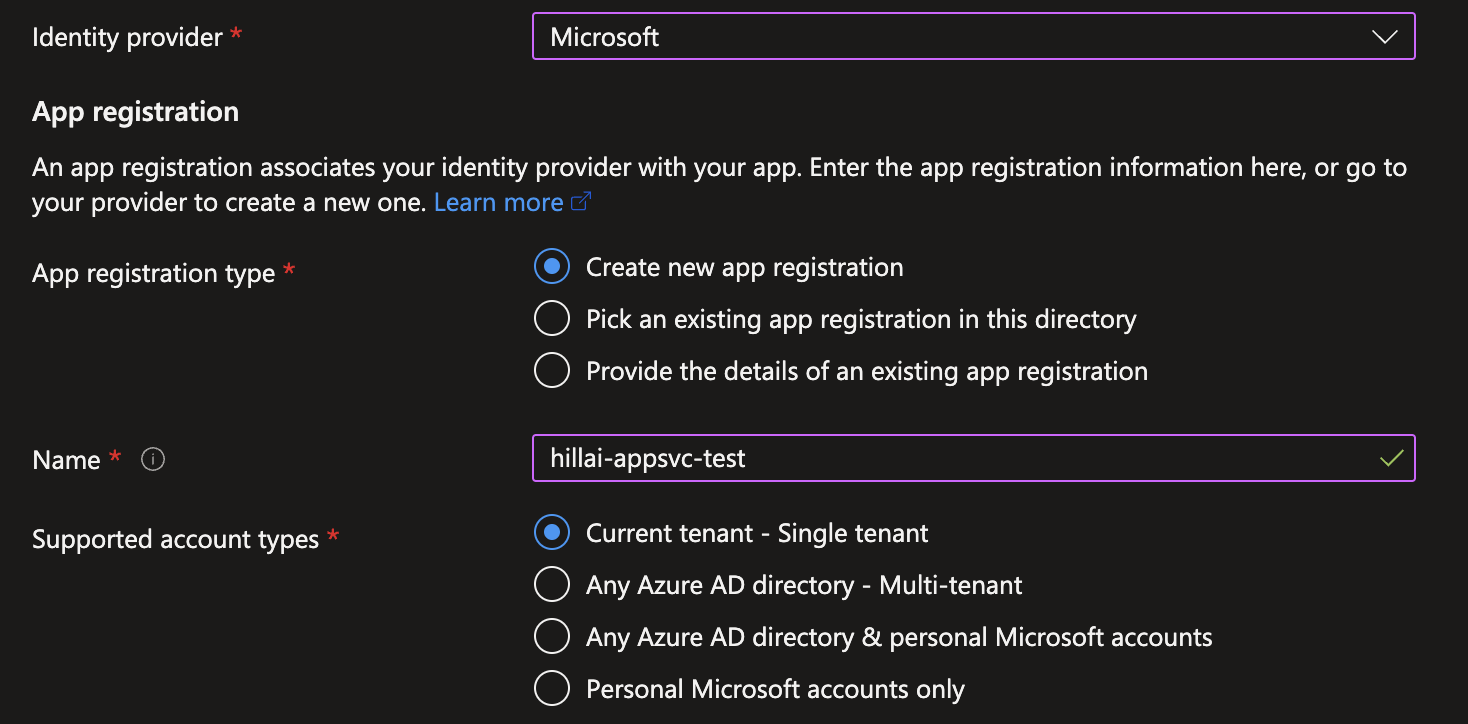 Azure AD user access configuration options (Wiz)
Azure AD user access configuration options (Wiz)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Wiz researchers also found a misconfigured “Bing Trivia” app that allowed anyone to log in to the application and access its CMS (Content Management System). The app was directly linked to Bing.com, allowing the researchers to modify the live content shown in Bing search results. They succeeded in modifying search results for the “best soundtracks” search term, adding arbitrary results to the top carousel.
XSS attacks
Next, the analysts tested if they could inject a payload into the Bing search results using this same CMS and found they could execute a cross-site scripting (XSS) attack on Bing.com.
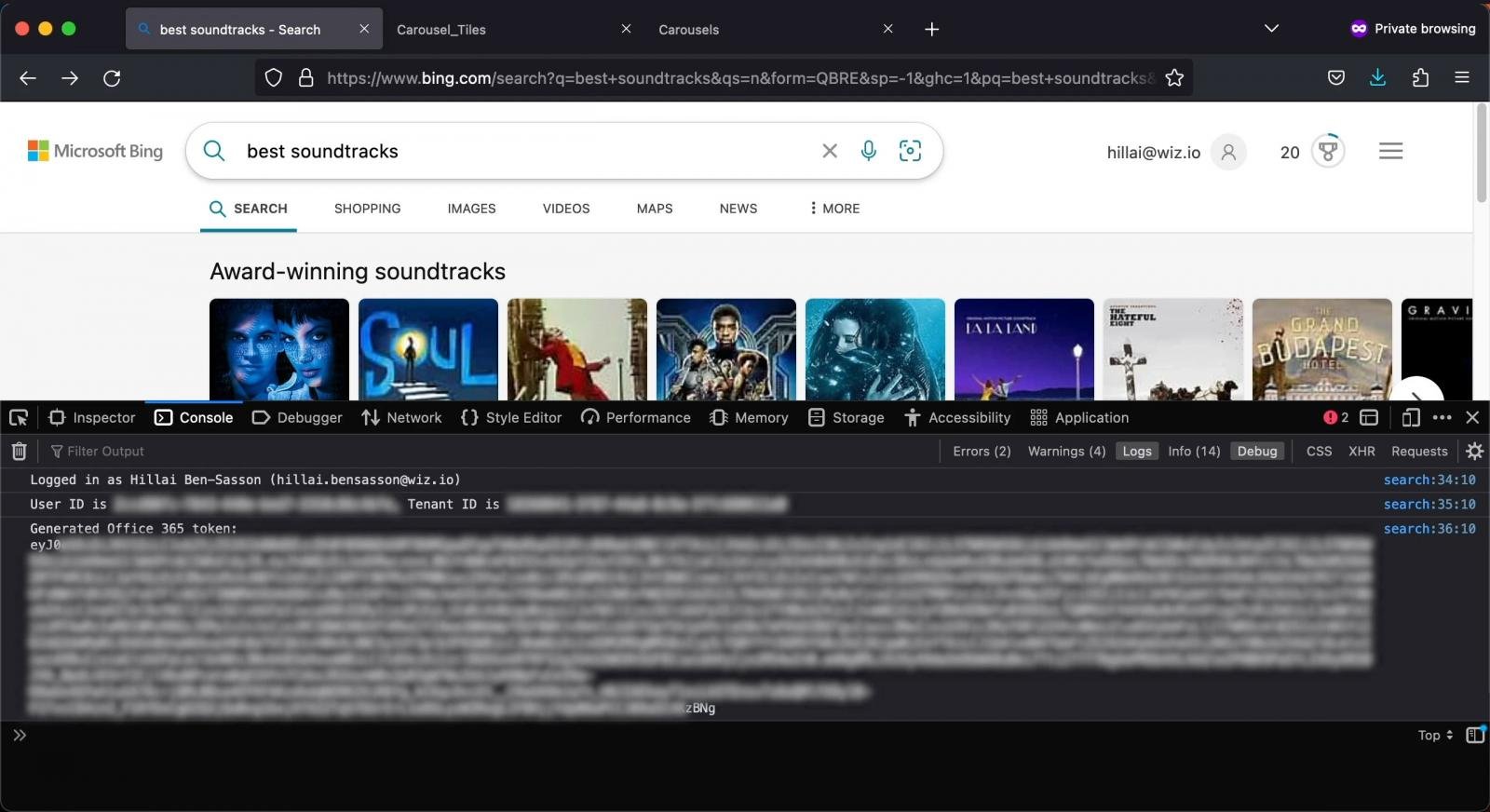 Bing.com XSS attack (Wiz)
Bing.com XSS attack (Wiz)
After confirming that the XSS was possible, Wiz reported its findings to Microsoft and worked with the software company to determine the exact impact of this second attack. A test XSS showed that it was possible to compromise the Office 365 token of any Bing user that saw the carousel in the search results, giving them full access to the searchers’ accounts, including access to Outlook emails, calendar data, messages on Teams, SharePoint documents, and OneDrive files.
Trending: Offensive Security Tool: OpenRediWrecked
Microsoft issues a fix
Microsoft downplayed the issue, saying that the misconfiguration that allowed external parties read and write access impacted only a small number of internal applications and was corrected immediately. Microsoft added that it has introduced security enhancements that will prevent Azure AD misconfiguration issues from becoming a problem again.
Microsoft has also stopped issuing access tokens to clients not registered in the resource tenants, limiting access only to properly registered clients. “This functionality has been disabled for more than 99% of customer applications,” reads Microsoft’s advisory. “For the remainder of multi-tenant resource applications that rely on access from clients without a service principal, we have provided instructions in an Azure Service Health Security Advisory to Global Admins (Azure Portal and email) and in the Microsoft 365 Message Center.”
In addition to these measures, Microsoft has also added additional security checks for multi-tenant applications, checking for tenant ID matching on a set allow-list and the presence of a client registration (Service Principal). Developers and admins that control multi-tenant applications are recommended to consult Microsoft’s updated guidance on securing them properly.
Wiz Research received a bug bounty of $40,000 for responsibly disclosing their findings to Microsoft. While Microsoft has fixed the issue, this security flaw underscores the importance of proper security configurations and highlights the risks associated with misconfigured applications. Developers and admins must be aware of the risks and take the necessary steps to secure their applications properly to avoid such issues in the future.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












