MinIO Under Siege: Threat Actor Exploits Critical Vulnerabilities

In a concerning development, an unidentified threat actor has been observed exploiting high-severity security vulnerabilities in the MinIO high-performance object storage system. This intrusion technique enables the attacker to achieve unauthorized code execution on targeted servers, potentially leading to significant data breaches.
Security Joes, a renowned cybersecurity and incident response firm, uncovered this threat and detailed its findings. The attacker’s strategy involved leveraging a publicly available exploit chain to establish a backdoor within the MinIO instance.
This alarming breach hinged on two specific vulnerabilities: CVE-2023-28432, with a CVSS score of 7.5, and CVE-2023-28434, rated at 8.8. Notably, CVE-2023-28432 was added to the U.S. Cybersecurity and Infrastructure Security Agency’s (CISA) Known Exploited Vulnerabilities (KEV) catalog on April 21, 2023.
Both of these vulnerabilities possessed the potential to expose sensitive data housed within the compromised MinIO installation. Furthermore, they facilitated remote code execution (RCE) on the host where the MinIO application was operational.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Security Joes’ investigation unveiled a troubling attack chain. The threat actor weaponized these vulnerabilities to acquire administrator credentials. With these credentials in hand, they exploited their foothold to replace the legitimate MinIO client on the host with a trojanized version. This was accomplished by triggering an update command, specifying a MIRROR_URL.
The MinIO documentation explains the update command’s purpose, which is to update all MinIO servers in the deployment, including support for private mirror servers.
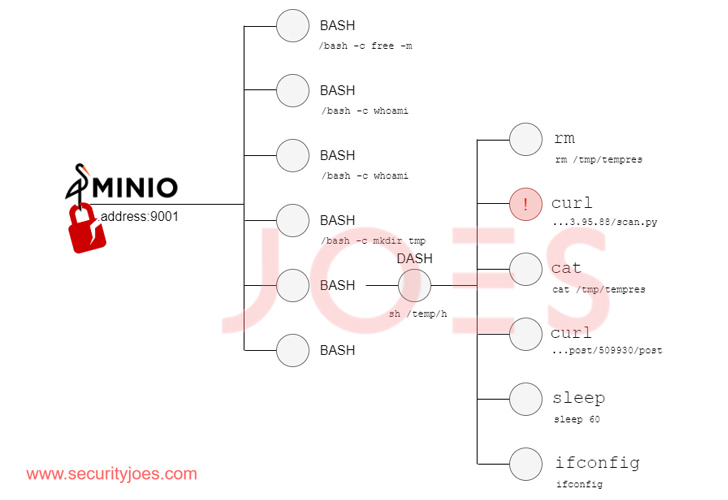
The consequences of these actions were severe. By replacing the authentic MinIO binary with a malicious counterpart, the attacker effectively sealed the compromise of the system. The tampered binary introduced an endpoint that executed commands via HTTP requests, effectively serving as a surreptitious backdoor. The executed commands inherited the system permissions of the user who initiated the application.
It’s worth highlighting that the modified binary bore a striking resemblance to an exploit named Evil MinIO, which had been published on GitHub in early April 2023. However, at this juncture, there is no concrete evidence linking the exploit’s author to the attackers.
Trending: Recon Tool: Dirhunt
What is clear, though, is the proficiency of the threat actor. They demonstrated adeptness in working with bash scripts and Python, leveraging their backdoor access to deliver supplementary payloads from a remote server for post-exploitation via a downloader script.
This downloader script exhibited versatility by targeting both Windows and Linux environments. Its role extended to profiling the compromised hosts, determining whether further execution was warranted, emphasizing the threat actor’s strategic approach to optimize their efforts based on the perceived value of the compromised system. This dynamic approach underscores the evolving sophistication of modern cyber threats and the need for robust cybersecurity measures.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com












