MortalKombat Ransomware: What You Need to Know About the Latest Threat

Reading Time: 3 Minutes
Hackers Using MortalKombat and Laplas Malware in Financially Motivated Cyberattacks
“MortalKombat” alongside the Laplas clipper in their latest financially-motivated campaign. MortalKombat encrypts various files on the victim machine’s filesystem, and Laplas is used to steal cryptocurrency by hijacking crypto transactions.
Talos researchers observed that the attacks mainly focused on the United States, with some victims in the UK, Turkey, and the Philippines.
Cisco Talos Detects Code Similarities between Xorist and MortalKombat Ransomware in New Campaign
In this new campaign, MortalKombat ransomware is based on the Xorist commodity ransomware family. According to Cisco Talos, the builder of Xorist allows threat actors to customize the malware, and it has been decryptable for free since 2016.
The code similarities between Xorist and MortalKombat suggest that the two are related. Researchers observed that the attackers used phishing emails to spread the malware.
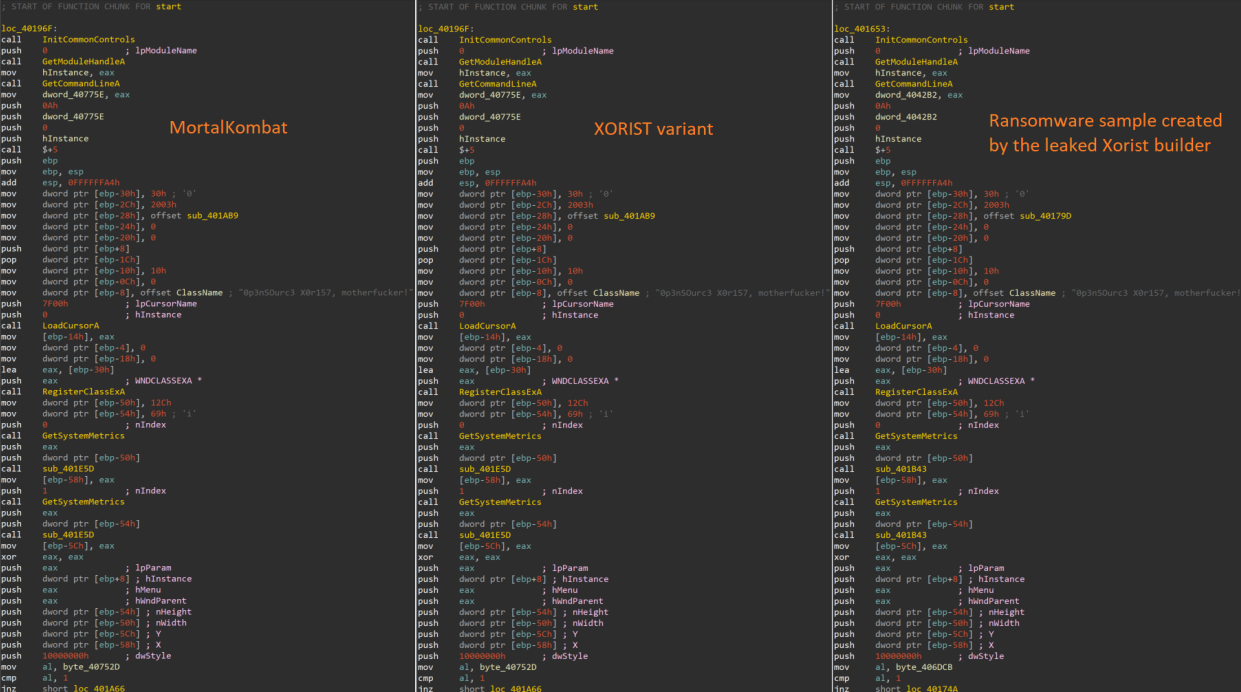 Code similarities between Xorist and MortalKombat (Cisco)
Code similarities between Xorist and MortalKombat (Cisco)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Phishing Attacks on the Rise
MortalKombat is a new variant of the Xorist ransomware family that researchers first detected in January 2023.
Phishing attacks are becoming more frequent, with emails containing malicious ZIP attachments that contain a BAT loader script that downloads a second archive from a remote resource. This archive contains one of the two malware payloads.
Talos analysts report that the ransomware targets system files and applications in addition to encrypting various files on the victim machine’s filesystem, which is not very sophisticated. MortalKombat encrypts database, backup, and virtual machine files, as well as files on remote locations mapped as logical drives.
The email message carrying the MortalKombat ransomware contains a malicious ZIP attachment that carries a BAT loader script. When opened, the script downloads a second archive from a remote resource containing one of the two malware payloads.
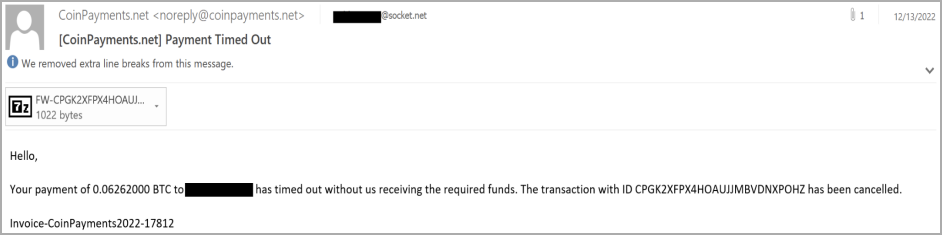 Sample of the phishing email (Cisco)
Sample of the phishing email (Cisco)
The loader script will execute the downloaded payload as a process in the compromised system and then delete the downloaded files to minimize the chances of detection.
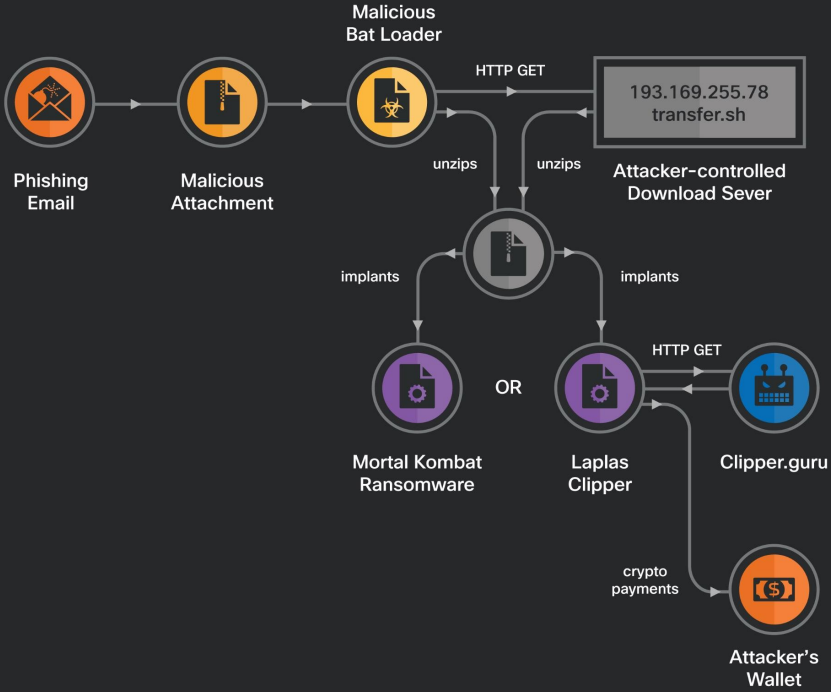 The campaign’s infection flow (Cisco)
The campaign’s infection flow (Cisco)
Trending: Major Cyber Attacks of 2022
Trending: Recon Tool: SauronEye
Protect Yourself from Financially Motivated Cyberattacks
To protect yourself from financially motivated cyberattacks, you should always be wary of opening attachments from unknown sources, especially if they contain ZIP files. In addition, be sure to keep your computer’s security software up to date, and regularly backup your files to ensure you always have access to important information.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












