Muddling Meerkat: Unprecedented Global DNS Manipulation by Chinese Threat Actors
A newly detected cluster of activity, labeled “Muddling Meerkat,” is believed to be connected to a Chinese state-sponsored threat actor’s manipulation of DNS systems to probe networks on a global scale since October 2019. Notably, a surge in activity was observed in September 2023.
An intriguing aspect of Muddling Meerkat’s operations is its manipulation of Mail Exchange (MX) records through the injection of false responses via China’s Great Firewall (GFW). This behavior, previously unseen in the country’s internet censorship system, showcases a level of sophistication and advanced capabilities in global DNS manipulation.
Discovered by Infoblox, the activity, while lacking a clear goal or motivation, demonstrates the adeptness of threat actors in manipulating DNS systems worldwide.
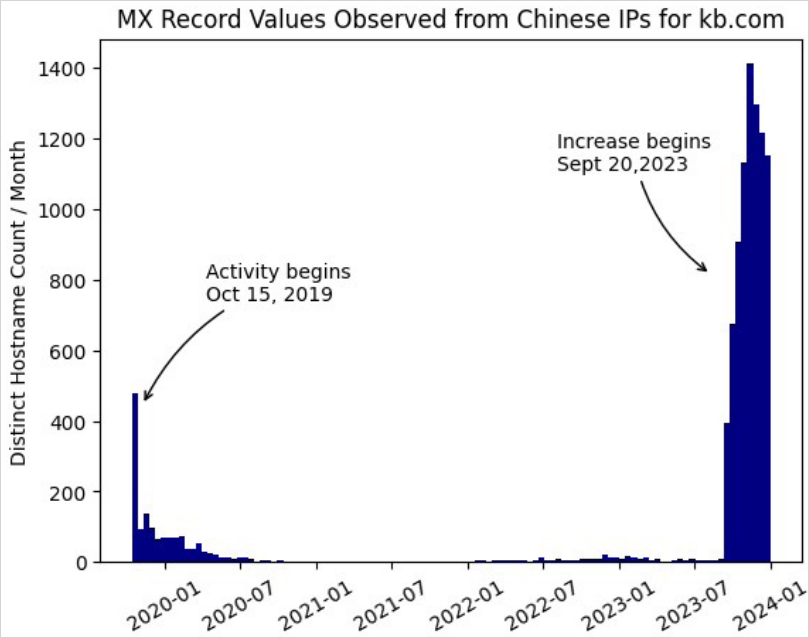 Observed volume of activity
Observed volume of activity
Source: Infoblox
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Muddling Meerkat operations
Muddling Meerkat operations entail the manipulation of DNS queries and responses, primarily targeting the mechanism through which resolvers return IP addresses. By provoking false responses from the GFW, the threat actors can tamper with routing and potentially redirect emails.
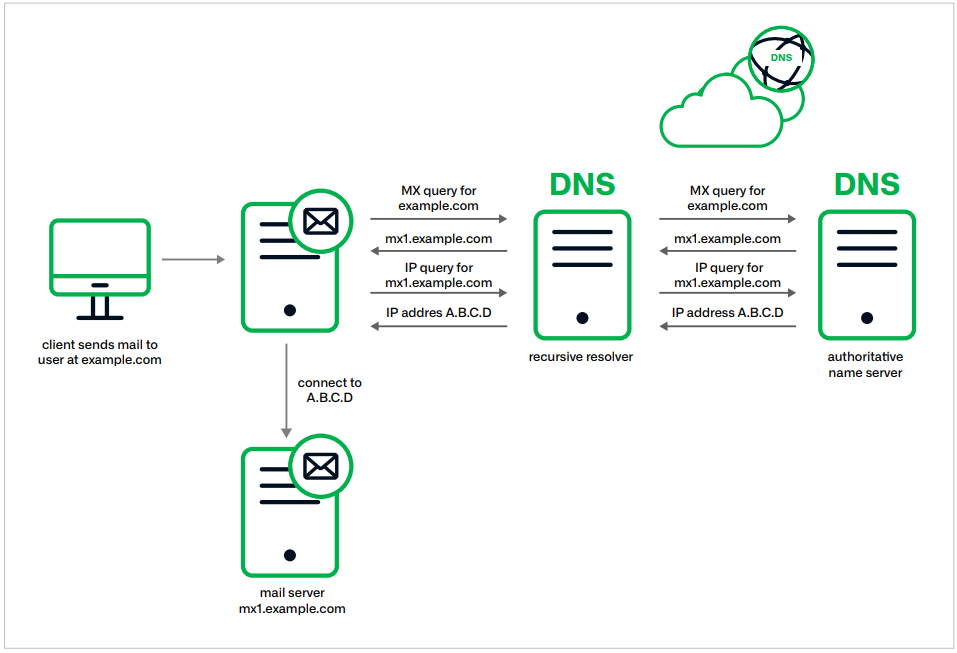 Standard MX request routing
Standard MX request routing
Source: Infoblox
Typically designed to filter and block content, the GFW’s function is subverted by Muddling Meerkat’s activities, which involve issuing fake responses to test the resilience and behavior of other networks.
To further obscure their activities, Muddling Meerkat makes DNS requests for random subdomains of target domains, a tactic reminiscent of “Slow Drip DDoS” attacks. However, unlike traditional DDoS attacks, these queries are small in scale and intended for testing rather than disruption.
Additionally, the threat actor exploits open resolvers and engages with both authoritative and recursive resolvers. They choose target domains with short names registered before 2000, making them less likely to be on DNS blocklists.
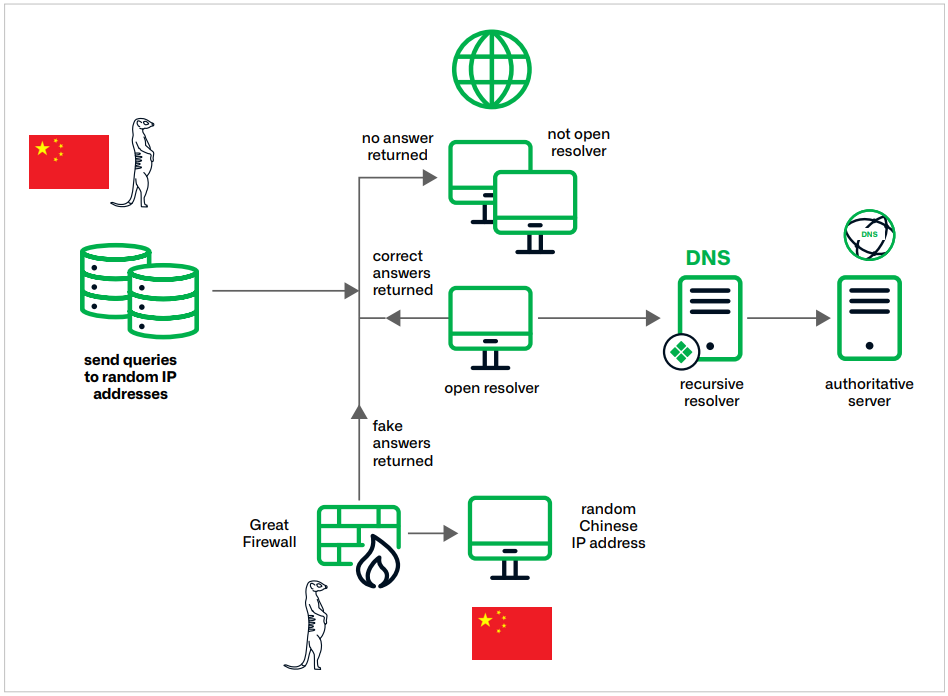 Overview of Muddling Meerkat operations
Overview of Muddling Meerkat operations
Source: Infoblox
Trending: Deep Dive to Fuzzing for Maximum Impact
Trending: OSINT Tool: Certina
The purpose of Muddling Meerkat’s activity remains speculative, with possibilities ranging from mapping networks and evaluating DNS security for future attacks to creating DNS “noise” to mask more malicious activities.
Infoblox’s report provides a comprehensive list of Muddling Meerkat’s indicators of compromise (IoCs) and techniques, tactics, and procedures (TTPs), offering insights into blocking domains without significant impact due to their hosting of illegal content or being parked.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













