New Acoustic Attacks Decipher Keystrokes in Any Environment

A groundbreaking study by researchers Alireza Taheritajar and Reza Rahaeimehr from Augusta University in the U.S. has revealed a novel acoustic side-channel attack targeting keyboards, capable of deducing user input by analyzing typing patterns, even amidst challenging conditions such as noisy environments.
While achieving an average success rate of 43%, which is notably lower compared to previous methods, this innovative approach eliminates the necessity for controlled recording settings or specific typing platforms, rendering it more adaptable in real-world attack scenarios. Depending on certain target-specific parameters, it can yield sufficient reliable data to decipher the overall input of the target with subsequent post-capture analysis.
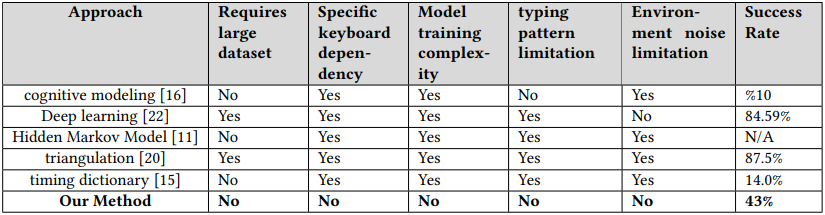 Comparison table (arxiv.org)
Comparison table (arxiv.org)
Acoustic Attack Technique
The technique, detailed in a technical paper published by the researchers, capitalizes on the unique sound emissions of different keystrokes and user typing patterns, captured through specialized software to compile a comprehensive dataset. Crucially, gathering typing samples from the target allows for correlation between specific keystrokes and associated sound waves.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
While the paper explores various methods for capturing text, potential avenues include malware, malicious websites or browser extensions, compromised applications, cross-site scripting, or compromised USB keyboards. Typing may be recorded using a concealed microphone in proximity to the target or remotely via compromised devices such as smartphones, laptops, or smart speakers.
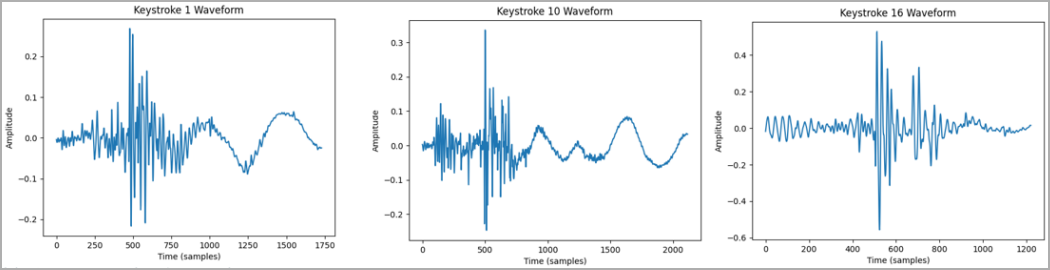 Extracted keystroke waveforms (arxiv.org)
Extracted keystroke waveforms (arxiv.org)
The compiled dataset encompasses typing samples under diverse conditions, necessitating recording of multiple typing sessions to bolster the success of the attack. However, the researchers emphasize that the dataset need not be excessively large.
Subsequently, a statistical model is trained on the dataset to construct a detailed profile of the target’s individual typing patterns, primarily based on time intervals between keystrokes.
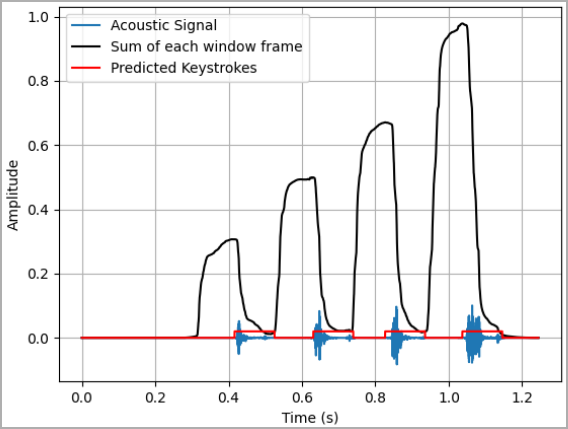 Calculating the time intervals (arxiv.org)
Calculating the time intervals (arxiv.org)
Maintaining a tolerance of 5% deviation in the statistical model proves crucial, as typing behavior exhibits slight variance even when typing the same word repeatedly.
Trending: Major Cyber Attacks that shaped 2023
Trending: Recon Tool: SiCat


