New Android Banking Malware MMRat Leverages Protobuf Serialization for Data Exfiltration

In a recent development, a novel Android banking malware named MMRat has emerged, harnessing an uncommon method of communication known as protobuf data serialization to streamline the process of data theft from compromised devices.
Trend Micro first identified MMRat in late June 2023. Remarkably, this malware has initially targeted users in Southeast Asia, successfully avoiding detection by popular antivirus scanning services like VirusTotal.
Although the precise method of MMRat’s initial distribution to victims remains uncertain, researchers have discovered that the malware is disseminated through deceptive websites posing as legitimate app stores. Unsuspecting victims download and install malicious apps carrying MMRat, often camouflaged as official government or dating applications. During installation, these apps request and acquire risky permissions, including access to Android’s Accessibility service.
Once infiltrated, MMRat capitalizes on the Accessibility feature to secure additional permissions, granting it the capability to execute a wide range of malicious actions on the compromised device.
Key Capabilities of MMRat Include:
- Gathering network, screen, and battery information.
- Exfiltrating the user’s contact list and list of installed apps.
- Capturing user input via keylogging.
- Extracting real-time screen content using the MediaProjection API.
- Recording and live-streaming camera data.
- Storing screen data as text form dumps for transmission to the C2 server.
- Self-uninstalling to erase all traces of infection.
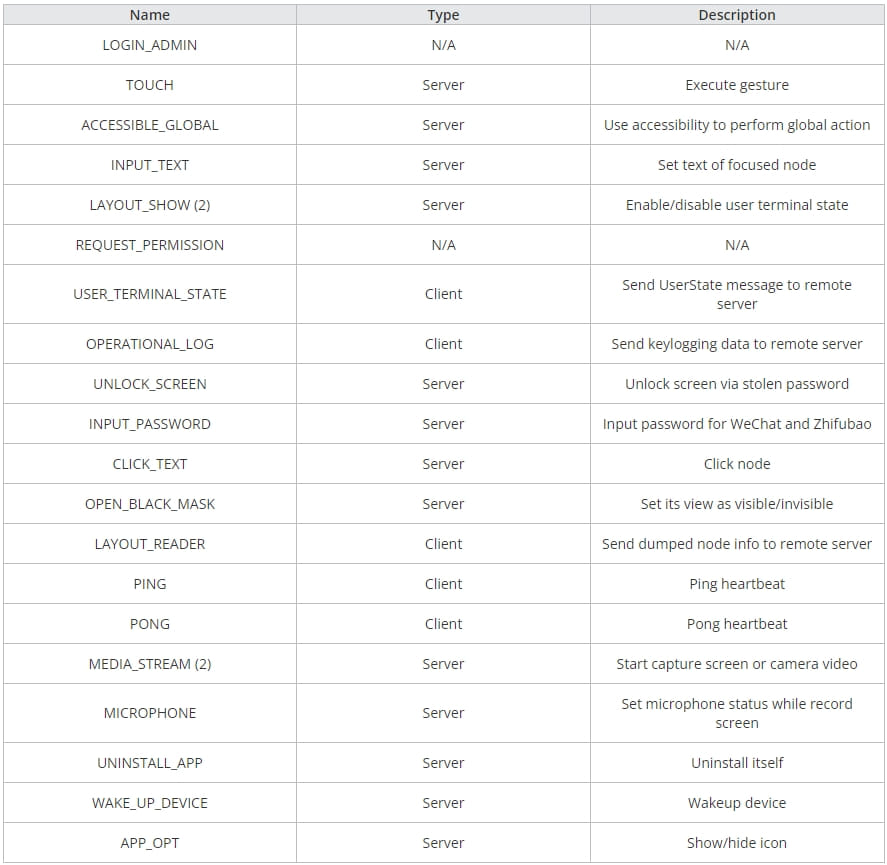 All commands supported by the malware (Trend Micro)
All commands supported by the malware (Trend Micro)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
To facilitate efficient data transmission, MMRat has incorporated a custom Protobuf protocol into its command and control (C2) server protocol. This protocol stands out in the realm of Android trojans for its utilization of protocol buffers (Protobuf) for streamlined data transfer.
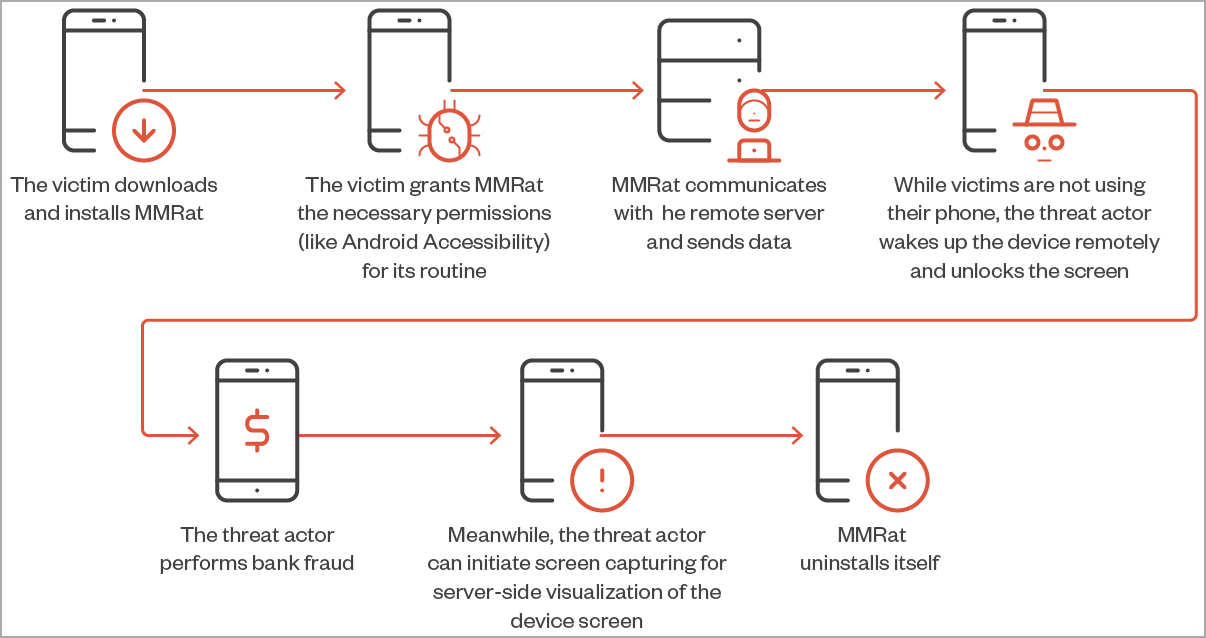 MMRat attack chain (Trend Micro)
MMRat attack chain (Trend Micro)
Protobuf
Protobuf is a serialization method developed by Google that, compared to XML and JSON, offers faster and smaller data representation.
MMRat employs distinct ports and protocols to engage with the C2 server, including HTTP on port 8080 for data exfiltration, RTSP and port 8554 for video streaming, and a custom Protobuf protocol on port 8887 for command and control.
Trend Micro’s report emphasizes the uniqueness and sophistication of MMRat’s C&C protocol, built with Netty (a network application framework) and Protobuf. This approach enables adaptable message structures and the capability to represent diverse data types using the “oneof” keyword.
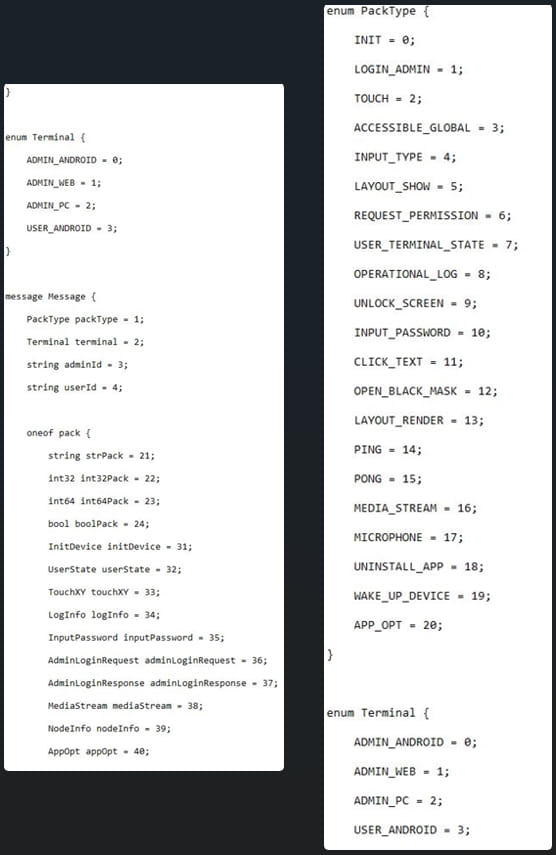 Protobuf schemas (Trend Micro)
Protobuf schemas (Trend Micro)
Trending: Offensive Security Tool: BruteSpray
The incorporation of Protobuf provides MMRat with several advantages. Its flexibility allows threat actors to define custom message structures while ensuring data compliance with a predefined schema. This structured nature also minimizes data corruption during transmission.
MMRat serves as a testament to the evolving complexity of Android banking trojans, effectively combining stealth with efficient data extraction. To protect themselves, Android users are advised to exclusively download apps from Google Play, scrutinize user reviews, place trust in reputable publishers, and exercise caution during the installation process, particularly when granting access permissions.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: info@blackhatethicalhacking.com
Source: bleepingcomputer.com












