New ‘Browser Syncjacking’ Attack Uses Chrome Extensions for Full Device Takeover

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Step-by-Step Breakdown of the Attack
1. Creating a Malicious Google Workspace
- The attacker creates a Google Workspace with multiple user profiles where security features such as multi-factor authentication (MFA) are disabled.
- This Google Workspace is used in the background to enroll the victim’s browser into a managed enterprise profile.
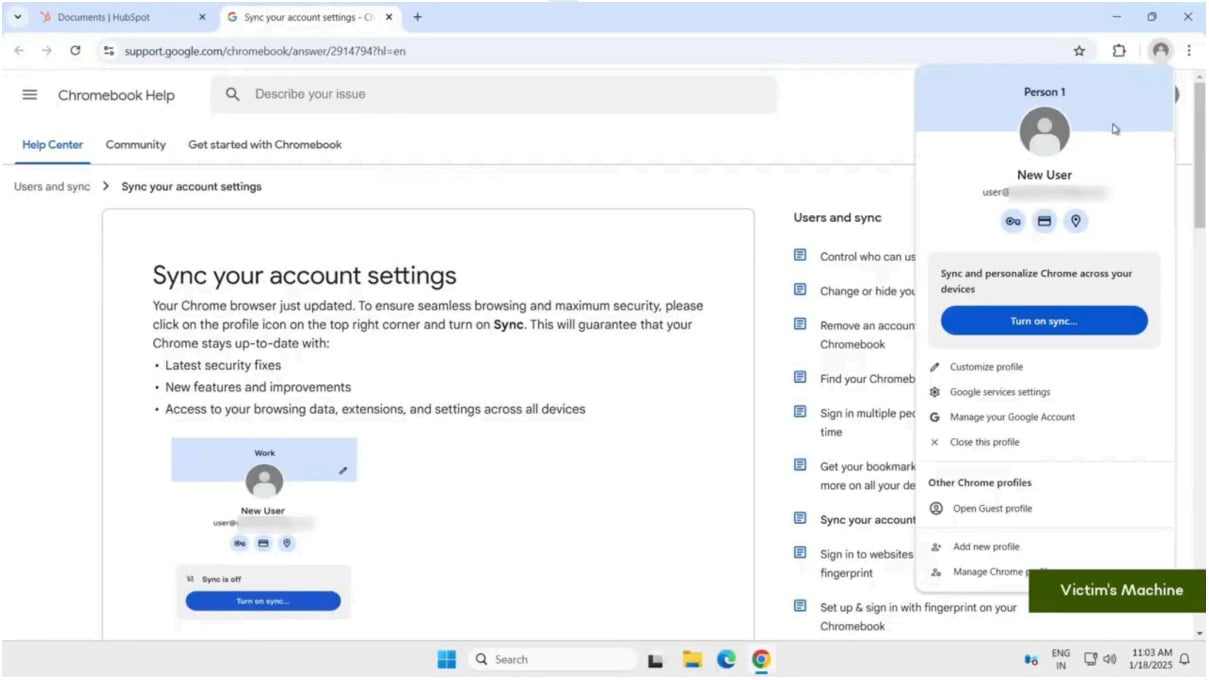 Victim opting to sync their browsing profile
Victim opting to sync their browsing profile
Source: SquareX
2. Distributing a Malicious Chrome Extension
- The attacker uploads a legitimate-looking Chrome extension to the Chrome Web Store, designed to appear like a useful productivity tool.
- Using social engineering, the victim is tricked into installing the extension.
At this point, no immediate signs of malicious activity occur, keeping the attack stealthy.
3. Forcing the User to Enable Chrome Sync
- The malicious extension quietly logs the victim into the attacker’s managed Google Workspace profile in a hidden browser window.
- The extension then opens a legitimate Google support page but injects content into it, instructing the user to enable Chrome Sync.
Why This Matters?
Once the victim syncs their browser, all their saved passwords, cookies, bookmarks, history, and authentication tokens become accessible to the attacker.
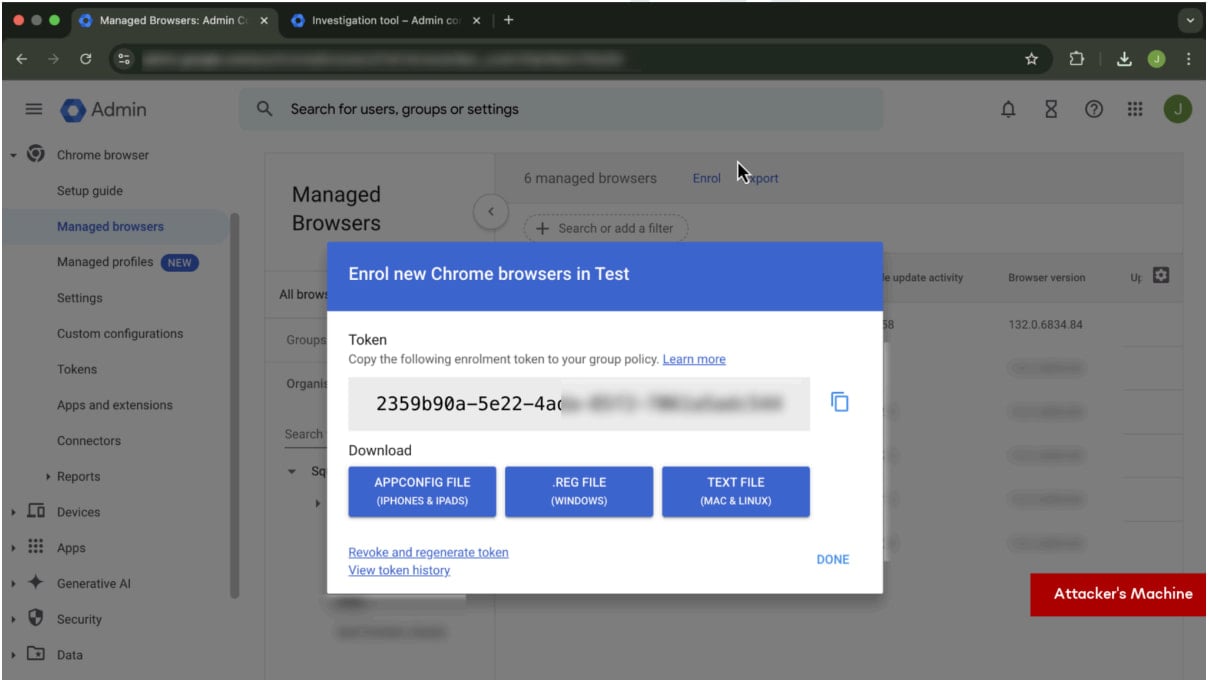 Enrolling the victim in a managed Google workspace
Enrolling the victim in a managed Google workspace
Source: SquareX
4. Browser Takeover via Fake Updates
- Now that the attacker controls the victim’s browser, they deliver a fake software update, such as a Zoom update prompt.
- If the victim downloads and runs the fake update, it enrolls the device into the attacker’s managed Google Workspace, giving them full control over the system.
 Prompting the victim to install a fake Zoom update
Prompting the victim to install a fake Zoom update
Source: SquareX
What Can the Attacker Do at This Stage?
- Silently access all web applications (Gmail, Drive, banking sites, etc.)
- Install additional malicious extensions
- Redirect the user to phishing sites
- Monitor or modify file downloads
- Browse directories and modify system files
- Install malware and execute arbitrary commands
- Capture keystrokes (keylogging)
- Stealthily access the victim’s webcam and microphone
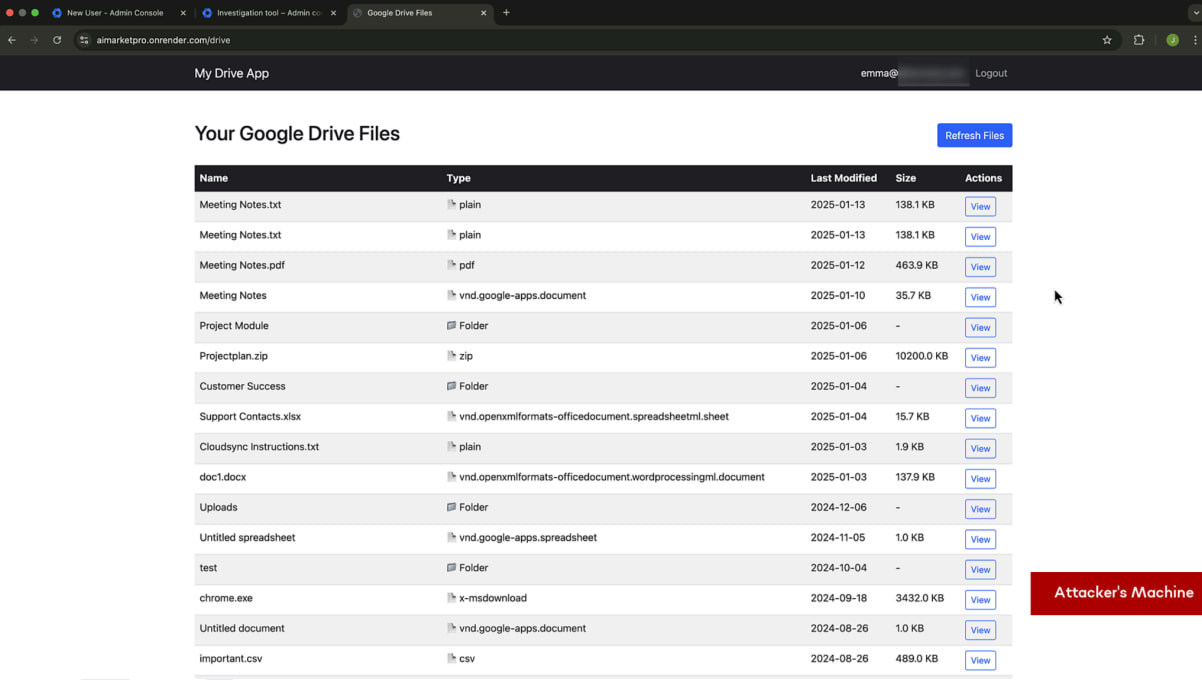 Accessing the victim’s Drive contents
Accessing the victim’s Drive contents
Source: SquareX
Trending: Offensive Security Tool: Penelope
Why This Attack is So Dangerous
- Requires minimal permissions – The extension does not need high-privilege permissions, making it harder to detect.
- No antivirus detection – Since the attack relies on legitimate Chrome features, traditional antivirus solutions may not flag it as malicious.
- Difficult to detect – The victim is unlikely to notice that their browser has been compromised, unless they actively check Chrome’s settings for managed browser indicators.
“Unless the victim is extremely security paranoid and technically savvy, there is no real visual indication that a browser has been hijacked.” — SquareX
Mitigation Strategies: How to Protect Yourself
- Never install unknown Chrome extensions, even if they appear useful or highly rated.
- Check if your Chrome browser is managed by going to:
- chrome://management → If your browser is managed by an unknown organization, remove the profile immediately.
- Disable Chrome Sync unless absolutely necessary.
- Manually review Chrome extensions in chrome://extensions and remove any suspicious ones.
- Avoid downloading software updates from pop-ups or redirected pages—always update directly from the official website.
- Enable multi-factor authentication (MFA) for Google accounts to prevent unauthorized logins.
Google’s Response
- BleepingComputer has reached out to Google for comment, and we will update this story if a response is received.
- Given the stealthy and dangerous nature of Syncjacking, it’s likely Google will implement new security measures to detect and prevent managed profile abuse in Chrome.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com



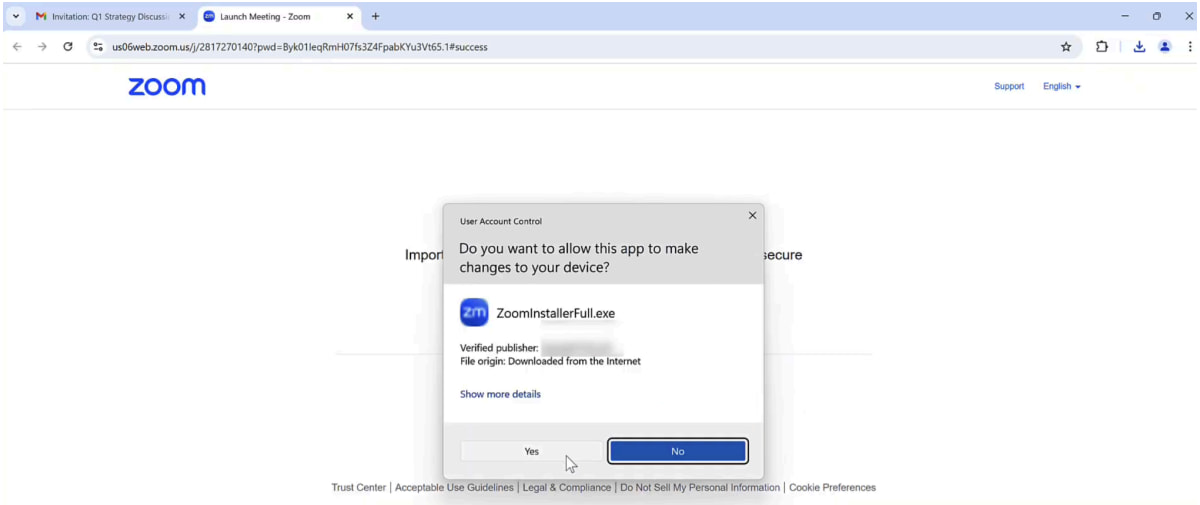 Prompting the victim to install a fake Zoom update
Prompting the victim to install a fake Zoom update









