New ‘Cheers’ Linux ransomware targets VMware ESXi servers

Reading Time: 2 Minutes
A new ransomware named ‘Cheers’ has appeared in the cybercrime space and has started its operations by targeting vulnerable VMware ESXi servers.
VMware ESXi is a virtualization platform commonly used by large organizations worldwide, so encrypting them typically causes severe disruption to a business’ operations.
We have seen many ransomware groups targeting the VMware ESXi platform in the past, with the most recent additions being LockBit and Hive.
The addition of Cheers ransomware to the club was discovered by analysts at Trend Micro, who call the new variant ‘Cheerscrypt’.
Infection and encryption
Once a VMware ESXi server is compromised, the threat actors launch the encryptor, which will automatically enumerate the running virtual machines and shut them down using the following esxcli command.
esxcli vm process kill –type=force –world-id=$(esxcli vm process list|grep ‘World ID’|awk ‘{print $3}’)When encrypting files it specifically seeks out files with the following .log, .vmdk, .vmem, .vswp, and .vmsn extensions. These file extensions are associated with ESXi snapshots, log files, swap files, paging files, and virtual disks.
Each encrypted file will have the “.Cheers” extension appended to its filename. Strangely, the renaming of files happens before encryption, so if access permission to rename a file is denied, the encryption will fail, but the file will still be renamed.
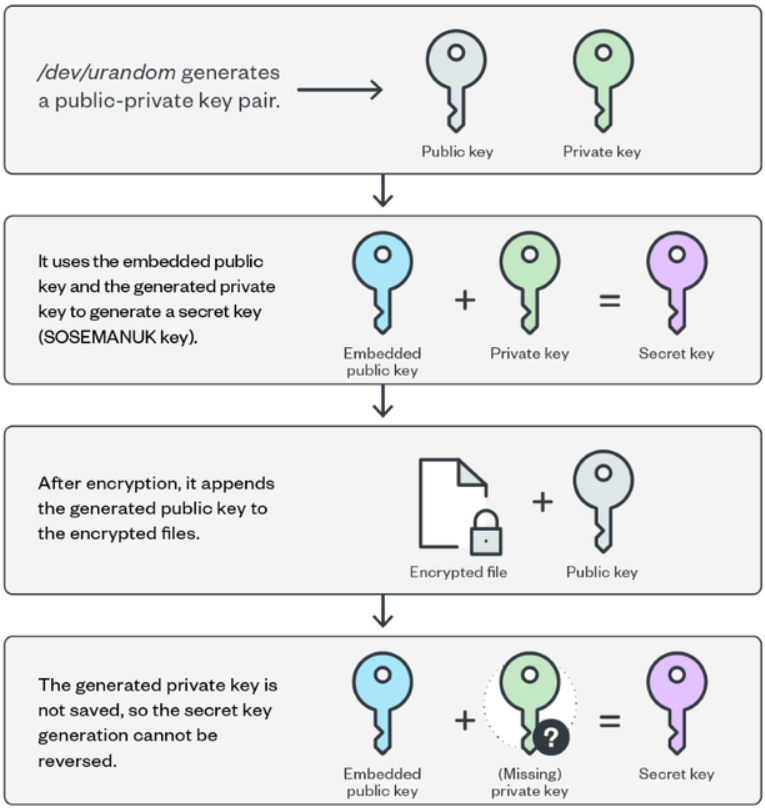
The encryption scheme uses a pair of public and private keys to derive a secret (SOSEMANUK stream cipher) key and embeds it in each encrypted file. The private key used for generating the secret key is wiped to prevent recovery.
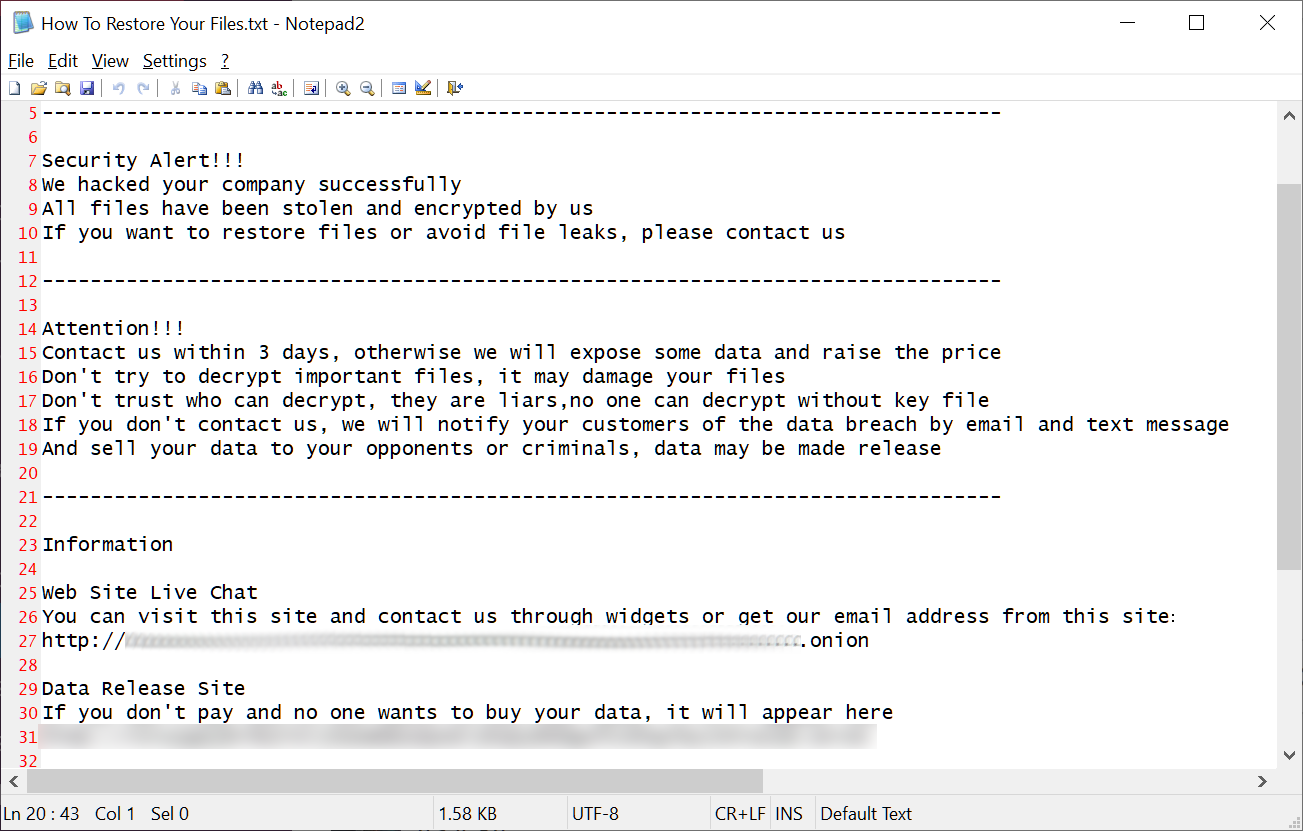
While scanning folders for files to encrypt, the ransomware will create ransom notes named ‘How To Restore Your Files.txt’ in each folder.
These ransom notes include information on what happened to the victim’s files and links to the ransomware operation’s Tor data leak sites and ransom negotiation sites.
Each victim has a unique Tor site for their negotiations, but the data leak site Onion URL is static.
Source: BleepingComputer
Based on BleepingComputer’s research into the new operation, it appears to have launched in March 2022.
See Also: Kali Linux 2022.2 released with new tools, terminal tweaks and more
While only a Linux ransomware variant has been found to date, there is likely a Windows variant available as well.
Uses double-extortion scheme
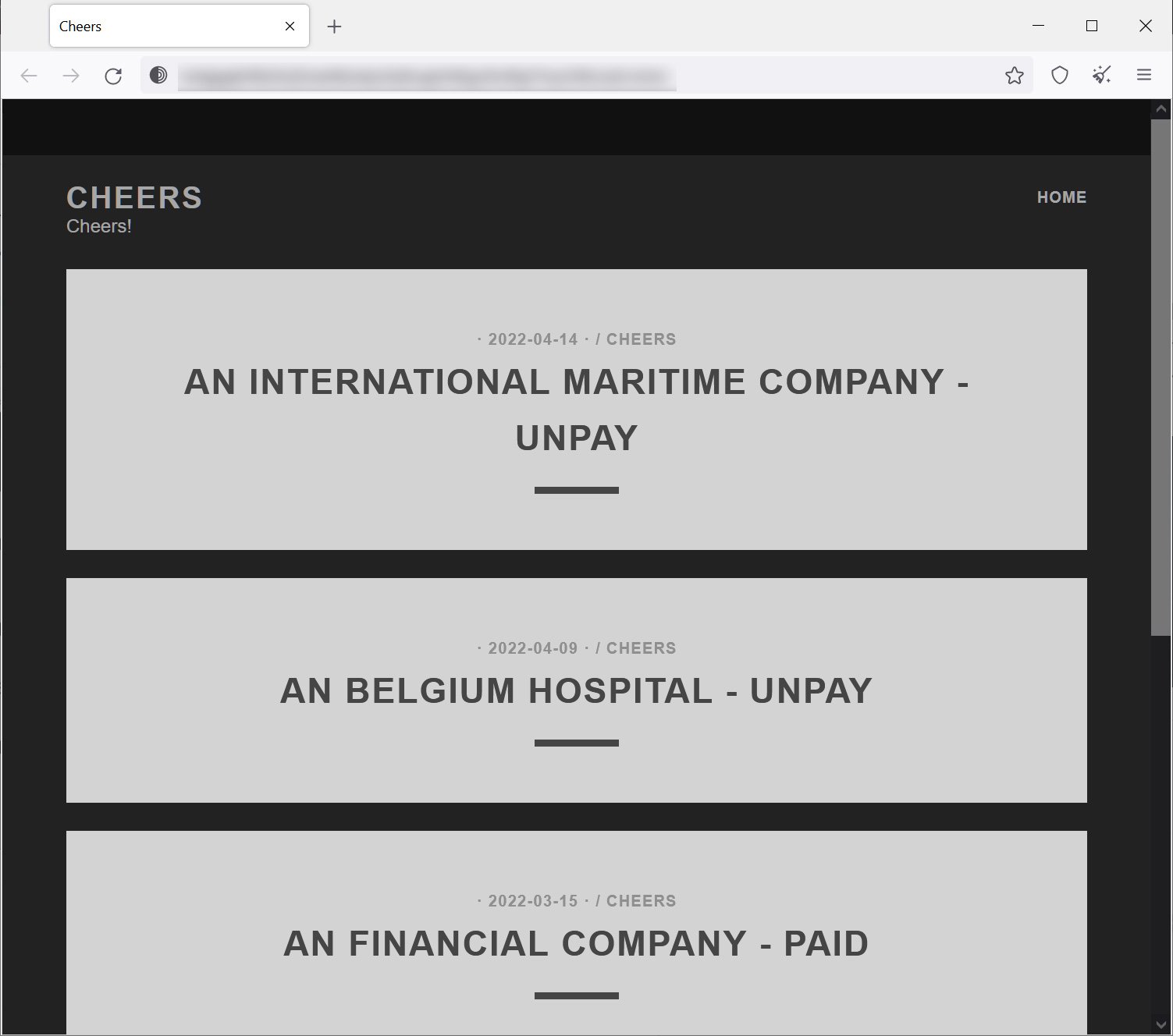
BleepingComputer found the data leak and victim extortion Onion site for the Cheers ransomware operation, which lists only four victims for now.
However, the very existence of this portal indicates that Cheers is performing data exfiltration during the attacks and using the stolen data in double-extortion attacks.
Source: BleepingComputer
The victims are of a semi-large size, so it appears that the new group prefers to hit companies that are in a position to cover larger demands.
See Also: Recon Tool: Dorks collections list
See Also: Write up: Find hidden and encrypted secrets from any website
Source: www.bleepingcomputer.com
Source Link













