New ‘Deadglyph’ Backdoor Malware Emerges in Middle East Government Cyberespionage

A highly sophisticated backdoor malware known as ‘Deadglyph’ has been identified in a cyberespionage campaign against a Middle Eastern government agency. This malware is attributed to the Stealth Falcon Advanced Persistent Threat (APT) group, also known as Project Raven or FruityArmor, which operates on behalf of the United Arab Emirates (UAE) government.
Stealth Falcon APT has a long history of targeting activists, journalists, and dissidents, spanning nearly a decade.
ESET researcher Filip Jurčacko presented a detailed analysis of this modular malware and its Windows device infection methods in a report unveiled at the LABScon cybersecurity conference.
Deadglyph Attack Details
While ESET researchers do not possess information about the initial infection vector, they suspect the use of a malicious executable, possibly a program installer.
ESET, however, managed to obtain most of the components involved in the infection chain, shedding light on how the malware functions and attempts to evade detection.
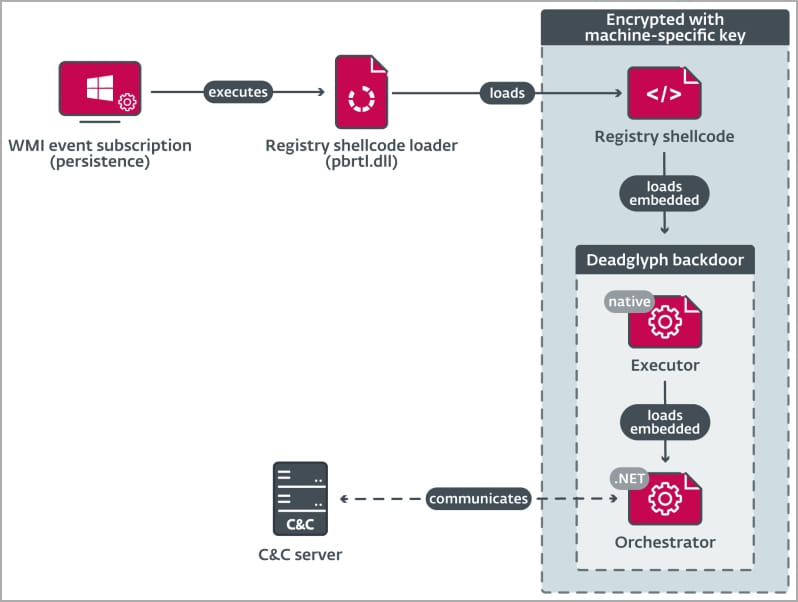
The loading process of Deadglyph initiates with a registry shellcode loader (DLL) responsible for extracting code from the Windows registry. This code is used to load the Executor (x64) component, which, in turn, loads the Orchestrator (.NET) component. Notably, only the initial component exists as a DLL file on the compromised system’s disk, reducing the likelihood of detection.
The loader retrieves an encrypted shellcode from the Windows Registry, making analysis more challenging. To further camouflage its presence, the DLL component leverages a homoglyph attack in the VERSIONINFO resource. This technique employs distinct Unicode characters, visually similar but not identical to the original characters, mimicking “Microsoft Corporation.”
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The Executor component’s functions include loading AES-encrypted configurations for the backdoor, initializing the .NET runtime on the system, loading the .NET portion of the backdoor, and acting as its library.
The Orchestrator, the final component, manages communication with the command and control (C2) server. It employs two modules for this purpose: ‘Timer’ and ‘Network.’ Importantly, if the backdoor fails to establish communication with the C2 server within a specified timeframe, it activates a self-removal mechanism to thwart analysis by security researchers.
 The Deadglyph loading chain (ESET)
The Deadglyph loading chain (ESET)
A Modular Malware
Deadglyph exhibits a modular structure, allowing it to download new modules from the C2 server. These modules contain various shellcodes that the Executor component executes.
This modular approach provides the threat actors with flexibility to create new modules as needed, tailoring attacks for specific purposes and pushing them to compromised systems to carry out additional malicious actions.
The modules possess both Windows and custom Executor APIs. The custom APIs offer 39 functions, enabling tasks such as file operations, executable loading, Token Impersonation, encryption, and hashing.
Although ESET identified only three modules—a process creator, an info collector, and a file reader—it estimates that there are between nine to fourteen different modules in total.
Trending: Recon Tool: Goblyn
The information collector employs Windows Management Instrumentation (WMI) queries to gather a wide range of data about the compromised system, including details about the operating system, network adapters, installed software, drives, services, drivers, processes, users, environment variables, security software, and more.
The process creator serves as a command execution tool, allowing the execution of specified commands as new processes. The results are then relayed to the Orchestrator.
The file reader module reads the content of files and shares it with the Orchestrator. It also provides the option for operators to delete the file after reading.
While ESET has only scratched the surface of Deadglyph’s capabilities, it’s evident that this malware poses a significant threat. Without detailed information regarding the initial infection vector, offering specific defense strategies against the malware remains a challenge. For now, defenders can rely on the indicators of compromise (IoCs) provided in the report to bolster their security measures.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












