New ‘Dev Popper’ Campaign Lures Developers with Job Offers, Spreads Python RAT

A newly identified campaign dubbed “Dev Popper” is honing in on software developers with a deceptive strategy of offering fake job interviews, aiming to dupe them into installing a Python remote access trojan (RAT).
Under the guise of legitimate job opportunities, developers are prompted to undertake tasks supposedly linked to the interview process, such as downloading and executing code from GitHub repositories.
However, the true intention of the threat actors is to coerce victims into downloading malicious software, which then gathers system data and establishes remote access to the compromised host.
Securonix analysts suspect that North Korean threat actors are behind the campaign, although the evidence for attribution is not definitive.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Dev Popper’s multi-stage infection chain
The “Dev Popper” attacks employ a multi-stage infection chain grounded in social engineering tactics, gradually leading targets towards compromise.
Initially, the attackers pose as prospective employers seeking to fill software developer roles. During the interview process, candidates are instructed to download and execute what appears to be a routine coding task from a GitHub repository.
This file, disguised as a ZIP archive containing an NPM package, houses an obfuscated JavaScript file (“imageDetails.js”) within the backend directory. Upon execution of the NPM package, the hidden JavaScript file triggers ‘curl’ commands through the Node.js process to fetch an additional archive (“p.zi”) from an external server.
 Obfuscated JavaScript
Obfuscated JavaScript
Securonix
Contained within this archive is the subsequent stage payload: an obfuscated Python script (“npl”) functioning as a RAT.
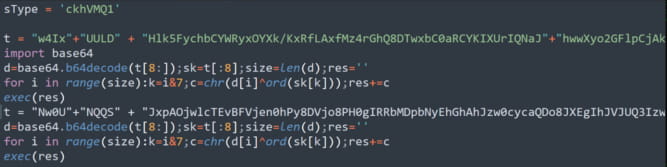 Python file contents
Python file contents
Securonix
Trending: Deep Dive to Fuzzing for Maximum Impact
Trending: OSINT Tool: Certina
Once active on the victim’s system, the RAT collects and transmits basic system information to the command and control (C2) server, including OS type, hostname, and network data.
RAT’s capabilities
The RAT boasts an array of capabilities:
- including persistent connections for ongoing control
- file system commands for data theft
- remote command execution
- direct FTP data exfiltration
- clipboard and keystroke logging.
While the perpetrators of the “Dev Popper” campaign remain unidentified, the tactic of exploiting job lures to propagate malware remains a prevalent threat. Developers are urged to remain vigilant against such risks.
The researchers highlight that this method exploits developers’ professional engagement and trust in the job application process, effectively leveraging the fear of compromising job opportunities to coerce compliance.
Notably, North Korean threat actors have a history of employing similar tactics, including the use of fake job offers to infiltrate various sectors, as evidenced in previous reports.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













