New DroidBot Malware Targets Cryptocurrency and Banking Apps in Europe
A new Android banking malware named DroidBot has surfaced, targeting credentials from over 77 cryptocurrency exchanges and banking apps across the UK, Italy, France, Spain, and Portugal.
Key Details
- Discovered by Cleafy researchers, DroidBot has been active since June 2024 and operates as a malware-as-a-service (MaaS) platform.
- Priced at $3,000 per month, DroidBot is being utilized by at least 17 affiliate groups, each customizing their payloads for specific regional and application targets.
- Despite lacking sophisticated features, DroidBot has already caused 776 unique infections across Europe and Turkey. Researchers believe the malware is still under heavy development, with plans to expand into Latin America.
DroidBot MaaS Operation
DroidBot’s creators, believed to be Turkish, provide affiliates with:
- Malware builders to create custom payloads.
- Command and Control (C2) infrastructure for managing attacks.
- A central administration panel for issuing commands and retrieving stolen data.
- Access to documentation, support, and updates via Telegram.
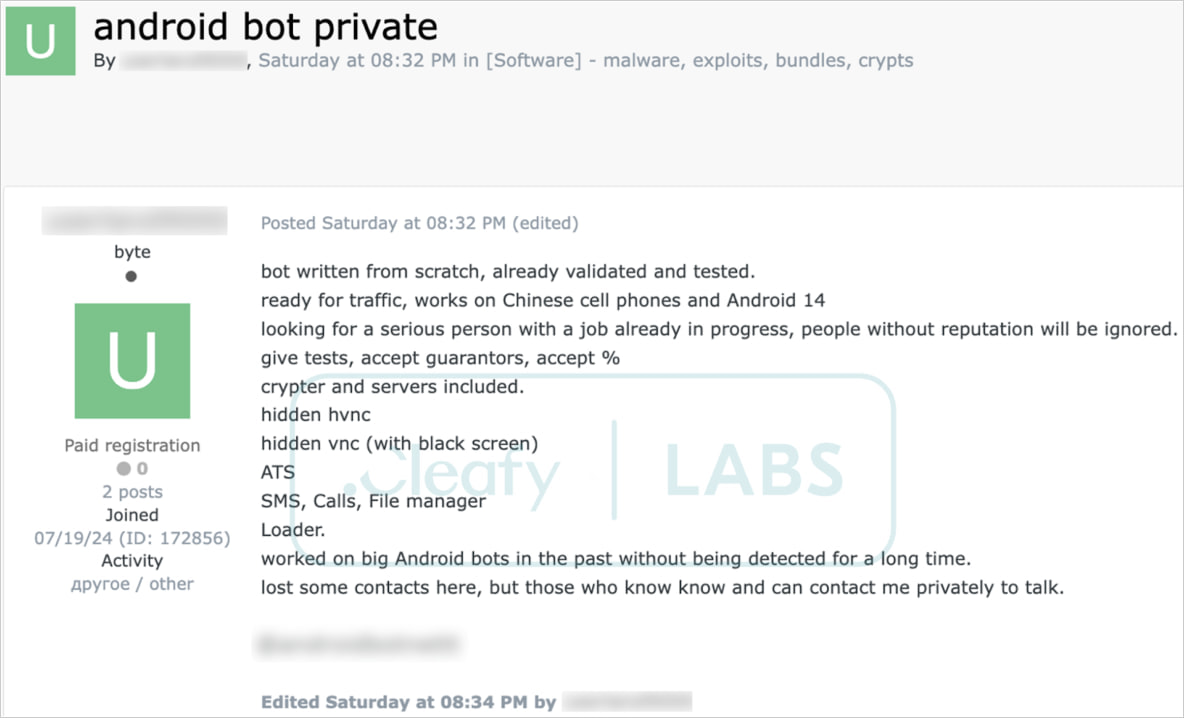 Creators claiming DroidBot works well on Android 14
Creators claiming DroidBot works well on Android 14
Source: Cleafy
Features for Affiliates
- Target customization (e.g., regional apps, language preferences).
- Detailed control through an admin panel.
- Support for inexperienced attackers, lowering the barrier for entry into cybercrime.
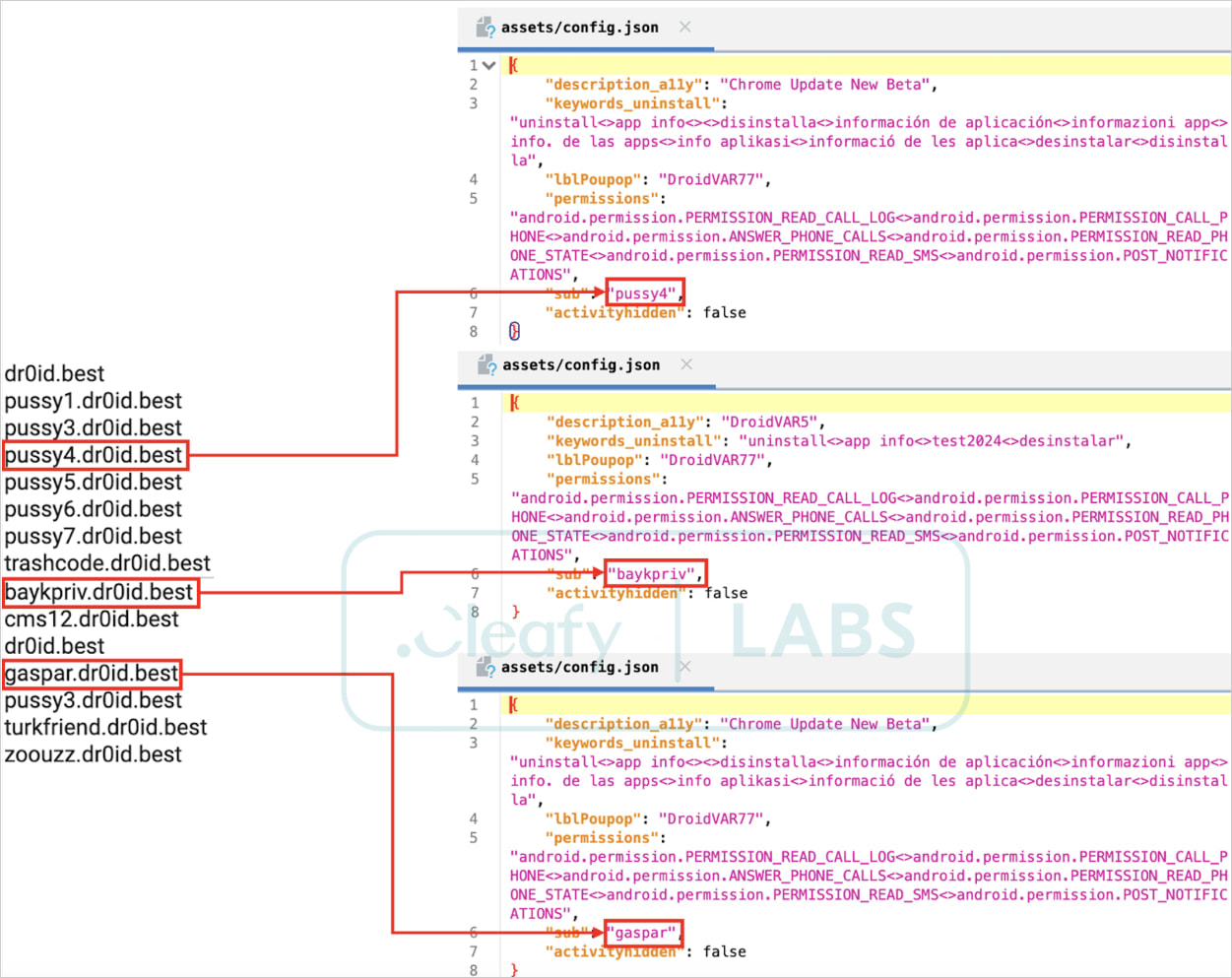 Affiliates extracted from the sample’s configuration
Affiliates extracted from the sample’s configuration
Source: Cleafy
Offensive Security, Bug Bounty Courses
Infection Techniques
DroidBot disguises itself as trusted apps like Google Chrome, Google Play Store, or Android Security, tricking users into installation. Once installed, the malware leverages Android’s Accessibility Services to monitor user actions and simulate device interactions.
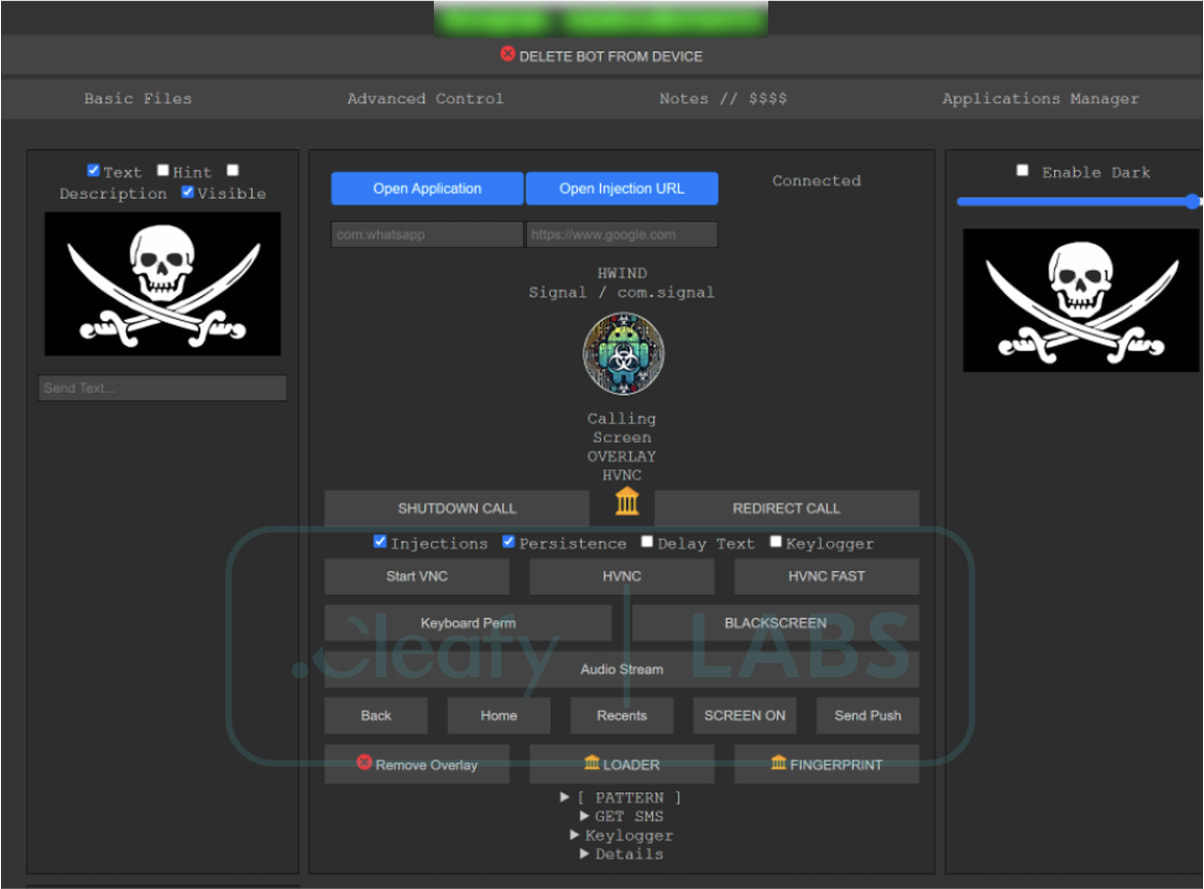 Admin panel giving affiliates complete control
Admin panel giving affiliates complete control
Source: Cleafy
Core Capabilities:
- Keylogging – Captures all keystrokes entered by victims.
- Overlaying – Displays fake login pages over legitimate banking apps to steal credentials.
- SMS Interception – Hijacks incoming SMS messages, including one-time passwords (OTPs).
- Remote Control – A Virtual Network Computing (VNC) module allows attackers to remotely view and control devices, execute commands, and even darken screens to conceal malicious activity.
Apps Targeted
Among the 77 apps DroidBot targets, prominent examples include:
- Cryptocurrency wallets: Binance, KuCoin, Metamask, Kraken.
- Banking apps: Santander, BBVA, Unicredit, BNP Paribas, Credit Agricole, Garanti BBVA.
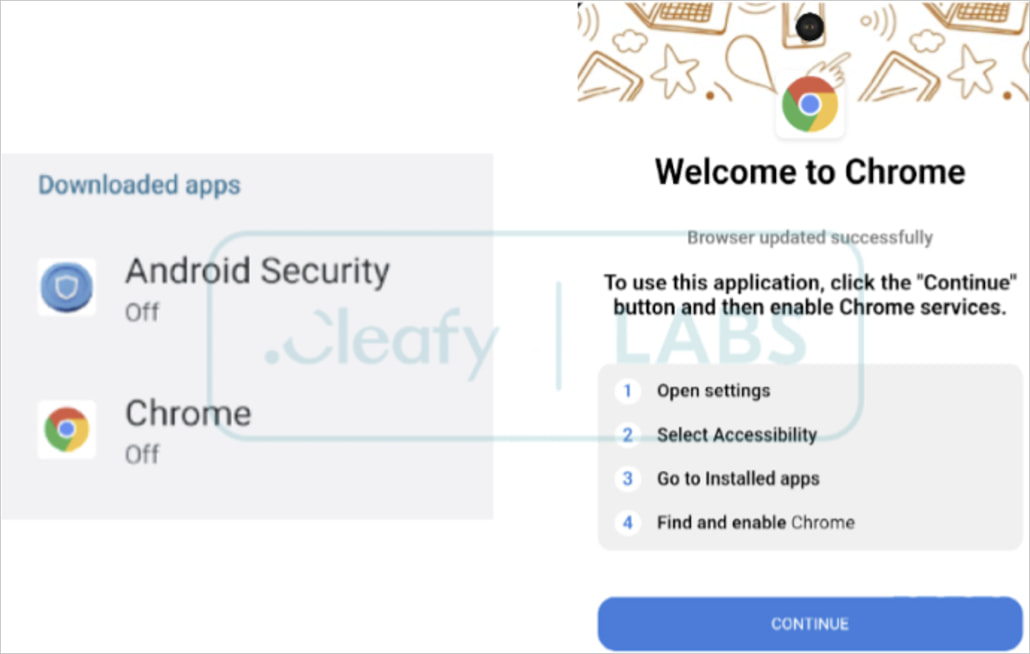 DroidBot’s masking apps
DroidBot’s masking apps
Source: Cleafy
Trending: Blue Team Tool: Ghostport
Mitigation Recommendations
To reduce the risk of DroidBot infections:
- Only download apps from official sources like Google Play.
- Review app permissions carefully, especially those requesting Accessibility Services.
- Enable Google Play Protect and ensure it remains active.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













