New generation of botnets builds high-performance VPS-based DDoS attacks

VPS-based botnets: the new threat landscape for DDoS attacks in 2023
Cloudflare, an internet security company, has reported that hyper-volumetric DDoS (distributed denial of service) attacks in Q1 2023 have shifted focus from compromised IoT devices to breached Virtual Private Servers (VPS). The new generation of botnets has gradually abandoned building large swarms of individually weak IoT devices and is now enslaving vulnerable and misconfigured VPS servers using leaked API credentials or known exploits. This shift allows threat actors to build high-performance botnets more easily and quickly, up to 5,000 times stronger than IoT-based botnets.
“Cloud computing providers offer virtual private servers to allow startups and businesses to create performant applications. The downside is that it also allows attackers to create high-performance botnets that can be as much as 5,000x stronger,” explains Cloudflare in their report. The company has been collaborating with cloud computing providers and partners to crack down on these emerging VPS-based threats and claims to have successfully taken down significant portions of these novel botnets.
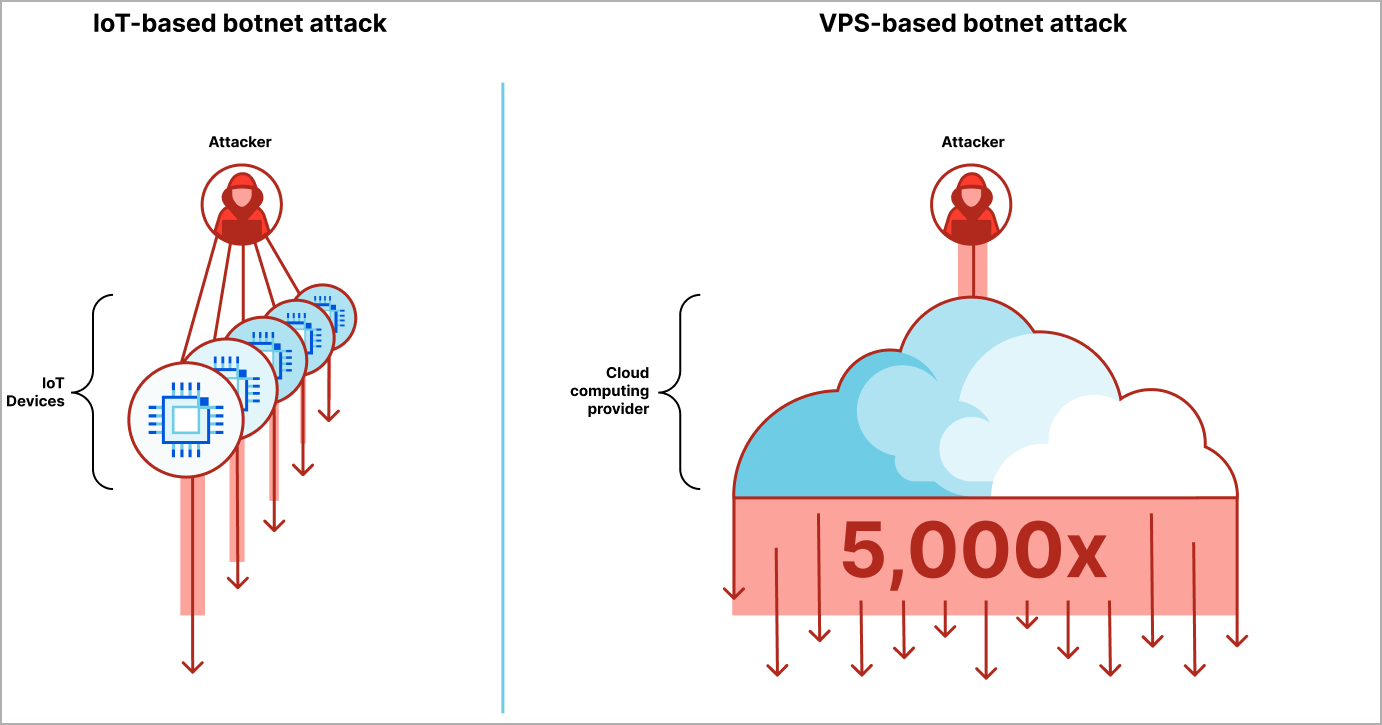 VPS servers used for DDoS attacks (Cloudflare)
VPS servers used for DDoS attacks (Cloudflare)
Offensive Security, Bug Bounty Courses
Ransom DDoS attacks increase by 60% YoY, with VPS-based botnets contributing to the rise
Cloudflare also reports steady DDoS activity in the first quarter of the year, with a 60% YoY increase in ransom DDoS attacks representing 16% of all recorded or reported DDoS attacks. These extortion-based DDoS attacks cause service outages to the target by bombarding them with garbage traffic and continue indefinitely until the victim meets the attacker’s demands.
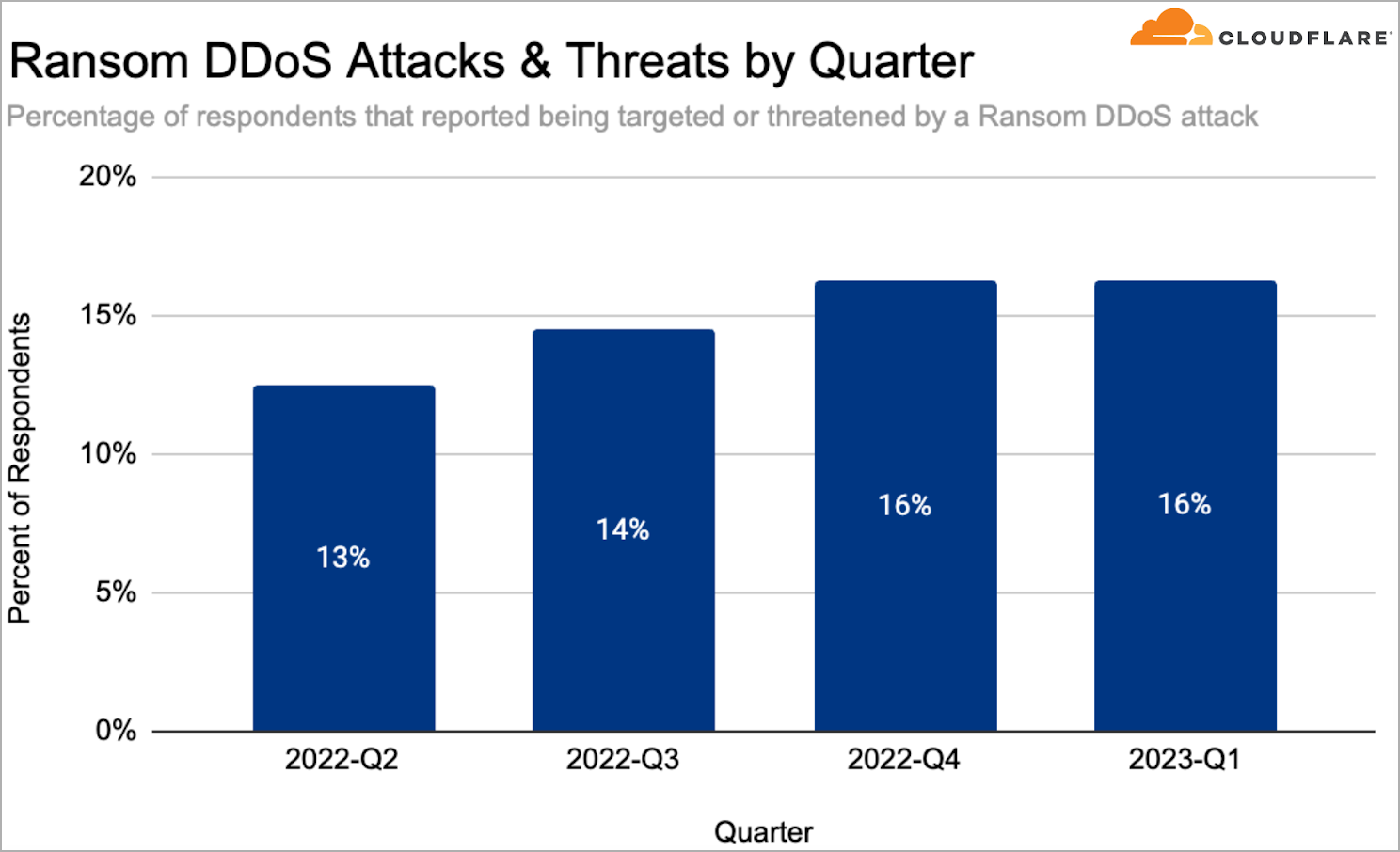 Ransom DDoS attacks (Cloudflare)
Ransom DDoS attacks (Cloudflare)
Although most attacks (86.6%) lasted for under 10 minutes, the number of larger attacks is still growing. Attacks surpassing 100 Gbps have recorded a rise of about 6.5% compared to the previous quarter.
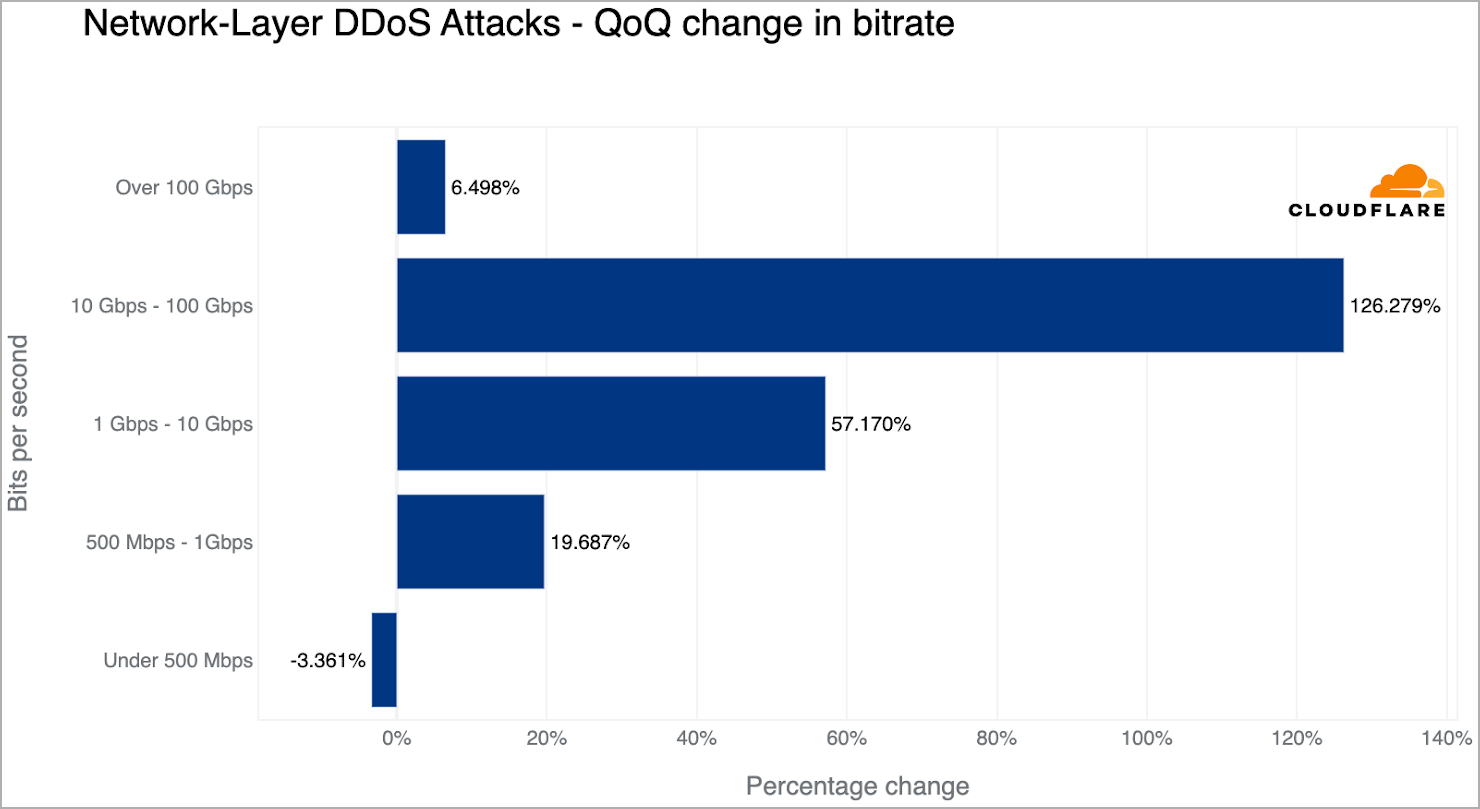 DDoS attack size trends (Cloudflare)
DDoS attack size trends (Cloudflare)
Cloudflare also recorded emerging trends in DDoS attacks during this quarter. There was a 1,565% QoQ increase in SPSS (statistical product and service solutions) based DDoS attacks fueled by the exploitation of two flaws (CVE-2021-22731 and CVE-2021-38153) in the Sentinel RMS License Manager service. Additionally, there was a 958% QoQ rise in DNS amplification DDoS attacks, where attackers exploit DNS infrastructure flaws to generate large amounts of traffic, and an 835% QoQ increase in GRE (generic routing encapsulation) based DDoS attacks, where attackers abuse the GRE protocol to flood the victim’s network with garbage requests.
Effective defense strategies for the evolving threat of DDoS attacks in 2023
Effective defense strategies require automated detection and mitigation solutions, as DDoS attacks in Q1 2023 show a trend of increasing in size and duration and are targeting a broad range of industries.
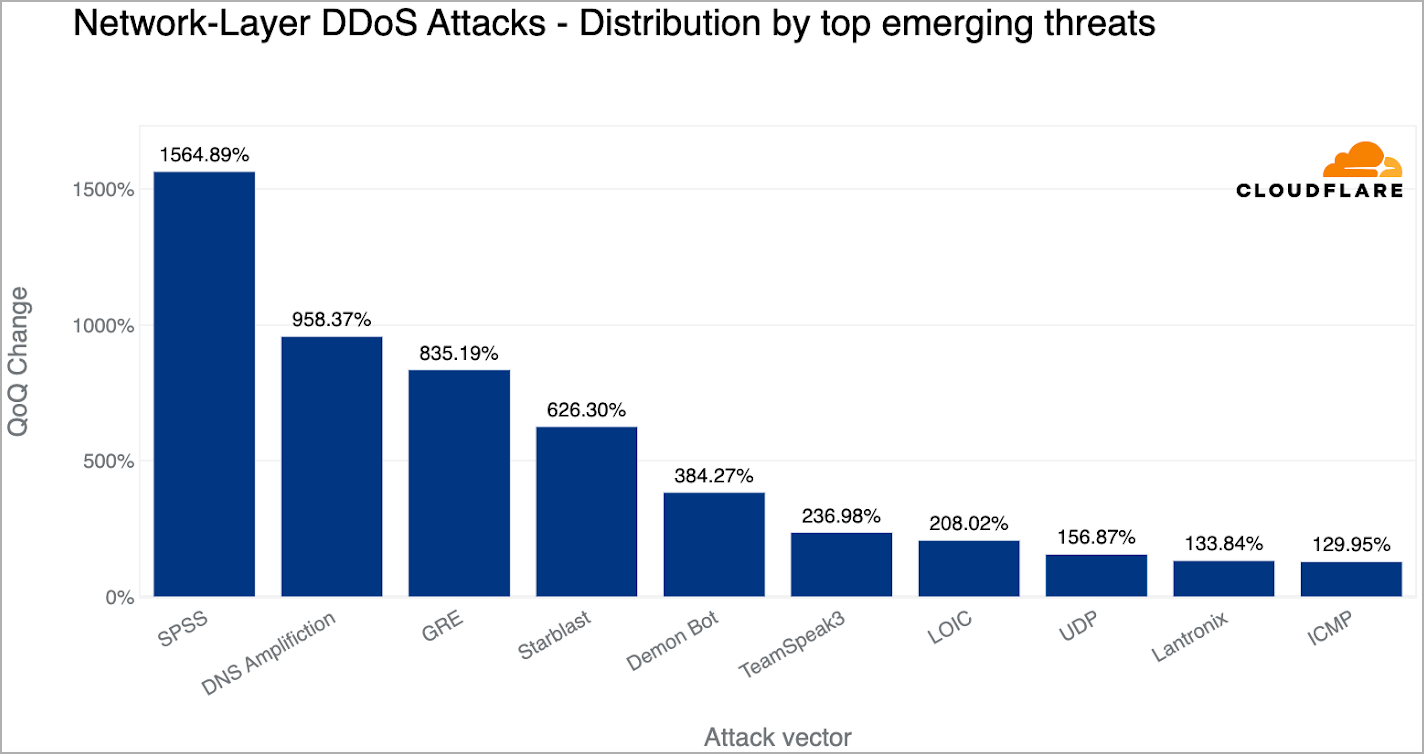 New DDoS attack trends (Cloudflare)
New DDoS attack trends (Cloudflare)
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












