New Ghost Tap Attack: The Next-Level Credit Card Scam Exploiting Apple Pay and Google Pay

Cybercriminals have devised a sophisticated scheme, dubbed ‘Ghost Tap,’ to exploit stolen credit card details linked to mobile payment systems like Apple Pay and Google Pay. This method leverages Near Field Communication (NFC) relays to enable global money mules to perform fraudulent transactions at Point-of-Sale (PoS) terminals.
Unlike previous attacks using the NGate malware, Ghost Tap eliminates the need for the victim’s device or continued interaction, making detection more challenging. Security firm Threat Fabric warns of a recent surge in Ghost Tap activity, with attackers coordinating large-scale fraudulent purchases.
 Threat actors looking for money mules on cybercrime forum
Threat actors looking for money mules on cybercrime forum
Source: Threat Fabric
How Ghost Tap Works
- Data Theft: Attackers steal card details and intercept one-time passwords (OTPs) through phishing, malware, or social engineering.
- Relay Mechanism: A relay server transmits the stolen payment credentials to a global network of money mules.
- Mule Operations: Mules use NFC-enabled devices to conduct PoS transactions, spreading activities across multiple locations to avoid detection.
This tactic contrasts with NGate attacks, where criminals relied on malware to guide victims into scanning their own NFC cards. Ghost Tap’s obfuscation methods make it harder to trace the fraud to its operators, leaving mules to face potential legal risks
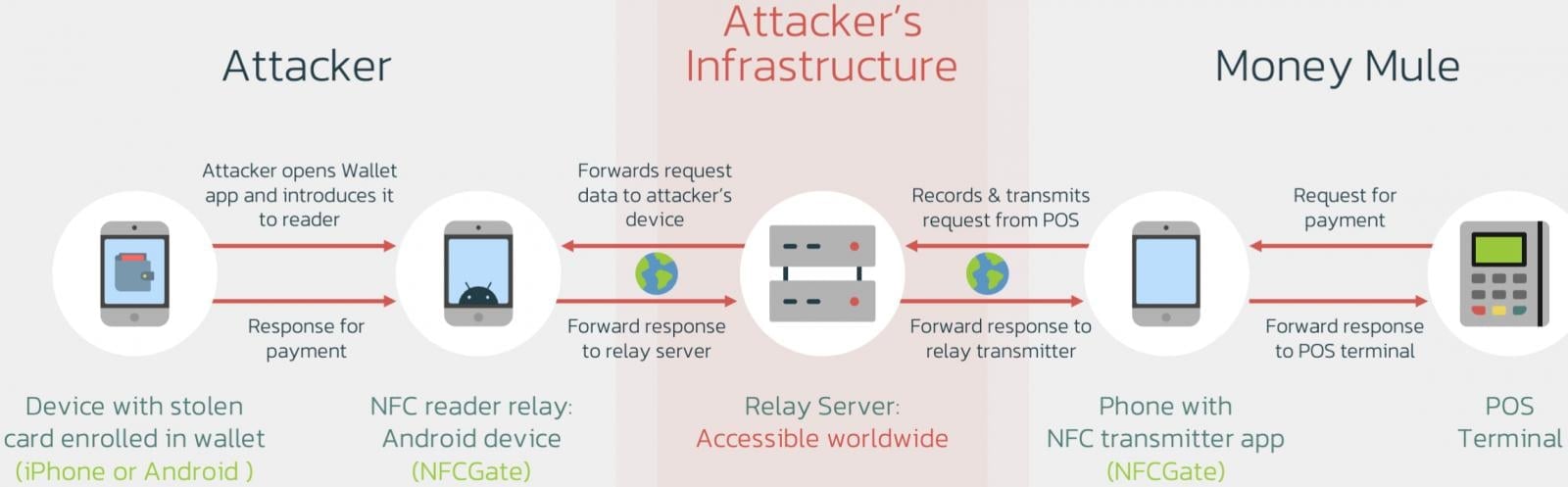 Overview of the Ghost Tap tactic
Overview of the Ghost Tap tactic
Source: Threat Fabric
Offensive Security, Bug Bounty Courses
Why Ghost Tap Is Hard to Detect
Ghost Tap bypasses many anti-fraud mechanisms by mimicking legitimate transactions and distributing small-scale purchases globally. Banks may struggle to flag these purchases, as the transactions often seem routine.
Attackers also exploit the ability to perform NFC payments in “airplane mode,” further complicating tracking efforts.
Protecting Against Ghost Tap
For financial institutions:
- Implement systems to flag geographically impossible transactions (e.g., purchases occurring in New York and Cyprus within minutes).
For consumers:
- Monitor accounts for unauthorized transactions.
- Report suspicious activity to banks immediately to block compromised cards.
As Ghost Tap gains traction, its impact on financial security could grow, making robust detection strategies crucial for institutions and users alike.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













