New Interlock Ransomware Exploits FreeBSD servers, Demanding Huge Ransoms

Interlock Ransomware: Targeting FreeBSD Servers in Critical Infrastructure
A new ransomware strain called Interlock is emerging as a significant threat, uniquely targeting FreeBSD servers, commonly found in critical infrastructure systems. Unlike the standard Linux-based encryptors, Interlock is one of the few ransomware operations specifically developing tools to target FreeBSD, following in the footsteps of the now-disrupted Hive ransomware.
Rising Threat of FreeBSD-Specific Attacks
Interlock, launched in late September 2024, has already targeted six organizations, publishing sensitive data on its leak site when ransom demands remain unpaid. One notable victim, Wayne County, Michigan, suffered an attack earlier in October, illustrating the potential for widespread service disruption and financial impact on vital systems.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Technical Aspects of Interlock Ransomware
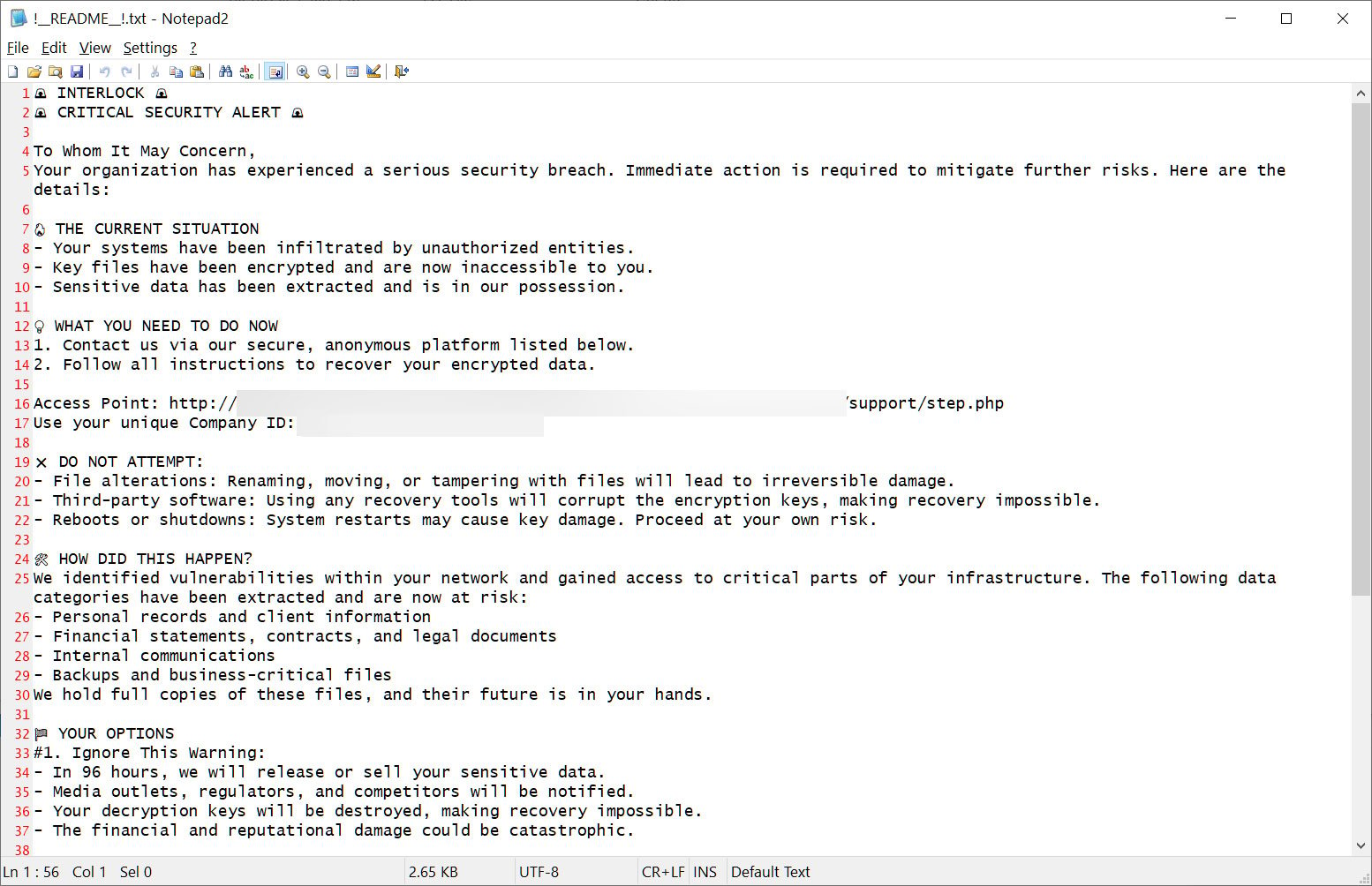 Interlock ransom note
Interlock ransom note
Source: BleepingComputer
Research from Trend Micro confirms that Interlock has created both FreeBSD and Windows encryptors. The FreeBSD encryptor, identified as a 64-bit ELF file, has sparked interest due to its specificity; FreeBSD is typically employed in sectors where security is paramount, such as energy and telecommunications infrastructure.
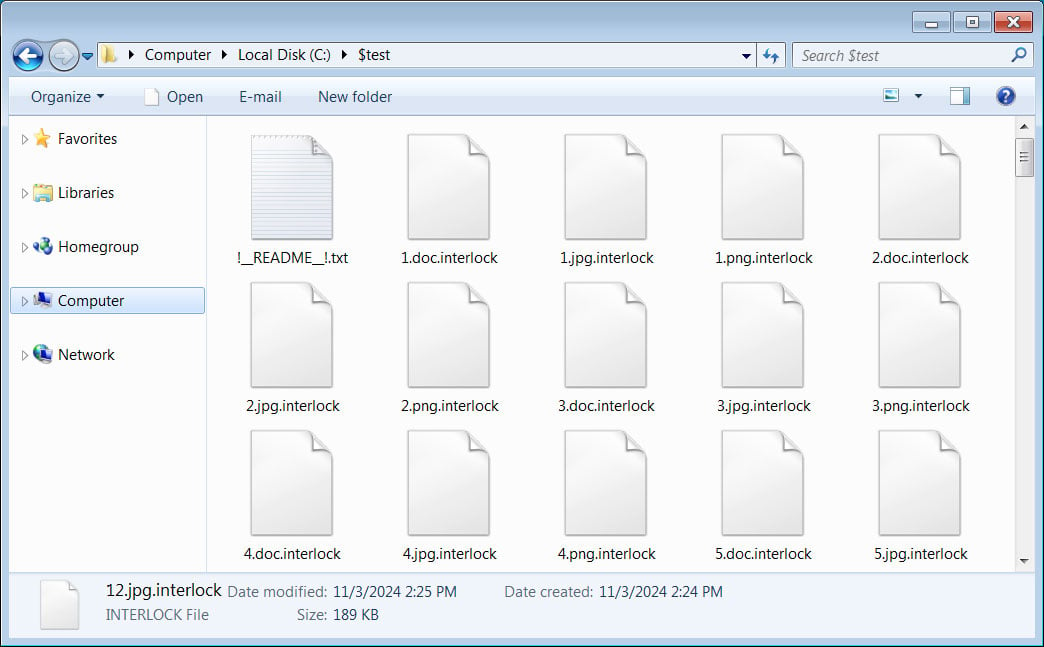 Files encrypted by Interlock
Files encrypted by Interlock
The ransomware uses a .interlock extension for encrypted files and delivers ransom notes across affected folders. Each note directs victims to a Tor-based negotiation platform featuring a chat system, where demands range from hundreds of thousands to millions of dollars, tailored to the victim’s profile.
Security Implications and Mitigations
Trend Micro attributes this unusual FreeBSD focus to the system’s extensive usage in mission-critical infrastructure, making it a prime target for cybercriminals seeking significant ransom payouts. The ransom note encourages quick payment with threats of data leakage on their site if demands are unmet. Furthermore, the Windows version of Interlock operates with efficiency, erasing Windows event logs and using DLL-based deletion tactics to obscure forensic traces.
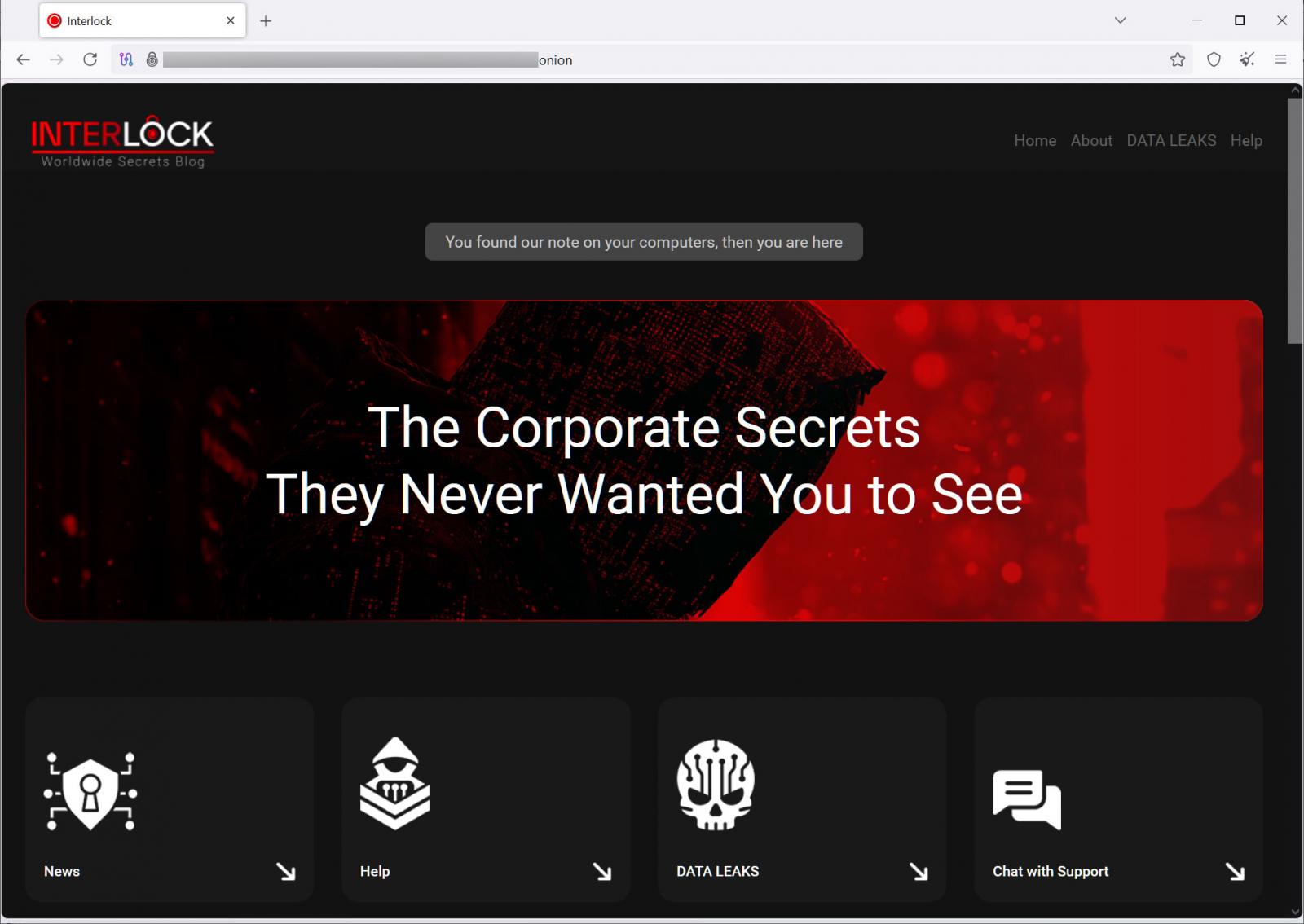 Interlock data leak site
Interlock data leak site
Source: BleepingComputer
Trending: Blue Team Tool: Ghostport
Growing Importance of Securing FreeBSD Systems
As ransomware tactics grow more sophisticated, Interlock’s targeting of FreeBSD points to a pressing need for security measures on FreeBSD servers. To reduce ransomware risks, organizations must implement multi-layered security protocols and prioritize patching vulnerabilities on any FreeBSD systems critical to their infrastructure.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













