New Linux Backdoor “Auto-color” Targets Government & Education Sectors

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
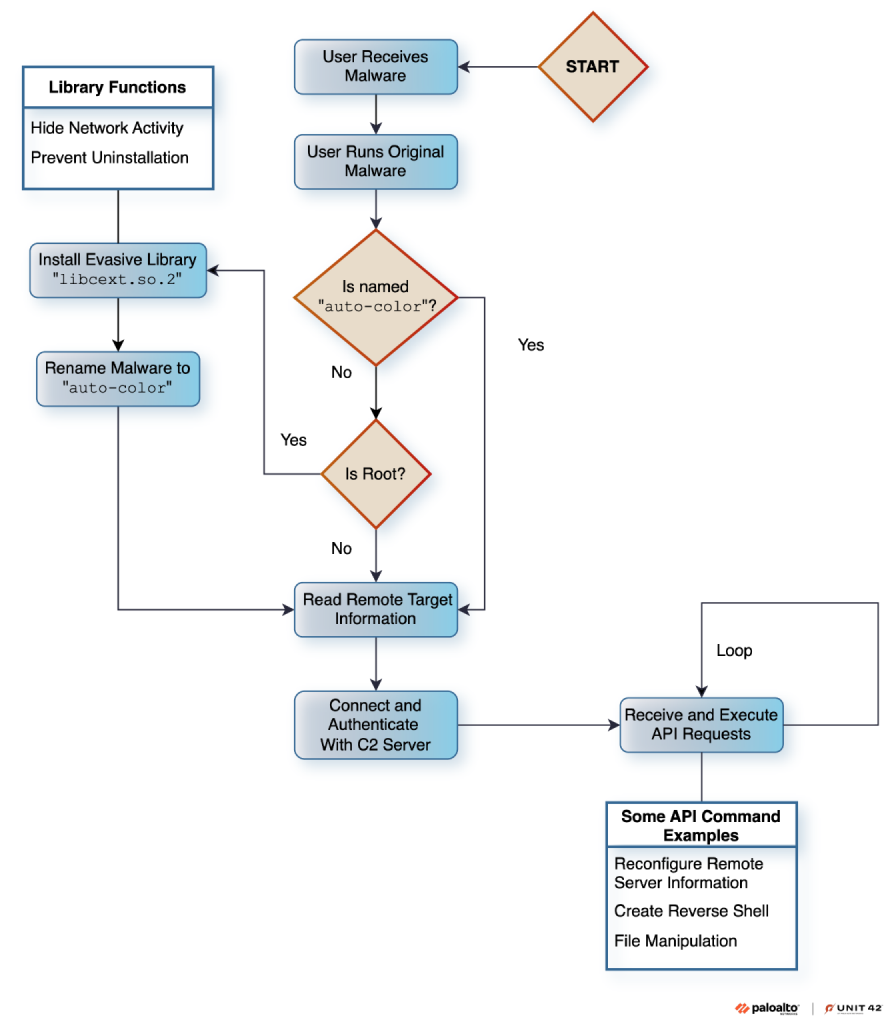
Why Auto-color Is Dangerous
✅ Evades Traditional Detection: Alters core Linux functions & hides network activity.
✅ Gains Deep System Control: Hooks into system processes for persistence.
✅ Encrypted Communication: Uses a custom stream cipher to avoid interception.
✅ Targets High-Value Sectors: Government & education institutions are primary targets.
Trending: Offensive Security Tool: HExHTTP
How to Protect Against Auto-color
🔒 Restrict Root Privileges: Limit admin access to prevent unauthorized modifications.
🛡️ Monitor ld.preload Changes: Watch for unexpected modifications to critical system libraries.
🔍 Inspect /proc/net/tcp Data: Look for inconsistencies in network connections.
📊 Enable Behavioral Threat Detection: Use EDR/XDR solutions to flag unusual system behavior.
🚨 Implement Continuous Linux Monitoring: Regularly audit system activity and network traffic.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: hackread.com