New macOS Malware ‘Atomic’ for Sale to Cybercriminals for $1,000 a Month

New ‘Atomic’ Malware Targets macOS Users for Information Theft and Cryptocurrency Fraud
A new strain of macOS malware is currently being offered for sale to cybercriminals via private Telegram channels. Named ‘Atomic’ aka ‘AMOS’, this malicious software is reportedly fetching a subscription of $1,000 per month from buyers interested in its information-stealing capabilities.
The Atomic malware arrives in the form of a DMG file containing a 64-bit Go-based application designed to target macOS systems. It is specifically intended to steal sensitive data from infected machines, including keychain passwords, files from the local filesystem, and various login credentials such as passwords, cookies, and credit card information that is stored in browsers.
Of particular note, the Atomic malware is designed to target over 50 different cryptocurrency extensions, making it a significant threat to cryptocurrency investors and traders. However, this is not the only data that it steals, as the malware is also capable of retrieving system information, model names, hardware UUIDs, RAM sizes, and serial numbers, among other sensitive data points.
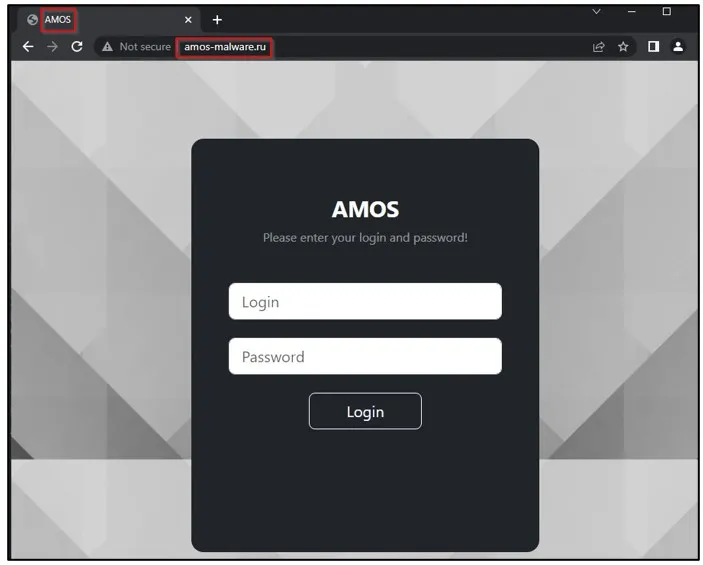 Atomic’s web panel (Cyble)
Atomic’s web panel (Cyble)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Atomic Malware for Sale on Telegram, Offers Comprehensive Data Theft Capabilities
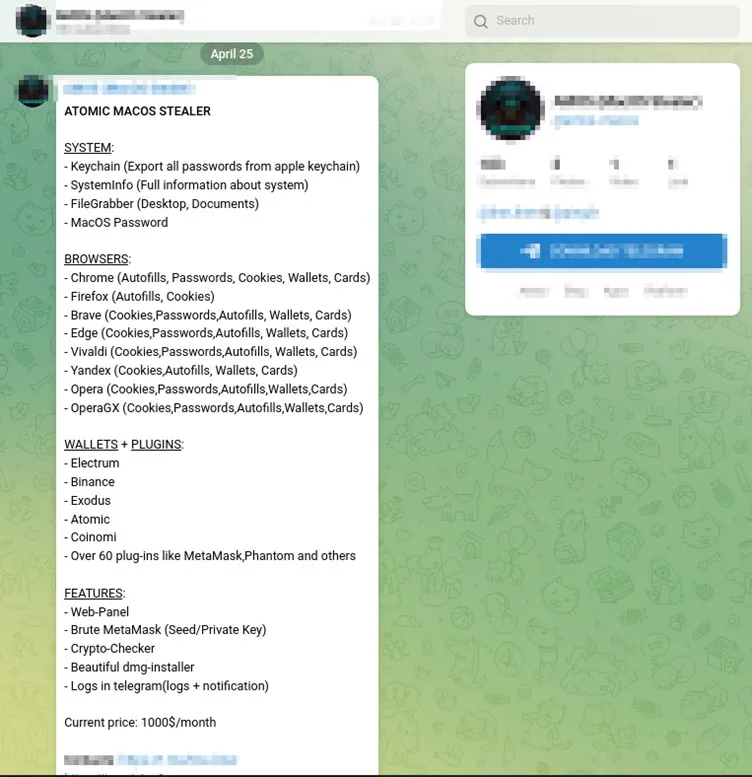 Latest version of the malware promoted on Telegram (Cyble)
Latest version of the malware promoted on Telegram (Cyble)
For the price, cybercriminals can also access a ready-to-use web panel for easy victim management, a MetaMask brute-forcer, a cryptocurrency checker, a dmg installer, and the ability to receive stolen logs via Telegram. The Atomic Stealer provides a comprehensive array of data-theft features, offering its operators enhanced opportunities to penetrate deeper into the target system.
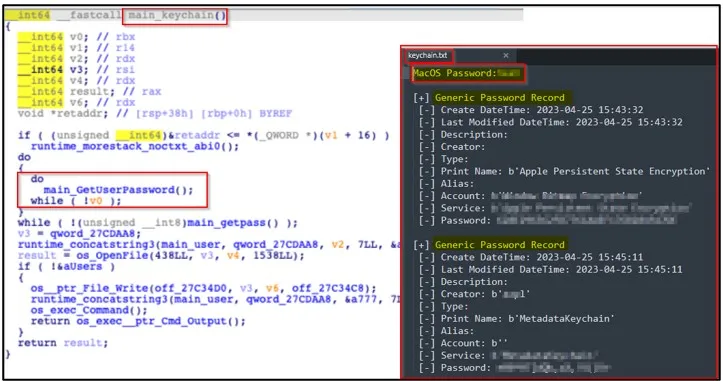 Extracting the Keychain password (Cyble)
Extracting the Keychain password (Cyble)
Although macOS is not typically at the epicenter of malicious info-stealer activity, like Windows, it is increasingly being targeted by threat actors of all skill levels. North Korean APT groups recently deployed a novel macOS info-stealer in the 3CX supply chain attack, illustrating that Macs are now a target for even state-sponsored hacking groups.
The Atomic malware was recently spotted by security researchers at Trellix and Cyble labs, who analyzed a sample of the malware and reported that the author released a new version on April 25, 2023, indicating that this is an actively developed project.
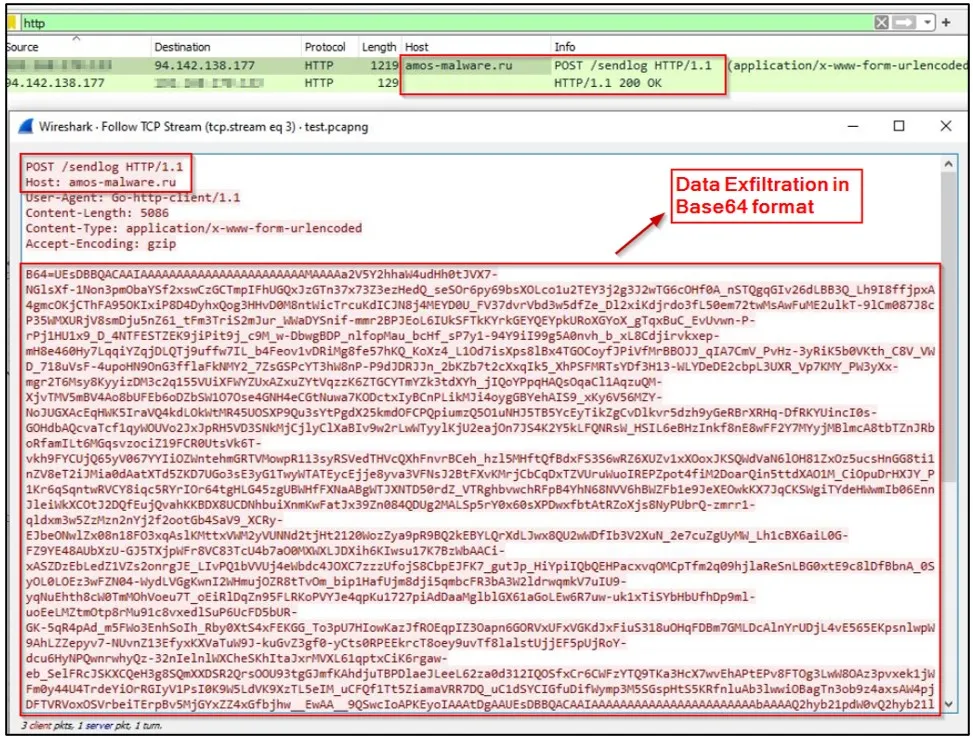 Exfiltrating the stolen data (Cyble)
Exfiltrating the stolen data (Cyble)
Trending: Major Cyber Attacks of 2022
Trending: Offensive Security Tool: dontgo403
Only one out of 59 AV engines flag Atomic on VirusTotal
At the time of writing, the malicious dmg file goes largely undetected on VirusTotal, where only one out of 59 AV engines flag it as malicious.
Buyers of the malware are responsible for setting up their own channels, which may include phishing emails, malvertizing, social media posts, instant messages, black SEO, laced torrents, and more.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












