New macOS Version of LightSpy Spyware Targets High-Value Data

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Targeted Exploits and Infection Method
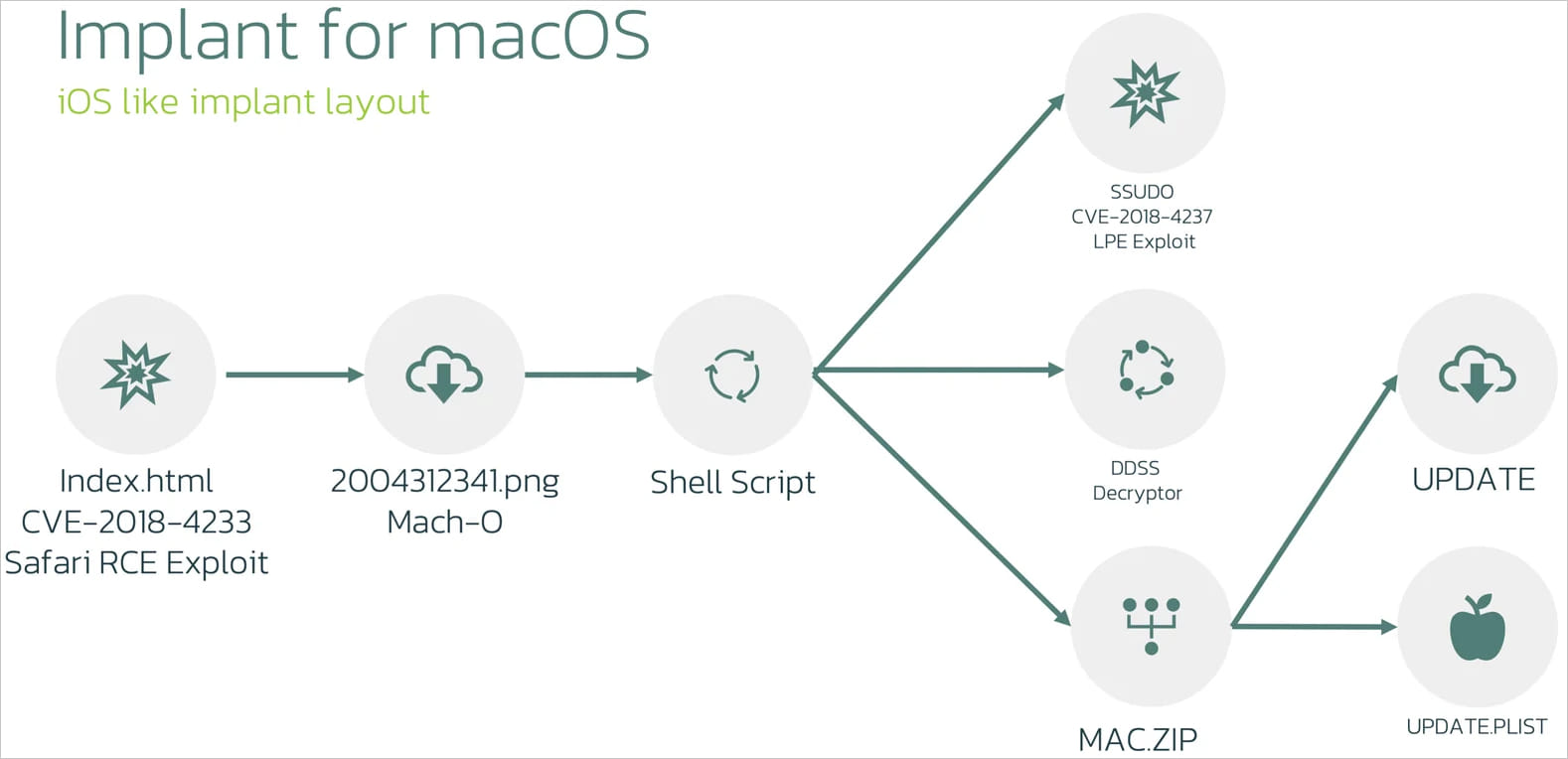
The macOS LightSpy variant exploits WebKit vulnerabilities CVE-2018-4233 and CVE-2018-4404 to gain code execution through Safari, targeting macOS 10.13.3 and earlier versions. Initially, a 64-bit MachO binary disguised as a PNG image file is delivered to the device. This binary decrypts and executes scripts to fetch a second-stage payload, which includes a privilege escalation exploit and additional tools.
Establishing Persistence and Data Exfiltration
Once on the device, LightSpy uses a series of scripts and executables to gain root access and establish persistence. The malware’s core component, “macircloader,” manages communications with the command and control (C2) server and coordinates the operation of various plugins. These plugins enable comprehensive data exfiltration from infected macOS systems.
Trending: OSINT Tool: SiteDorks
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com