New Malware ‘LOBSHOT’ Secretly Takes Over Windows Devices via Google Ads

Google Ads Used to Distribute LOBSHOT RAT
Security researchers have discovered a new remote access Trojan (RAT) named LOBSHOT being distributed via Google Ads. The ads, which promoted the legitimate AnyDesk remote management software, led users to a fake AnyDesk site at amydeecke[.]website. This site pushed a malicious MSI file that executed a PowerShell command to download a DLL from download-cdn[.]com, a domain previously associated with the TA505/Clop ransomware gang. However, it is unclear if TA505 is still using the domain as it had changed ownership in the past.
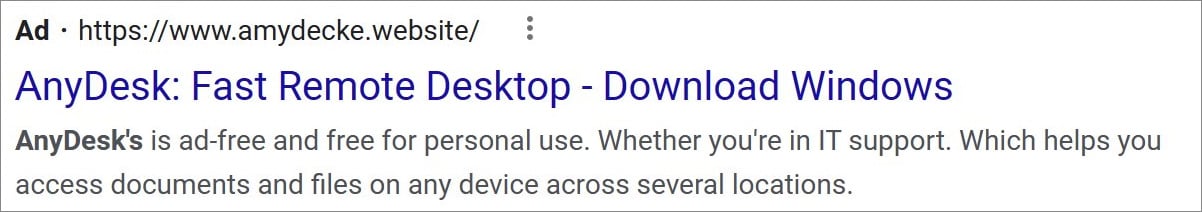 Fake AnyDesk ad spotted by Will Dormann
Fake AnyDesk ad spotted by Will Dormann
Source: MalwareHunterTeam & Dormann
Once executed, the LOBSHOT malware checks if Microsoft Defender is running, and if detected, terminates execution to prevent detection. If Defender is not detected, the malware configures Registry entries to start automatically when logging in to Windows and then transmits system information from the infected device, including running processes.
LOBSHOT malware is saved in the C:\ProgramData folder and then executed by RunDLL32.exe. The malware will also check for 32 Chrome cryptocurrency wallet extensions, nine Edge wallet extensions, and 11 Firefox wallet extensions. After enumerating the extensions, the malware will execute a file in C:\ProgramData. However, as that file did not exist in their analysis, researchers are unsure whether it is used to steal the extension data or for some other purpose.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
LOBSHOT Malware Includes hVNC Module for Remote Access Control
Elastic Security Labs, the researchers who discovered the malware, found that LOBSHOT included an hVNC module, allowing the threat actors to access an infected device remotely. hVNC, or hidden virtual network computing, is a VNC remote access software modified to control a hidden desktop on the infected device, rather than the main desktop used by the device’s owner. This allows a threat actor to remotely control a Windows desktop computer without the victim knowing it is happening.
LOBSHOT deploys an hVNC module that allows the threat actors to control the hidden desktop using their mouse and keyboard as if they were in front of it. With this kind of access, the threat actors have complete control over the device, allowing them to execute commands, steal data, and even deploy further malware payloads. As AnyDesk is commonly used in business environments, the malware is likely used for initial access to corporate networks and to spread laterally to other devices.
Trending: Offensive Security Tool: Go365
Rising trend of malware distribution through Google Ads
This type of access could lead to ransomware attacks, data extortion, and other attacks. The discovery of LOBSHOT highlights the growing trend of threat actors utilizing Google Ads to distribute malware in search results. In fact, earlier this year, BleepingComputer and numerous cybersecurity researchers reported a dramatic increase in threat actors using Google Ads to distribute malware. These advertising campaigns impersonated popular websites for various applications but instead pushed malware, including Gozi, RedLine, Vidar, Cobalt Strike, SectoRAT, and the Royal Ransomware.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












