New Neptune RAT Variant Spreads via YouTube and Telegram, Targets Windows Users

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Notable Capabilities of Neptune RAT
🟩 Credential Theft & Clipboard Hijacking
Steals passwords from browsers and applications, and silently replaces copied crypto wallet addresses with the attacker’s wallet.
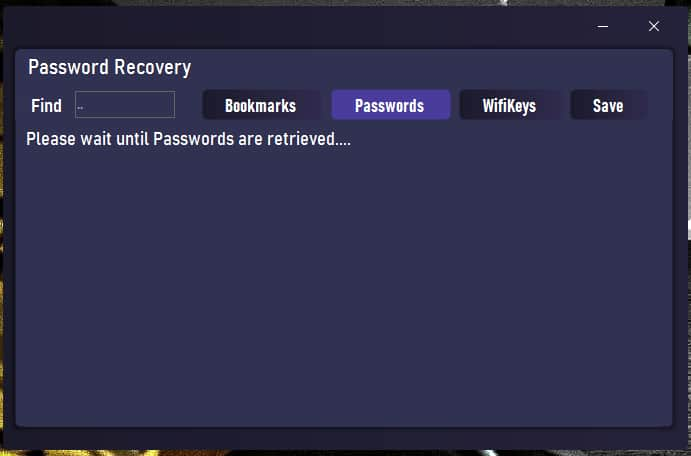 Screenshot from NaptuneRAT’s official website (Credit: Hackread.com)
Screenshot from NaptuneRAT’s official website (Credit: Hackread.com)
🟩 Ransomware Deployment
Encrypts victim files, appending .ENC extensions and dropping an HTML ransom note. Can also corrupt the Master Boot Record (MBR), rendering the system unbootable.
🟩 Persistence & Evasion
Creates scheduled tasks and modifies the Windows Registry
Detects virtual machines to avoid analysis
Uses separate DLL modules to expand functionality, including:
Live screen viewing
Email and browser data extraction
User account control bypassing
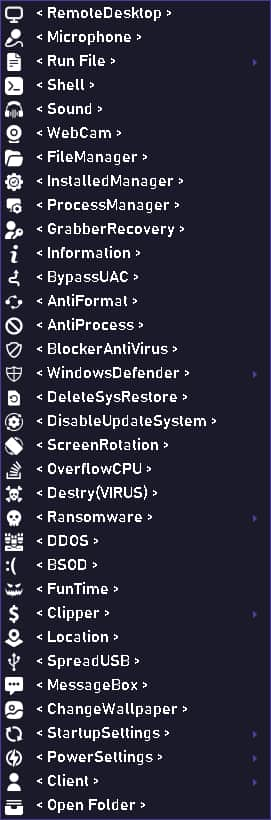 Screenshot from NaptuneRAT’s official website shows the full list of its capabilities (Credit: Hackread.com)
Screenshot from NaptuneRAT’s official website shows the full list of its capabilities (Credit: Hackread.com)
Expert Analysis: A Serious Threat Masquerading as “Educational Software”
Satish Swargam, Principal Security Consultant at Black Duck, warns that Neptune RAT is:
“…capable of launching ransomware, hijacking crypto wallets, and spying on users in real time. It bypasses typical security tools by blending into platforms like GitHub and YouTube.”
Swargam emphasizes the need for strong endpoint monitoring and active threat detection, especially as cybercriminals increasingly disguise malware as educational tools.
Trending: Offensive Security Tool: CTFPacker
How to Protect Against Neptune RAT
✅ Avoid downloading software or scripts from unverified YouTube or Telegram sources
✅ Keep Windows and antivirus software updated
✅ Use behavioral monitoring tools to detect unusual script or registry activity
✅ Implement application whitelisting and disable unnecessary PowerShell execution
✅ Back up important data regularly and store it offline
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: hackread.com













