New Phishing Campaign Exploits Microsoft Teams to Deliver DarkGate Loader Malware

A phishing campaign has been detected that leverages Microsoft Teams messages to distribute malicious attachments, ultimately installing the DarkGate Loader malware. This campaign was first observed in late August 2023 when phishing messages posing as Microsoft Teams communications were sent from two compromised external Office 365 accounts to organizations.
The attackers behind this campaign employed these compromised accounts to deceive Microsoft Teams users into downloading and opening a ZIP file named “Changes to the vacation schedule.” Once the unsuspecting victim clicks on the attachment, it triggers the download of the ZIP file from a SharePoint URL. Inside the ZIP file, there’s an LNK file cleverly disguised as a PDF document.
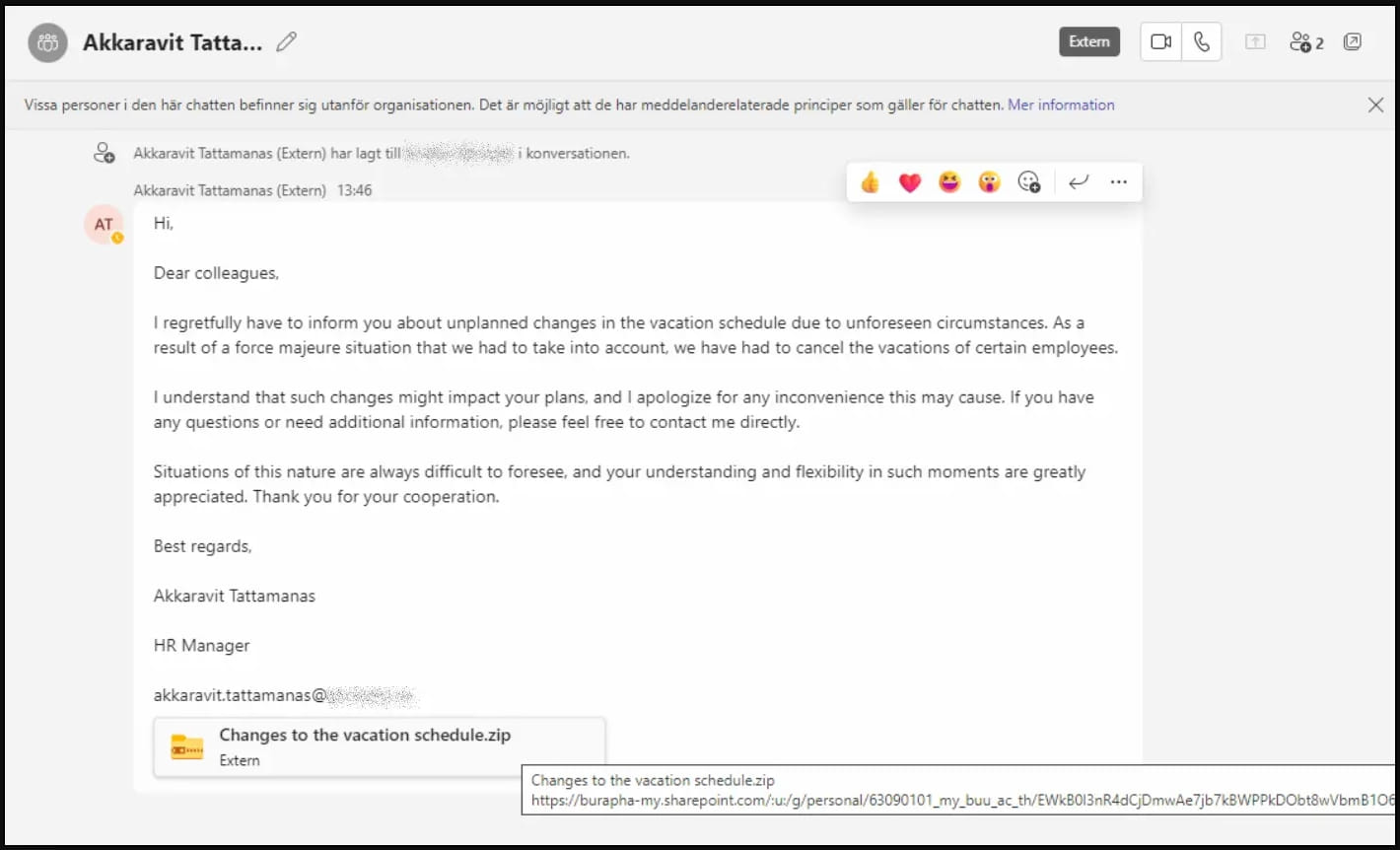 Phishing message sent to targets (Truesec)
Phishing message sent to targets (Truesec)
Security experts at Truesec conducted an analysis of this Microsoft Teams phishing campaign and discovered that it contains a malicious VBScript. This VBScript initiates an infection chain leading to the deployment of DarkGate Loader, a notorious malware strain.
To evade detection, the download process employs Windows cURL to fetch the executable and script files required for the malware. The script is obfuscated and comes pre-compiled, with its malicious code concealed within the file, beginning with distinguishable “magic bytes” associated with AutoIT scripts.
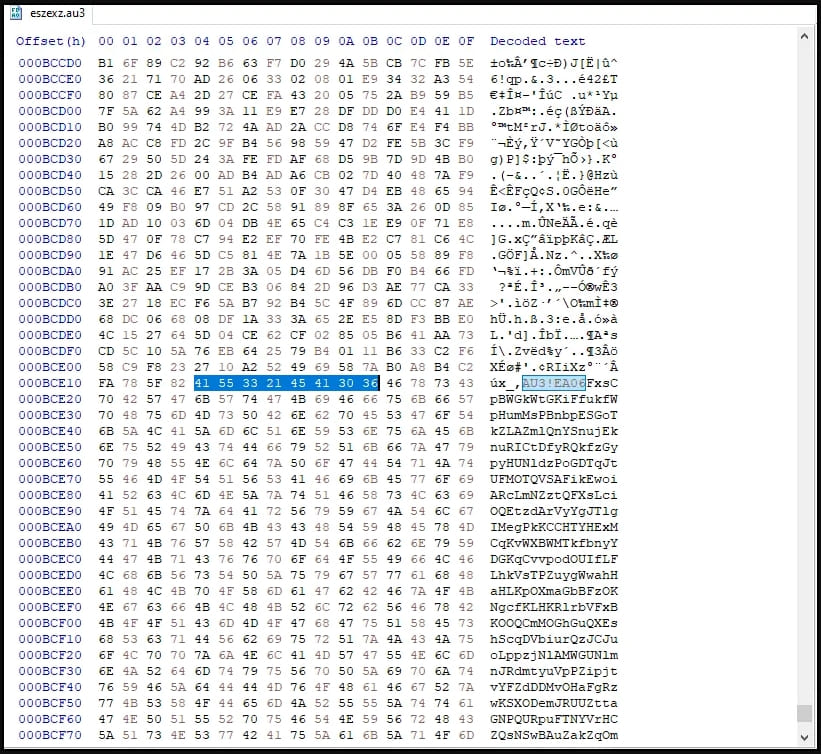 Magicbytes section in the malicious script (Truesec)
Magicbytes section in the malicious script (Truesec)
It’s noteworthy that this script checks for the presence of Sophos antivirus software on the targeted machine. If Sophos is not detected, it proceeds to deobfuscate additional code and triggers the execution of shellcode.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The shellcode utilizes a technique known as “stacked strings” to construct the DarkGate Windows executable and loads it into the computer’s memory.
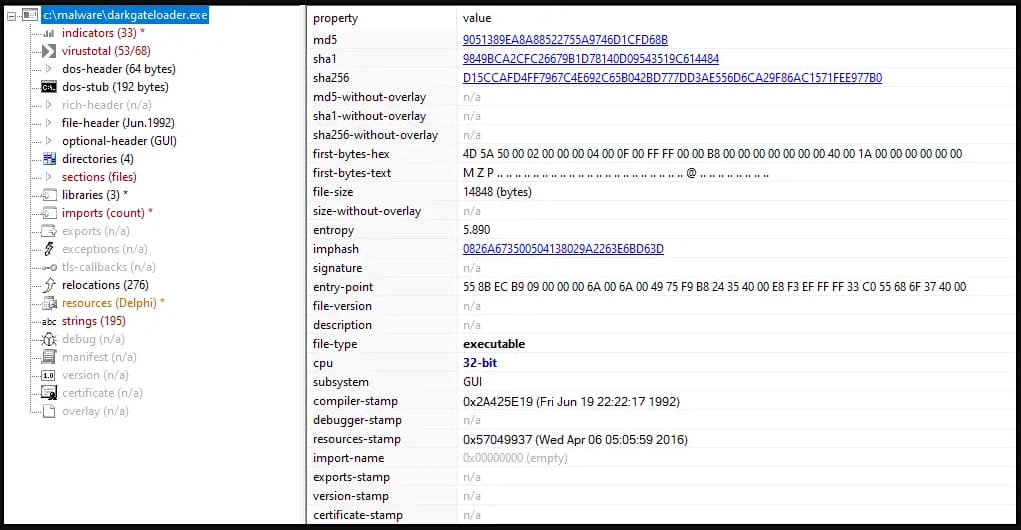 Payload details (Truesec)
Payload details (Truesec)
Microsoft Teams phishing
This campaign is an example of Microsoft Teams phishing, which was previously demonstrated in a June 2023 report by Jumpsec. The method involves sending malicious messages to other organizations through phishing and social engineering, much like what was observed in this attack. Despite concerns raised earlier, Microsoft has yet to address this risk comprehensively. Instead, it recommends administrators implement secure configurations such as narrow-scoped allow-lists and disabling external access if communication with external tenants is unnecessary.
While a tool released by a Red Teamer in July 2023 streamlined this Microsoft Teams phishing attack method, there’s no direct indication that it played a role in the recent campaign.
DarkGate, the malware at the center of this attack, has been in circulation since 2017, primarily used by a select group of cybercriminals against specific targets. It is a versatile malware capable of various malicious activities, including hVNC for remote access, cryptocurrency mining, reverse shell, keylogging, clipboard data theft, and information exfiltration (including files and browser data).
Trending: OSINT Tool: Photon
In June 2023, ZeroFox reported an attempt by someone claiming to be the original author of DarkGate to sell access to the malware to a select group of individuals for a significant sum. Subsequently, there have been reports of an increase in DarkGate distribution through various channels, including phishing and malvertising.
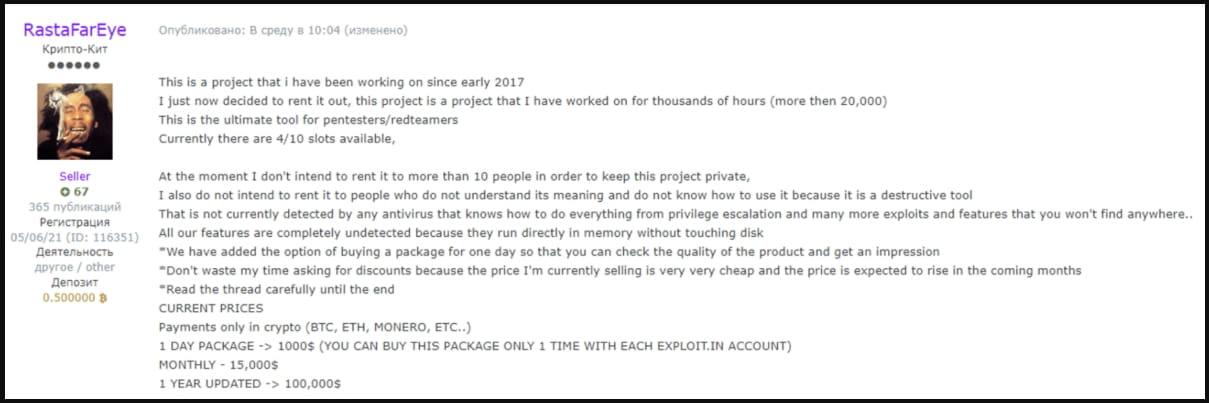 Forum post about DarkGate (ZeroFox)
Forum post about DarkGate (ZeroFox)
While DarkGate may not be considered a widespread threat at present, its expanding targeting strategies and adoption of multiple infection vectors make it an emerging threat that should be closely monitored by the cybersecurity community.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












