New QR Code Phishing Campaign Leverages Microsoft Sway Infrastructure

Cybersecurity researchers have identified a new phishing campaign, often referred to as “quishing,” that uses QR codes to direct victims to malicious websites. The campaign stands out by exploiting Microsoft Sway, a legitimate cloud-based tool for creating presentations and documents, to host fake pages that aim to steal Microsoft 365 credentials. The use of Microsoft Sway infrastructure adds credibility to the phishing attempts, making them more convincing to victims.
Key Findings
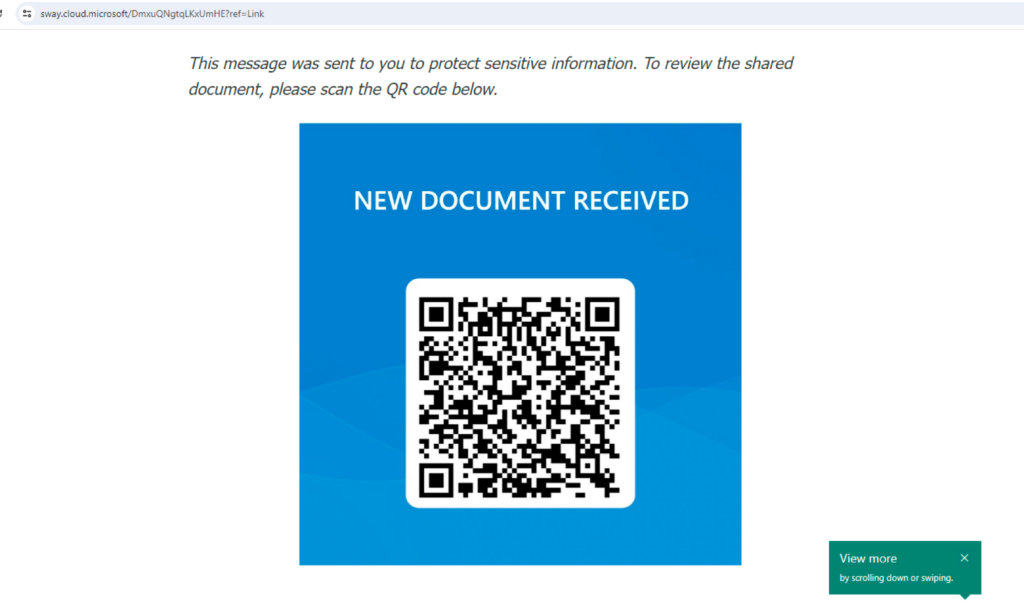
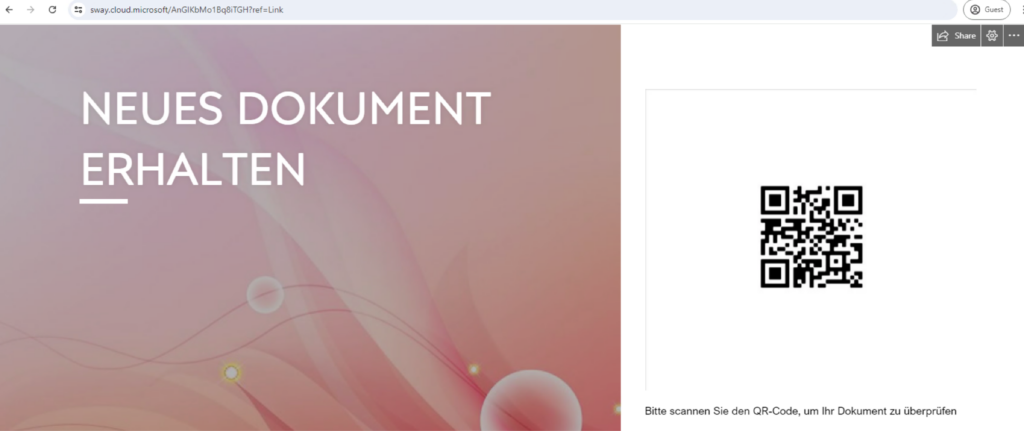
Exploitation of Microsoft Sway: Attackers are hosting phishing pages on Microsoft Sway, capitalizing on the trust that users place in Microsoft services. Since Sway is part of the Microsoft 365 suite, users are more likely to believe the content is legitimate, especially when they are already logged into their Microsoft 365 accounts.
Quishing Tactics: The phishing campaign primarily uses QR codes hosted on Sway. When scanned, these QR codes redirect victims to phishing websites designed to capture their Microsoft 365 login credentials. This method bypasses traditional email scanners that focus on text content since the malicious URLs are embedded within the QR codes.
Targeted Regions and Sectors: The campaign has primarily targeted users in Asia and North America, with the technology, manufacturing, and finance sectors being the most frequently targeted industries.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
4. Sophisticated Techniques:
- Cloudflare Turnstile: Some phishing campaigns use Cloudflare Turnstile to hide their domains from static URL scanners, making detection more difficult.
- Adversary-in-the-Middle (AitM) Phishing: Attackers are employing AitM tactics to capture credentials and two-factor authentication (2FA) codes in real-time. This technique uses lookalike login pages to trick victims into entering their credentials, which are then used to log them into the service, further enhancing the illusion of legitimacy.
5. Challenges in Detection:
- QR Code Embedded URLs: The use of QR codes poses a significant challenge to defenders because the malicious URLs are embedded within images, which are harder to scan and analyze than plain text.
- Mobile Device Vulnerability: Many users scan QR codes with mobile devices, which often have less stringent security measures compared to desktops and laptops, making them more susceptible to phishing attacks.
6. Unicode QR Code Phishing: In a new twist, attackers have begun crafting QR codes using Unicode text characters instead of images. This method presents a significant challenge for conventional security measures as it bypasses detections designed to scan for suspicious images.
Trending: Digital Forensics Tool: Horus
Historical Context
This is not the first time phishing attacks have abused Microsoft Sway. In April 2020, a campaign known as PerSwaysion targeted high-ranking officers at various firms by using Sway to redirect victims to credential harvesting sites. This current wave of attacks shows that the abuse of legitimate cloud services like Microsoft Sway continues to be an effective strategy for cybercriminals.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com













