New RAMBO Attack Extracts Secrets from Air-Gapped Systems via Electromagnetic Signals

A newly discovered side-channel attack, dubbed RAMBO (Radiation of Air-gapped Memory Bus for Offense), enables attackers to extract data from air-gapped computers by generating electromagnetic radiation from the device’s RAM.
Air-Gapped Systems at Risk
Air-gapped systems, typically used in high-security environments such as government, military, and nuclear facilities, are isolated from the internet and other networks to prevent malware infections and data theft. Despite their isolation, they remain vulnerable to malware introduced through physical means like USB drives or sophisticated supply chain attacks by state actors.
Once compromised, malware can remain dormant and covertly manipulate RAM components to transmit sensitive data to a nearby receiver.
How the RAMBO Attack Works
The RAMBO attack begins with malware planted on the air-gapped system. The malware manipulates memory access patterns (read/write operations) to create controlled electromagnetic emissions from the RAM. These emissions, caused by the rapid switching of electric signals within the RAM, are not actively monitored by security products and go undetected.
The data is encoded into binary form, using On-Off Keying (OOK) for modulation. In this process, “1” is represented by the presence of an electromagnetic signal, and “0” by its absence. The researchers used Manchester code to ensure accurate transmission and reduce errors.
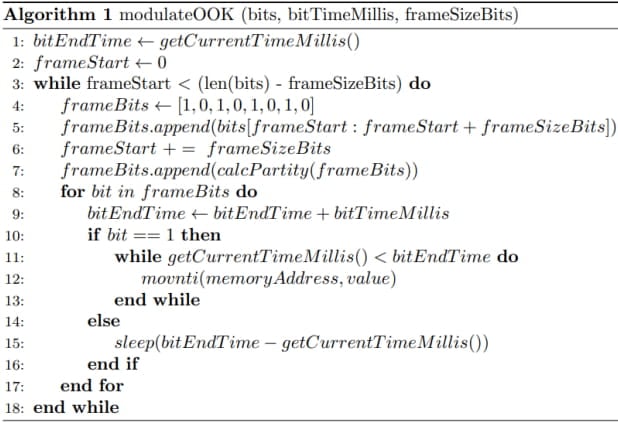 Code to perform the OOK modulation
Code to perform the OOK modulation
Source: Arxiv.org
A nearby attacker can then intercept these emissions using a simple Software-Defined Radio (SDR) equipped with an antenna, allowing them to recover and interpret the transmitted data.
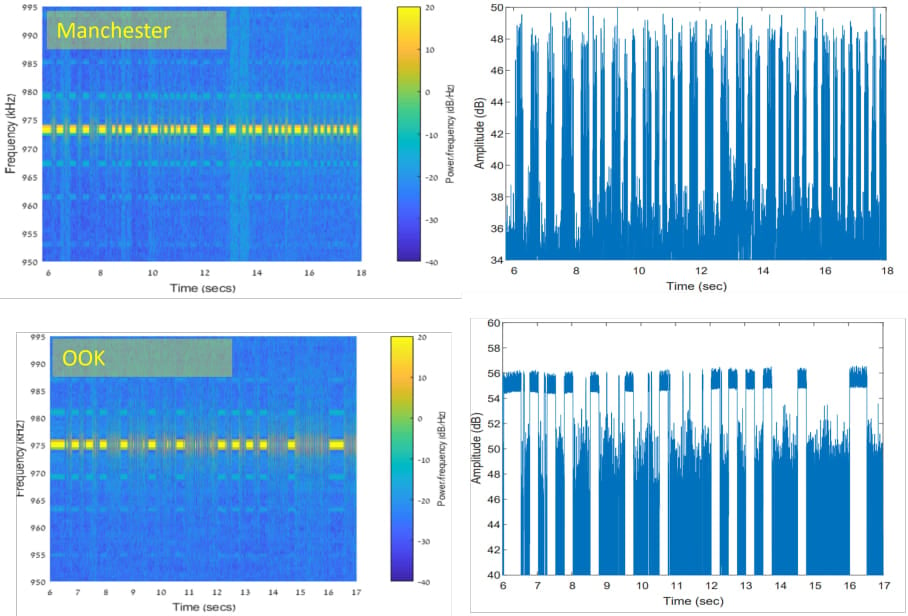 EM signal of the word “DATA”
EM signal of the word “DATA”
Source: Arxiv.org
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Performance and Range
The RAMBO attack can achieve data transfer rates of up to 1,000 bits per second (bps), equivalent to 128 bytes per second. While this limits large-scale data theft, it is sufficient for exfiltrating sensitive information such as passwords, keystrokes, or encryption keys.
For instance:
- Keylogging can be performed in real-time.
- Stealing passwords takes 0.1 to 1.28 seconds.
- Exfiltrating a 4096-bit RSA key takes 4 to 42 seconds.
- Small images can be transmitted in 25 to 250 seconds.
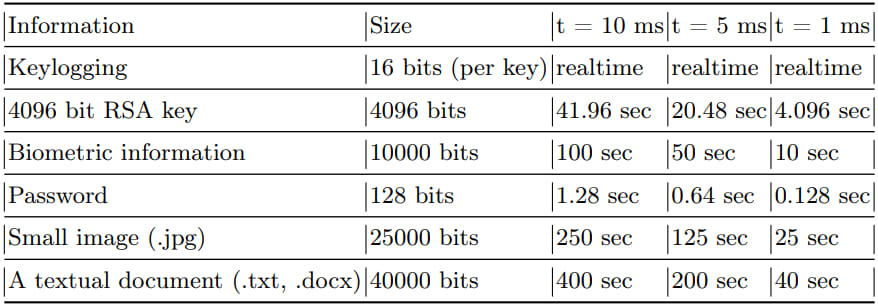 Data transmissions speeds
Data transmissions speeds
Source: Arxiv.org
The attack is most effective within a maximum range of 300 cm (10 ft) with a bit error rate of 2-4%. At slower transmission speeds, it can reach up to 7 meters (23 ft) with nearly zero errors.
Trending: Recon Tool: FinalRecon
Mitigation and Prevention
Several defense strategies are recommended to mitigate RAMBO and similar electromagnetic-based attacks:
- Physical zone restrictions to prevent unauthorized access.
- RAM jamming to disrupt covert channels at the source.
- External electromagnetic jamming to disrupt the transmission of signals.
- Faraday enclosures to block electromagnetic emissions from air-gapped systems.
While these countermeasures are effective, they introduce additional overhead and complexity to the system.
Effectiveness Against Virtual Machines
The researchers tested the RAMBO attack on processes running inside virtual machines and found that it remained functional. However, interference from the host operating system or other virtual machines could disrupt the attack over time.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













