New RansomHouse Tool ‘MrAgent’ Streamlines Ransomware Attacks on VMware ESXi Hypervisors
The RansomHouse ransomware operation has unveiled a new tool called ‘MrAgent,’ designed to streamline the deployment of its data encrypter across multiple VMware ESXi hypervisors. RansomHouse, a ransomware-as-a-service (RaaS) operation known for its double extortion tactics, has been targeting large organizations since its emergence in December 2021.
Targeting ESXi Servers:
Ransomware groups often target ESXi servers due to their deployment of virtual computers containing valuable data, such as critical applications and services like databases and email servers. Trellix analysts have identified a new binary used in RansomHouse attacks, specifically tailored for targeting ESXi systems.
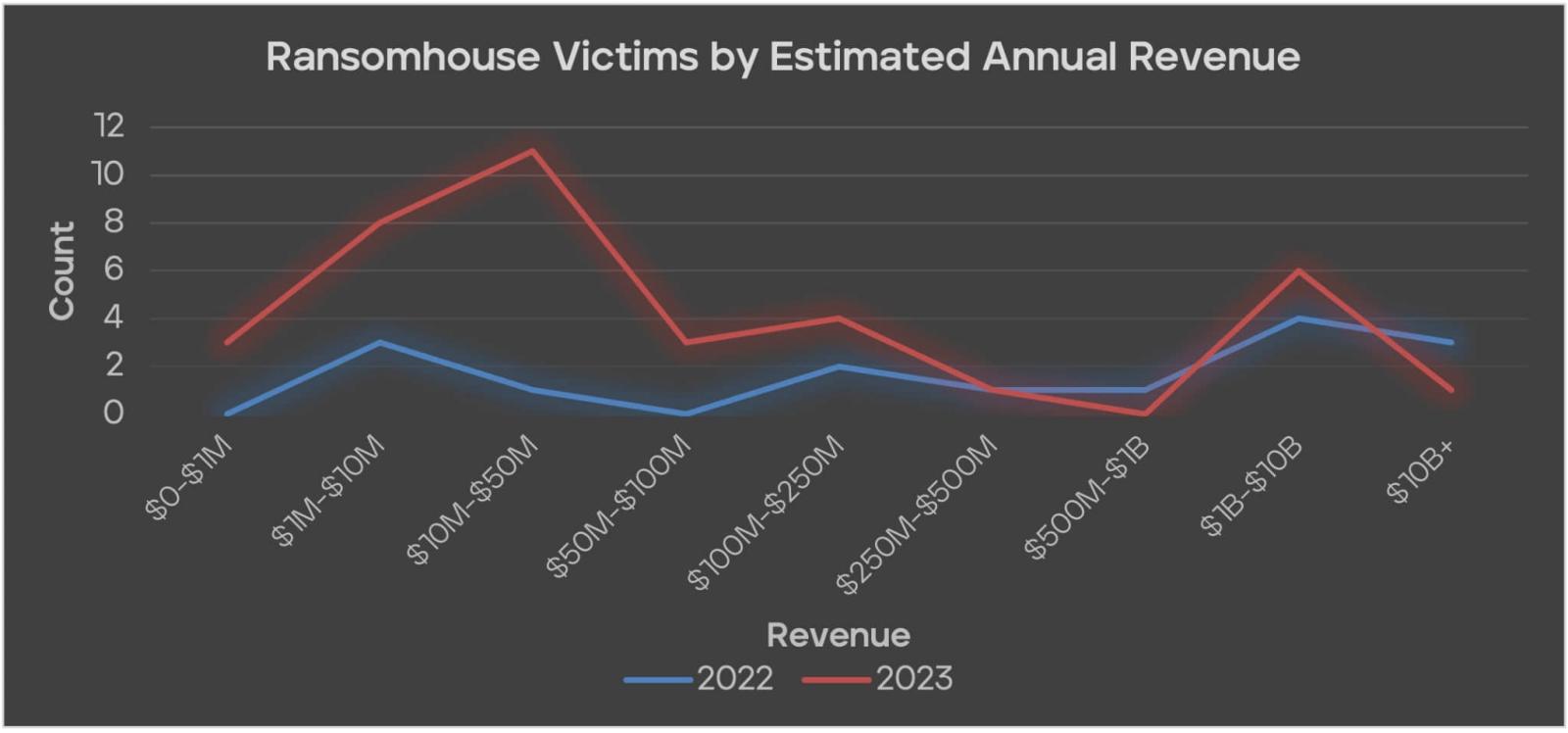 RansomHouse’s victims sizes and counts (Trellix)
RansomHouse’s victims sizes and counts (Trellix)
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
MrAgent’s Functionality
MrAgent’s primary function is to identify host systems, disable their firewalls, and automate the ransomware deployment process across multiple hypervisors simultaneously, compromising all managed virtual machines (VMs). The tool supports custom configurations for ransomware deployment received directly from the command and control (C2) server
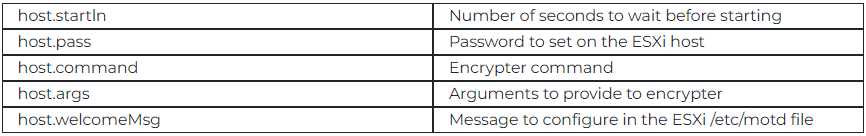 Typical MrAgent configuration (Trellix)
Typical MrAgent configuration (Trellix)
Windows Version and Adaptations
Trellix has also discovered a Windows version of MrAgent, featuring OS-specific adaptations such as the use of PowerShell for certain tasks.This cross-platform capability demonstrates RansomHouse’s intent to maximize the impact of their campaigns across different operating systems.
Trending: Jeff Foley – OWASP Amass Founder
Trending: Recon Tool: go-dork


