New Scanner Released to Detect CUPS RCE Vulnerability CVE-2024-47176

New Scanner Released to Detect CUPS RCE Vulnerability CVE-2024-47176
A new automated scanner has been developed to help security professionals detect devices vulnerable to the Common Unix Printing System (CUPS) Remote Code Execution (RCE) flaw, tracked as CVE-2024-47176. Discovered by Simone Margaritelli, this flaw allows attackers to execute arbitrary code remotely, albeit with some real-world constraints.
CUPS Flaw: A DDoS Amplification Threat
Although RCE exploitation in real-world scenarios is limited, Akamai demonstrated that CVE-2024-47176 can enable a 600x amplification factor in distributed denial-of-service (DDoS) attacks, raising further security concerns.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Marcus Hitchins Releases Python-Based Scanner
Cybersecurity researcher Marcus Hitchins (aka MalwareTech) developed the cups_scanner.py tool to allow system administrators to scan networks for vulnerable CUPS-Browsed services. The tool helps detect instances of CUPS-Browsed bound to UDP port 631, which can expose devices to unauthorized access or exploitation.
How the Scanner Works
The scanner sends custom UDP packets to broadcast addresses on port 631. Vulnerable CUPS instances respond by sending HTTP requests back to the scanner’s server. The results are logged, allowing administrators to identify and target affected devices for patching or reconfiguration.
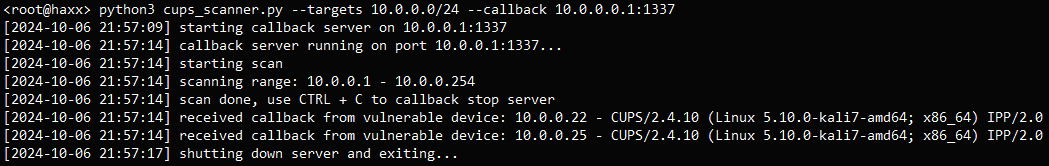 Example scan and results
Example scan and results
Source: GitHub
Trending: 10 Misconceptions about Hacking
Trending: Recon Tool: Argus
Logs and Next Steps
The tool creates two logs: cups.log, detailing the IP addresses and CUPS versions of responding devices, and requests.log, capturing the raw HTTP requests for further analysis. By using this tool, system administrators can mitigate exposure to CVE-2024-47176, improving network security.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













