New Specula Tool Turns Microsoft Outlook into C2 Beacon for Remote Code Execution

Specula: A New Post-Exploitation Framework
Microsoft Outlook can be turned into a command-and-control (C2) beacon to remotely execute code, as demonstrated by a new red team post-exploitation framework named “Specula,” released today by cybersecurity firm TrustedSec.
Exploiting an Old Vulnerability
This C2 framework works by creating a custom Outlook Home Page using WebView, exploiting CVE-2017-11774, an Outlook security feature bypass vulnerability patched in October 2017.
“In a file-sharing attack scenario, an attacker could provide a specially crafted document file designed to exploit the vulnerability, and then convince users to open the document file and interact with the document,” Microsoft explains. Despite the patch, attackers can still create malicious home pages using Windows Registry values, even on systems with the latest Office 365 builds.
How Specula Operates
Specula runs purely in Outlook’s context, setting a custom Outlook home page via registry keys that call out to an interactive Python web server. Non-privileged threat actors can set a URL target in Outlook’s WebView registry entries under HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\WebView\ to an external website under their control.
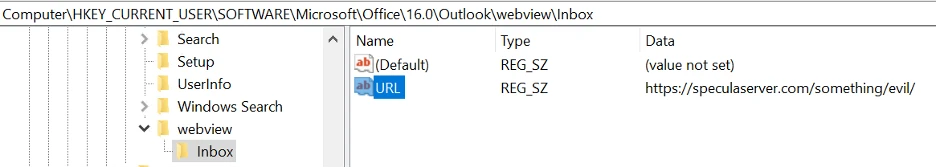 Outlook Specula registry value (TrustedSec)
Outlook Specula registry value (TrustedSec)
The attacker-controlled Outlook home page serves custom VBscript files that can execute arbitrary commands on compromised Windows systems. TrustedSec notes, “Specula has been able to leverage this specific channel for initial access in hundreds of clients despite the existing knowledge and preventions available for this technique.”
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Mechanism of the Attack
When a custom home page is set via the registry keys, Outlook will download and display that HTML page instead of the normal mailbox elements (inbox, calendar, sent, etc.) when the associated tab is selected. From the downloaded HTML page, attackers can run VBscript or Jscript within a privileged context, granting them full access to the local system as if they were running cscript or wscript.exe.
Persistence and Lateral Movement
While a device first needs to be compromised to configure the Outlook Registry entry, once configured, attackers can use this technique for persistence and lateral movement to other systems. Since outlook.exe is a trusted process, it facilitates evading existing security software as commands are executed.
Trending: 10 Misconceptions about Hacking
Trending: Digital Forensics Tool: Horus
Historical Context and Ongoing Threat
As U.S. Cyber Command (US CyberCom) warned five years ago, the CVE-2017-11774 Outlook vulnerability was also used to target U.S. government agencies. Security researchers from Chronicle, FireEye, and Palo Alto Networks later linked these attacks to the Iranian-sponsored APT33 cyber espionage group.
“FireEye first observed APT34 use CVE-2017-11774 in June 2018, followed by adoption by APT33 for a significantly broader campaign beginning in July 2018 and continuing for at least a year,” FireEye cybersecurity researchers said at the time.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













