Caketap, a New Unix rootkit for stealing ATM banking data


Reading Time: 2 Minutes
Threat analysts following the activity of LightBasin, a financially motivated group of hackers, report the discovery of a previously unknown Unix rootkit that is used to steal ATM banking data and conduct fraudulent transactions.
The particular group of adversaries has been recently observed targeting telecom companies with custom implants, while back in 2020, they were spotted compromising managed service providers and victimizing their clients.
In a new report by Mandiant, researchers present further evidence of LightBasin activity, focusing on bank card fraud and the compromise of crucial systems.
Tapping into your banking data
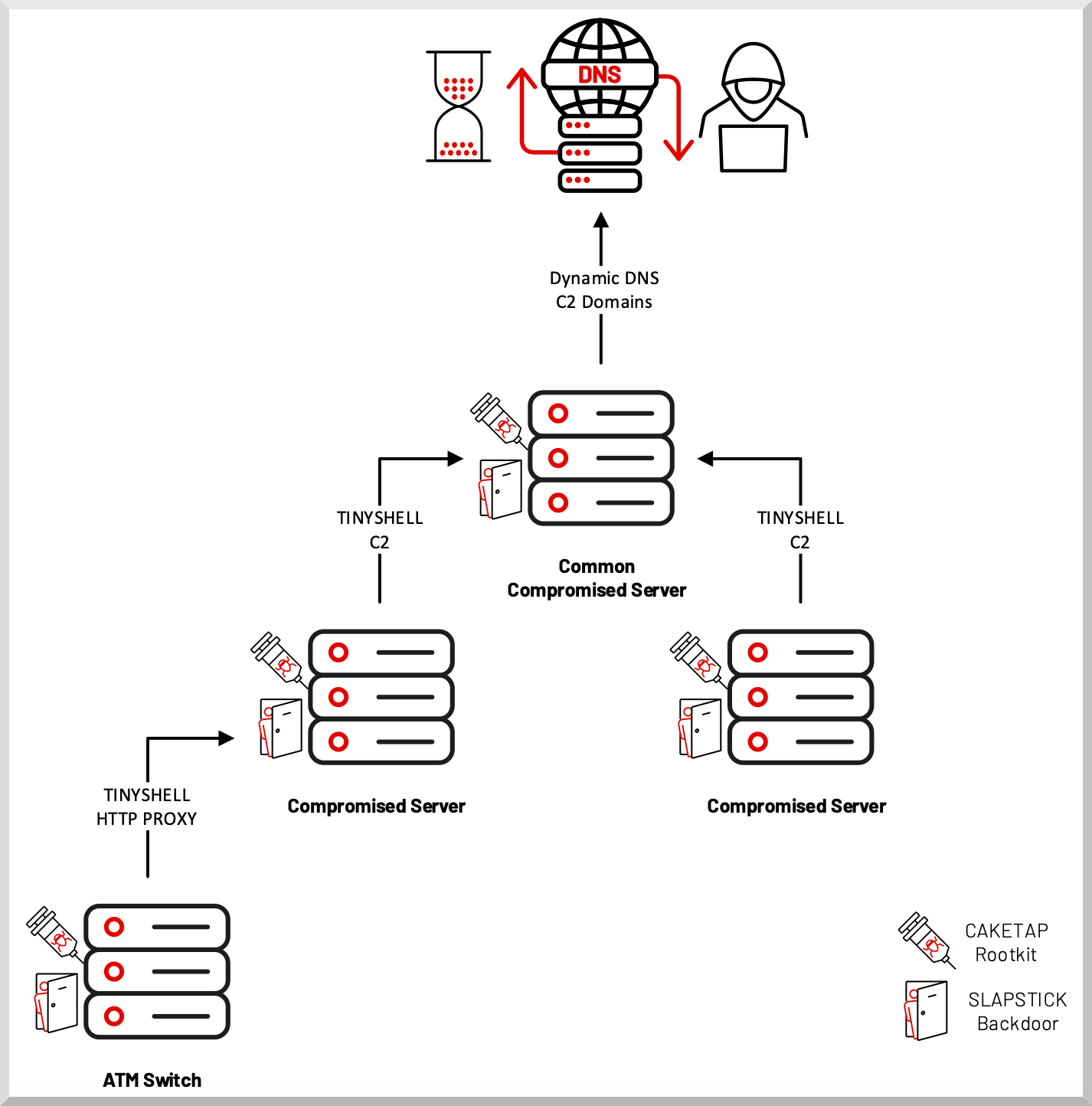
LightBasin’s new rootkit is a Unix kernel module named “Caketap” that is deployed on servers running the Oracle Solaris operating system.
When loaded, Caketap hides network connections, processes, and files while installing several hooks into system functions to receive remote commands and configurations.
The commands observed by the analysts are the following:
- Add the CAKETAP module back to the loaded modules list
- Change the signal string for the getdents64 hook
- Add a network filter (format p)
- Remove a network filter
- Set the current thread TTY to not to be filtered by the getdents64 hook
- Set all TTYs to be filtered by the getdents64 hook
- Displays the current configuration
See Also: Complete Offensive Security and Ethical Hacking Course
The ultimate goal of Caketap is to intercept banking card and PIN verification data from breached ATM switch servers and then use the stolen data to facilitate unauthorized transactions.
The messages intercepted by Caketap are destined for the Payment Hardware Security Module (HSM), a tamper-resistant hardware device used in the banking industry for generating, managing, and validating cryptographic keys for PINs, magnetic stripes, and EMV chips.
Caketap manipulates the card verification messages to disrupt the process, stops those that match fraudulent bank cards, and generates a valid response instead.
In a second phase, it saves valid messages that match non-fraudulent PANs (Primary Account Numbers) internally and sends them to the HSM so that routine customer transactions aren’t affected and the implant operations remain stealthy.
See Also: Offensive Security Tool: Scapy
“We believe that CAKETAP was leveraged by UNC2891 (LightBasin) as part of a larger operation to successfully use fraudulent bank cards to perform unauthorized cash withdrawals from ATM terminals at several banks,” explains Mandiant’s report.
Other tools linked to the actor in previous attacks include Slapstick, Tinyshell, Steelhound, Steelcorgi, Wingjook, Wingcrack, Binbash, Wiperight, and the Mignogcleaner, all of which Mandiant confirmed as still deployed in LightBasin attacks.
See Also: Hacking stories: MafiaBoy, the hacker who took down the Internet
Source: bleepingcomputer.com
Full post












