New version of Clop ransomware targets Linux servers

Reading Time: 3 Minutes
New Clop variant
The Clop ransomware gang is using a new malware variant that targets Linux servers, but the encryption scheme is flawed, allowing victims to retrieve their files for free.
The Linux variant of Clop was spotted in December 2022 by researcher Antonis Terefos at SentinelLabs after the threat group used it in an attack against a Colombian university, in conjunction with its Windows version. Although the Linux version is similar to the Windows version, with the same encryption method and process logic, there are some differences, mainly in OS API calls and features yet to be implemented.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Clop ransomware features and flaws
The Linux malware is still in its early stages and lacks proper obfuscation and evasive mechanisms, making it vulnerable to attack. The malware creates a new process upon launch, which attempts to gain higher permissions to allow data encryption. The targeted files and folders include the user’s personal files in the “/home” directory, the “/root” and “/opt” directories, and the Oracle database folders (“/u01” – “/u04”). The specific targeting of Oracle database folders is not commonly seen in Linux ransomware encryptors, which usually focus on encrypting ESXi virtual machines.
The Linux variant lacks some features, including drive enumeration, command line parameters, and the exclusion of certain file types and folders from encryption. The encryption scheme is also weak, with a hardcoded RC4 “master key” used to generate encryption keys and to encrypt and store the RC4 key locally. The key is not validated, and the RC4 and extra data are written on the file, making the encryption easily reversible.
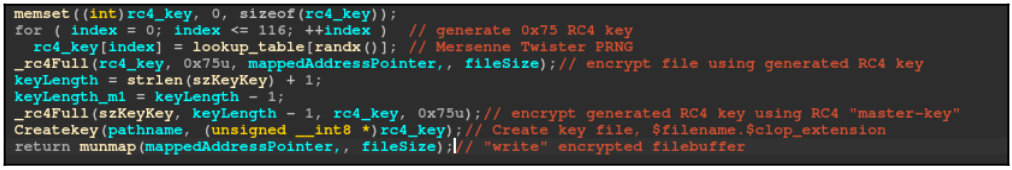 Encryption scheme flaw (SentinelLabs)
Encryption scheme flaw (SentinelLabs)
Trending: Major Cyber Attacks of 2022
Trending: Recon Tool: ScopeHunter
SentinelLabs shared its decryptor
Despite its weaknesses, the use of the Linux variant in actual Clop attacks demonstrates the threat actors’ preference for having a Linux version, even a flawed one, to attack Linux systems within target organizations. SentinelLabs has shared its decryptor with law enforcement to help victims recover their files, and will continue to collaborate with relevant organizations to improve the economics of the ransomware space in favor of defenders.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












