New Version of iOS Spyware LightSpy Adds Device-Disabling Capabilities

Security researchers have discovered an enhanced version of the iOS spyware LightSpy, incorporating advanced capabilities to capture extensive device data and even disable infected devices, preventing them from rebooting.
Enhanced Spyware Capabilities
LightSpy, a modular spyware implant first identified in 2020 targeting Hong Kong users, now includes 28 plugins — up from the previous 12 — enabling it to capture a wide range of sensitive information. These plugins extract data including Wi-Fi details, location data, iCloud Keychain, screenshots, contacts, call history, and app information from popular apps such as WhatsApp, WeChat, Telegram, and LINE.
The attack chains distributing LightSpy exploit known vulnerabilities in iOS and macOS, utilizing a WebKit vulnerability tracked as CVE-2020-3837 to launch a binary disguised as a “.PNG” file. This binary acts as a dropper for additional payloads that facilitate data exfiltration from infected devices.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Destructive Plugin Features Now Introduced
The latest version of LightSpy includes new plugins capable of destructive actions, such as deleting media files, contacts, and even Wi-Fi network configurations. This upgrade enables threat actors to fully disrupt compromised devices, freezing them and blocking attempts to reboot. Additionally, the spyware can send fake push notifications containing URLs, potentially luring users to malicious sites or downloads.
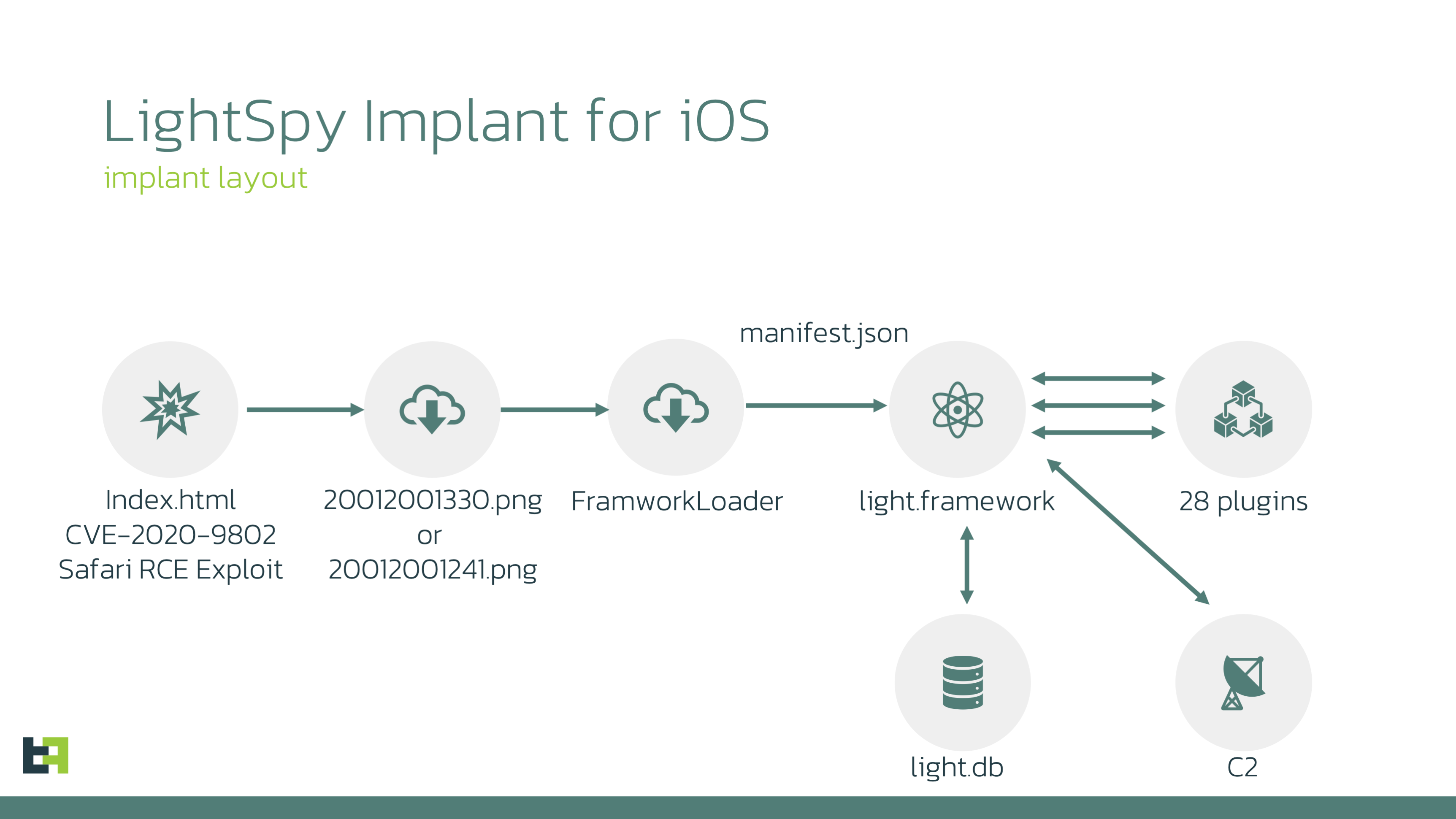
Distribution and Attribution Unclear, But Signs Point to China
While the exact distribution vehicle remains unknown, researchers suspect watering hole attacks to be the primary infection vector. No group has claimed responsibility, but LightSpy’s operators are believed to be based in China, given the use of the GCJ-02 coordinate system in the spyware’s location plugins.
Trending: Red Teaming Tool: avred
Staying Safe: The Need for Regular Updates
ThreatFabric’s analysis underlines the importance of updating iOS devices to avoid exploitation from vulnerabilities that LightSpy leverages. With threat actors closely monitoring security disclosures for new exploits, maintaining device security with regular updates has never been more critical.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com













