New Windows Zero-Day Exploited in Active Attacks

The Windows vulnerability MSHTML spoofing, tracked as CVE-2024-43461, was first disclosed by Microsoft as part of the September 2024 Patch Tuesday. Initially, it wasn’t marked as exploited, but later updates confirmed that it had been actively used in attacks before it was fixed. Void Banshee, a cyber espionage group targeting North America, Europe, and Southeast Asia, utilized this flaw to deploy information-stealing malware.
Exploiting the CVE-2024-43461 Vulnerability
- Malicious Shortcut Files (.url): The attacks began with the use of Windows Internet Shortcut (.url) files. When these files were clicked, they triggered the now-deprecated Internet Explorer (IE) instead of Microsoft Edge, forcing the system to open a malicious website controlled by the attackers.
- HTA File Execution via Internet Explorer: Once the malicious website was opened, it prompted the download of an HTML Application (HTA) file. HTA files are executable files that run scripts on the user’s device. In this case, the HTA file contained a script to install the Atlantida info-stealer, a malware that harvests sensitive information such as:
- Passwords
- Authentication cookies
- Cryptocurrency wallets
The vulnerability allowed the attackers to hide the true nature of the file by spoofing its file extension, making it appear as something benign like a PDF file instead of a .hta executable.
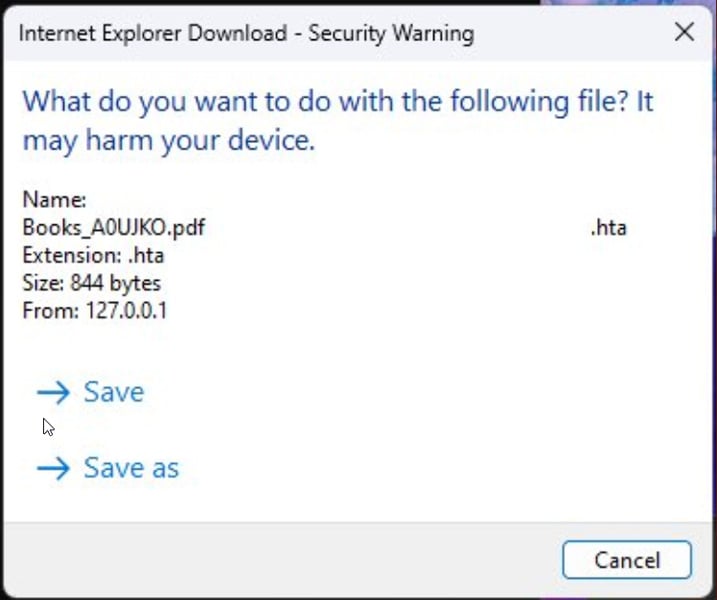
- Using Braille Whitespace Characters for Concealment: Attackers exploited a flaw in Windows MSHTML (the core component responsible for rendering web content in Internet Explorer) to spoof the file extension of the HTA file. The technique used braille whitespace characters (
%E2%A0%80) to push the “.hta” extension out of the user’s view in the file name prompt.For example, a file name like this:Books_A0UJKO.pdf%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80%E2%A0%80.htaWould be displayed as:
Books_A0UJKO.pdf...This trick made the file appear to be a PDF when in reality, it was an executable HTA file. When the user clicked the file, they unknowingly executed the Atlantida malware.
 Braile whitespace characters pushing HTA extension out of view
Braile whitespace characters pushing HTA extension out of view
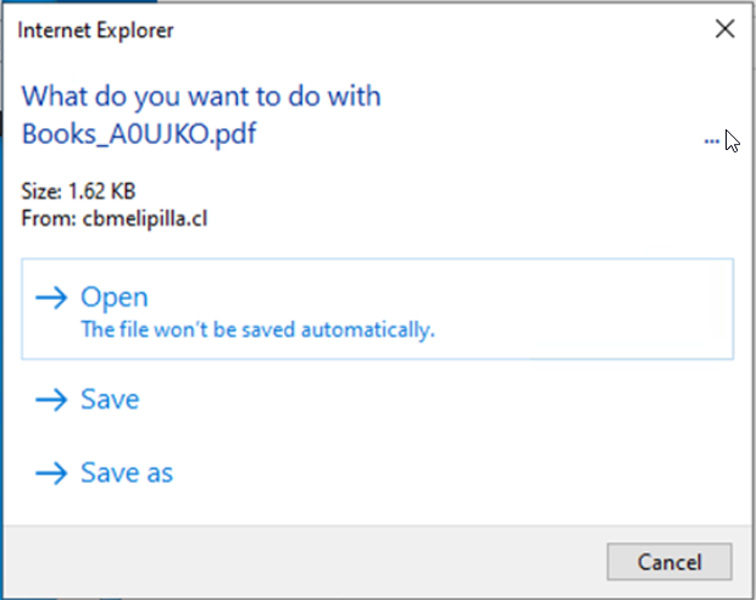
Source: Trend Micro - Final Execution and Infection: Once the user opened the spoofed file, the HTA file was executed, running the script that installed the Atlantida info-stealer on the device. This malware was designed to silently steal credentials, financial information, and other sensitive data, sending it back to the attackers.

Security update now shows HTA extension
Source: Peter Girnus
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
How the Vulnerability Works:
The core of this attack hinged on a spoofing flaw in how Windows handled file extension prompts. By leveraging CVE-2024-43461, attackers were able to manipulate the way Windows displayed file extensions, hiding the true identity of dangerous files and tricking users into running them.
- MSHTML is a rendering engine used by Internet Explorer and other Windows components to display web content. The vulnerability allowed malicious actors to exploit this engine to manipulate how file extensions were shown in Windows prompts.
- This spoofing vulnerability was critical because it exploited the interface where users are prompted to open files. If a file is mislabeled as something innocuous like a PDF, users are far more likely to trust and open it, thereby executing malicious content.
Trending: Understanding PTaaS and SOC
Trending: Offensive Security Tool: headi
Fixing the CVE-2024-43461 Flaw:
Microsoft’s fix for CVE-2024-43461 included ensuring that braille whitespace characters are no longer able to obscure the actual file extension when users are prompted to open files. Although the braille whitespace is still present, Windows now correctly displays the .hta extension in the prompt, alerting users to the true nature of the file.
However, as ZDI researcher Peter Girnus noted, while the fix prevents the extension from being completely hidden, the use of whitespace may still confuse some users into thinking the file is safe (e.g., a PDF).
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com


 Braile whitespace characters pushing HTA extension out of view
Braile whitespace characters pushing HTA extension out of view