New Ymir Ransomware Launches In-Memory Attacks Post-RustyStealer Infections

Ymir Ransomware Targets Networks Infected by RustyStealer Malware
A newly discovered ransomware variant, Ymir, is infiltrating networks previously compromised by the RustyStealer infostealer malware, indicating an organized shift towards cybercrime partnerships. First observed in July 2024 and targeting companies worldwide, Ymir is identified for its memory-based execution and innovative approach to encryption.
RustyStealer Sets the Stage for Ymir Ransomware
RustyStealer, documented initially in 2021, is a credential-stealing malware enabling unauthorized access by harvesting login data. In recent cases examined by Kaspersky, RustyStealer infiltrated targeted systems two days before Ymir ransomware deployment. By compromising high-privilege accounts, RustyStealer allows attackers to execute lateral movements, ultimately paving the way for Ymir ransomware.
Attackers using RustyStealer performed lateral movement across networks with tools like Windows Remote Management (WinRM) and PowerShell. They installed additional tools, such as Process Hacker and Advanced IP Scanner, and used SystemBC malware scripts to establish hidden channels, potentially for data exfiltration or command execution. This foothold, supported by RustyStealer, facilitated Ymir’s eventual deployment as the final payload.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Ymir: In-Memory Execution and Advanced Encryption Techniques
The Ymir ransomware variant is unusual for its in-memory operation. Utilizing memory functions like malloc, memmove, and memcmp, it evades detection by residing entirely in the system memory. On launch, Ymir performs system reconnaissance, including retrieving system time and date, process details, and uptime to detect sandboxed environments and avoid rendering the system inoperable.
Ymir encrypts files using the ChaCha20 cipher, a highly secure, efficient encryption algorithm. Files are appended with a random extension (e.g., “.6C5oy2dVr6”), and the ransom note, INCIDENT_REPORT.pdf, is generated in each directory with encrypted files. Kaspersky researchers have also noted Lingala language references in the ransomware’s code.
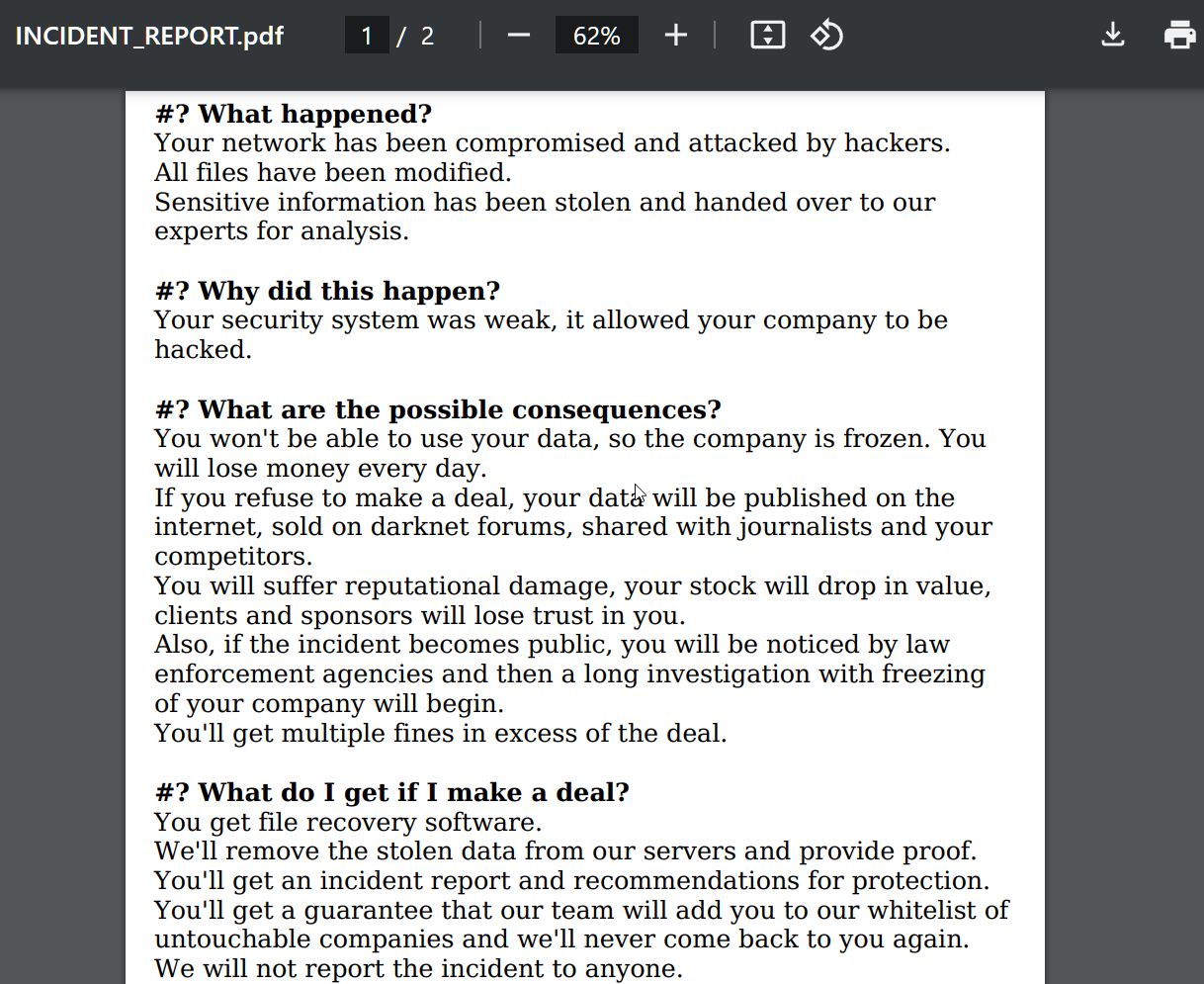 Ymir ransom note
Ymir ransom note
Source: BleepingComputer
Ymir Delivers Ransom Demands with Unique Strategies
Following file encryption, Ymir alters the Windows Registry “legalnoticecaption” to display an extortion notice before a user logs in. Each ransom note claims that data theft has occurred, and Kaspersky suspects this was achieved through tools deployed before Ymir’s infection. For stealth, Ymir uses PowerShell to erase its executable, avoiding forensic analysis and raising its chances of evading detection.
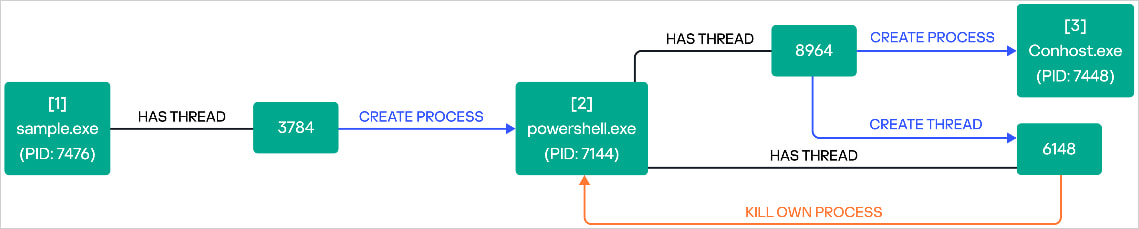 Ymir’s execution process
Ymir’s execution process
Source: Kaspersky
Trending: Blue Team Tool: Ghostport
Potential Threat Expansion and Indicators of Compromise
While Ymir has yet to establish a dedicated data leak site, accumulating victim data could be in its plans. Kaspersky researchers caution that Ymir’s connection with RustyStealer could make it a rapidly expanding threat, especially as it capitalizes on RustyStealer’s existing network footholds.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













