New Zergeca Botnet: A Powerful New Threat that Employs Advanced Evasion Tactics and DDoS Attacks

Discovery of the Zergeca Botnet
Cybersecurity researchers have uncovered a new botnet named Zergeca, capable of conducting distributed denial-of-service (DDoS) attacks. Written in Golang, the botnet is named after a string “ootheca” found in the command-and-control (C2) servers, “ootheca[.]pw” and “ootheca[.]top”.
Advanced Capabilities Beyond DDoS
“Functionally, Zergeca is not just a typical DDoS botnet,” the QiAnXin XLab team reported. “Besides supporting six different attack methods, it also has capabilities for proxying, scanning, self-upgrading, persistence, file transfer, reverse shell, and collecting sensitive device information.”
Technical Sophistication and Evasion Techniques
Zergeca is notable for using DNS-over-HTTPS (DoH) for Domain Name System (DNS) resolution of the C2 server and employing a lesser-known library known as Smux for C2 communications. This sophisticated approach aids in evading detection and complicates mitigation efforts.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Development and Historical Context
There is evidence that Zergeca is actively being developed and updated to support new commands. The C2 IP address 84.54.51[.]82, which previously distributed the Mirai botnet around September 2023, began serving as a C2 server for Zergeca as of April 29, 2025. This suggests that the threat actors might have accumulated experience operating the Mirai botnet before creating Zergeca.
Global Attack Patterns
Attacks mounted by the botnet, primarily ACK flood DDoS attacks, have targeted Canada, Germany, and the U.S. between early and mid-June 2024. These attacks highlight the botnet’s global reach and potential impact on critical infrastructure and services.
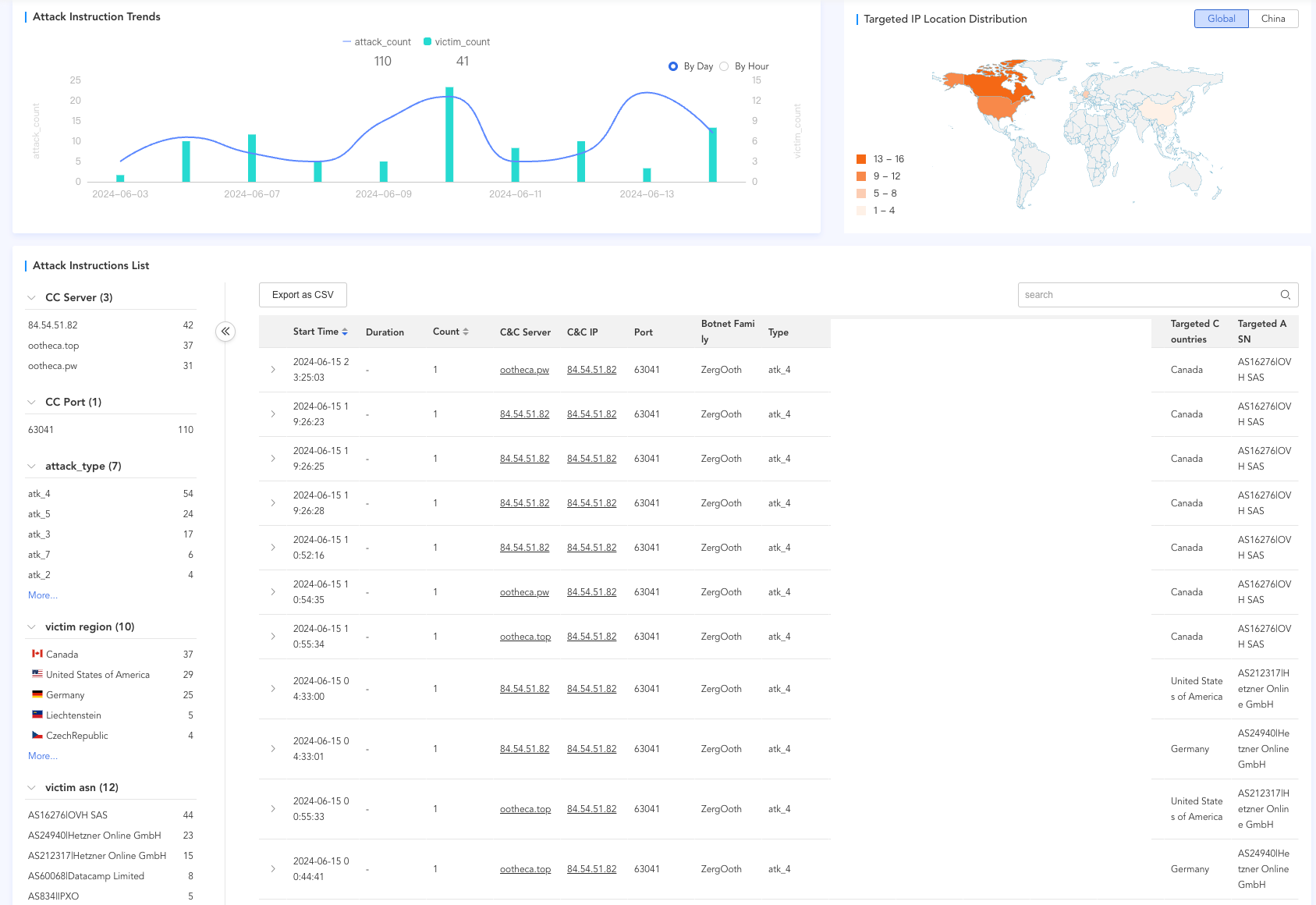
DDoS Statistics – qianxin.com
Zergeca’s Modular Architecture
Zergeca’s features span four distinct modules: persistence, proxy, silivaccine, and zombie. These modules enable the botnet to set up persistence by adding a system service, implement proxying, remove competing miner and backdoor malware to gain exclusive control over devices, and handle the main botnet functionality.
Trending: Offensive Security Tool: Genzai
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com













