NKAbuse: The First NKN-Abusing Malware Threat
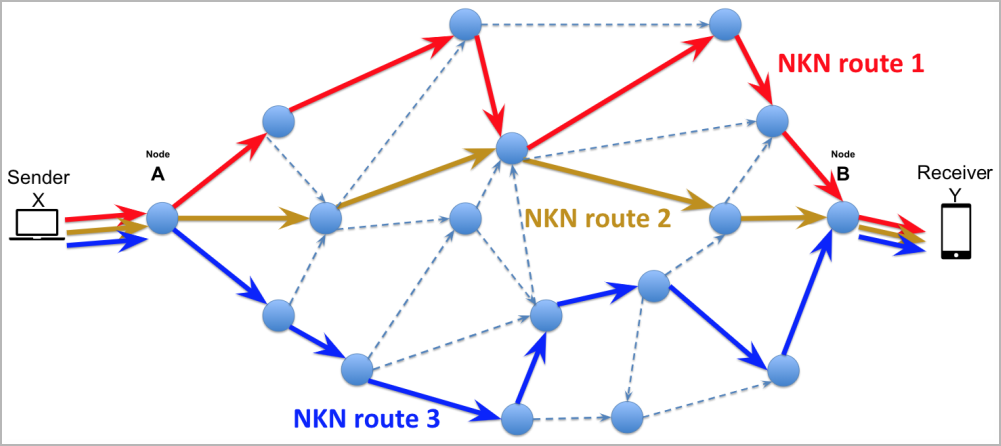 Moving data through NKN (Kaspersky)
Moving data through NKN (Kaspersky)NKAbuse
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
NKAbuse’s utilization of NKN to launch DDoS attacks poses a significant challenge for security professionals, as the attacks are difficult to trace and unlikely to be detected by conventional security tools.
By leveraging the NKN public blockchain protocol, NKAbuse can carry out flooding attacks and establish a backdoor within Linux systems, enabling it to communicate with a bot master and execute various malicious commands.
The payload commands sent by the C2 include HTTP, TCP, UDP, PING, ICMP, and SSL flood attacks aimed at a specified target.
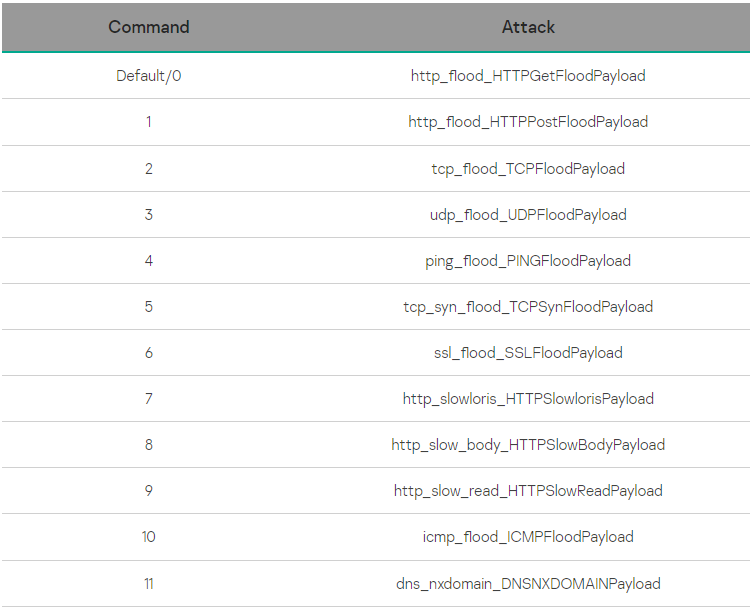 DDoS attack commands (Kaspersky)
DDoS attack commands (Kaspersky)
Trending: Recon Tool: ReconSpider
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com



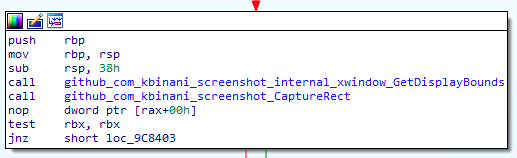 Screenshot functionality (Kaspersky)
Screenshot functionality (Kaspersky)









