Novel QR Code Exploit Circumvents Browser Isolation Security Measures

Mandiant researchers have unveiled a novel method to bypass browser isolation technology, using QR codes to enable command-and-control (C2) operations.
What Is Browser Isolation?
Browser isolation is a widely adopted security technology designed to prevent malicious code from reaching local systems. By routing all local web browser requests through remote browsers hosted in cloud environments or virtual machines:
- Scripts and content are executed remotely.
- Only the rendered pixel stream of the webpage is sent back to the local browser, ensuring malicious content cannot directly affect the user’s device.
This effectively blocks many C2 communication models, which often rely on HTTP traffic, by filtering out malicious scripts and commands.
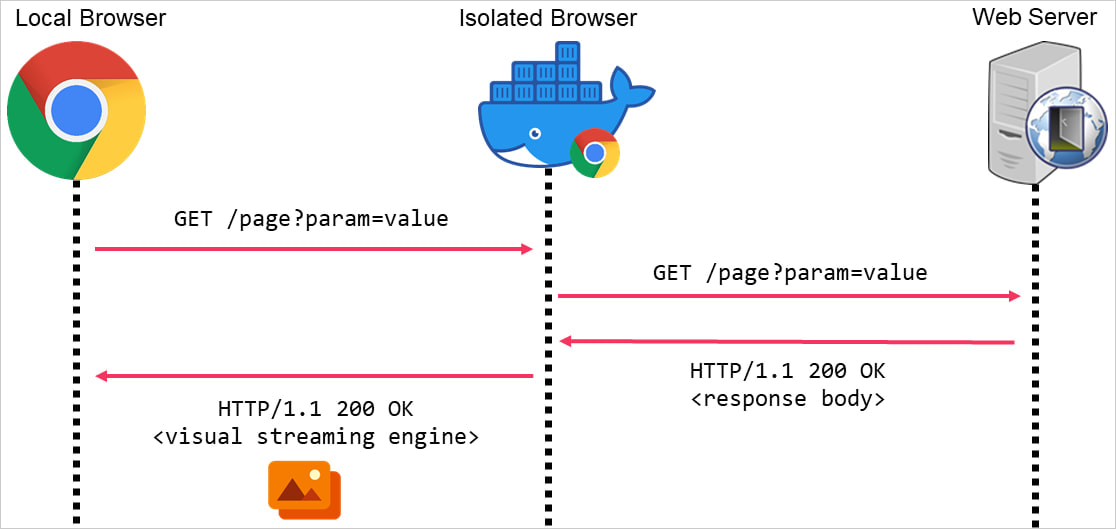 Overview of browser isolation
Overview of browser isolation
Source: Mandiant
Mandiant’s QR Code-Based Bypass
Mandiant’s researchers have developed a proof-of-concept (PoC) demonstrating how QR codes can bypass browser isolation protections.
Instead of embedding malicious commands in HTTP traffic, attackers encode them into QR codes displayed on the webpage. Because browser isolation streams visual content, the QR codes remain intact when rendered and are sent back to the client.
How It Works:
- QR Code Delivery: Commands are encoded as QR codes on the malicious webpage.
- Local Retrieval: A headless browser or malware already infecting the target device captures and decodes the QR codes.
- Execution: The decoded commands are used for C2 operations, enabling remote attackers to issue commands or exfiltrate data.
Mandiant integrated the attack with Cobalt Strike’s External C2 feature, a well-known penetration testing framework often exploited by attackers.
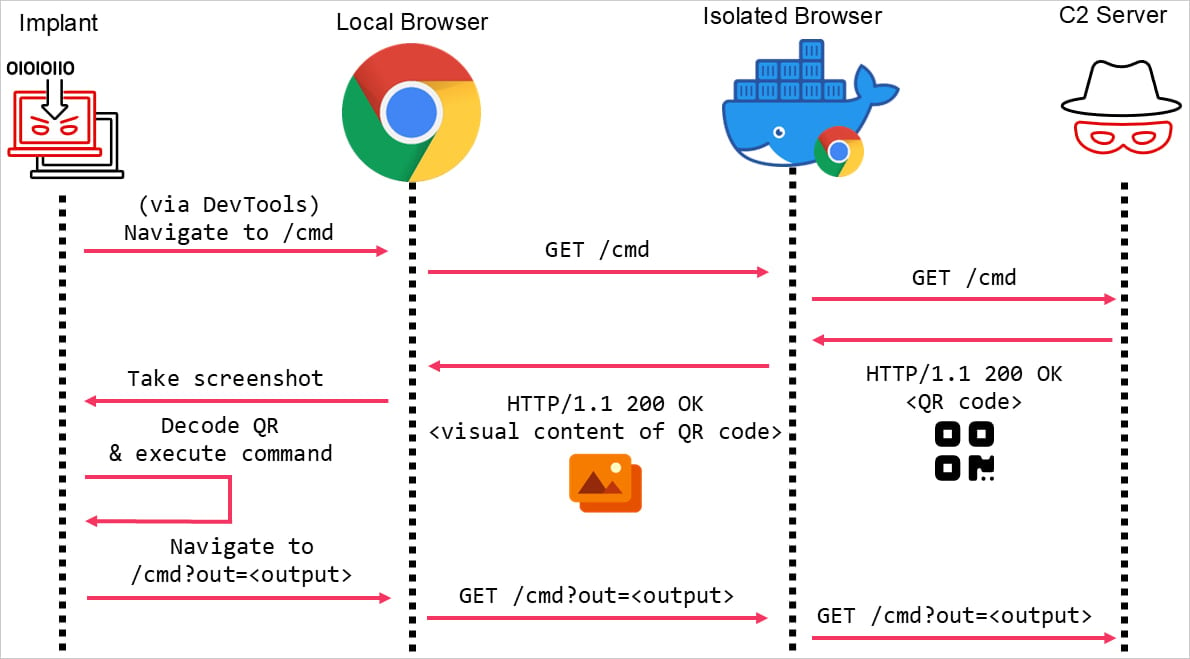 Bypassing browser isolation using a QR code
Bypassing browser isolation using a QR code
Source: Mandiant
Offensive Security, Bug Bounty Courses
Challenges and Limitations
While innovative, this technique has practical constraints:
Limited Data Capacity:
- QR codes can only store up to 2,189 bytes of data per request.
- Encoding inefficiencies further reduce this limit to about 438 bytes/sec, restricting the attack to small data payloads.
Latency Issues:
- Each C2 communication takes approximately 5 seconds, significantly slowing down data transfer rates.
Real-World Countermeasures:
- Mandiant’s research did not account for advanced defenses like domain reputation checks, data loss prevention (DLP) systems, or URL heuristics, which may block or flag suspicious activity.
Trending: Recon Tool: Argus
Implications and Recommendations
Although limited in bandwidth, Mandiant’s approach highlights vulnerabilities in browser isolation systems and underscores the importance of defense-in-depth strategies.
Recommendations for Security Teams:
- Monitor for abnormal traffic patterns, particularly involving headless browsers operating in automation mode.
- Employ behavioral analytics to detect unexpected QR code-related activity.
- Enforce comprehensive endpoint monitoring to identify malware capable of decoding QR codes.
- Combine browser isolation with additional security measures, including domain reputation services and heuristic-based URL scanning.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













