Open source ‘Package Analysis’ tool finds malicious npm, PyPI packages

Reading Time: 3 Minutes
The Open Source Security Foundation (OpenSSF), a Linux Foundation-backed initiative has released its first prototype version of the ‘Package Analysis’ tool that aims to catch and counter malicious attacks on open source registries.
In a pilot run that lasted less than a month, the open source project released on GitHub, was able to identify over 200 malicious npm and PyPI packages.
Project aims to combat malware in open source registries
This week, OpenSSF released its initial prototype version of the ‘Package Analysis‘ project on GitHub.
The project repository contains tools that analyze open source packages, particularly, to hunt for malicious npm and PyPI packages.
“The Package Analysis project seeks to understand the behavior and capabilities of packages available on open source repositories: what files do they access, what addresses do they connect to, and what commands do they run?” explain Caleb Brown and David A. Wheeler, who are involved in OpenSSF’s Securing Critical Projects working group.
“The project also tracks changes in how packages behave over time, to identify when previously safe software begins acting suspiciously.”
In its test run that lasted under a month, Package Analysis was able to identify more than 200 malicious PyPI and npm components, according to OpenSSF.
The vast majority of these malicious packages, says OpenSSF, are dependency confusion and typosquatting attacks.
Among all malicious packages identified by Package Analysis, one of them is ‘colorsss’ that has been previously deemed malicious:
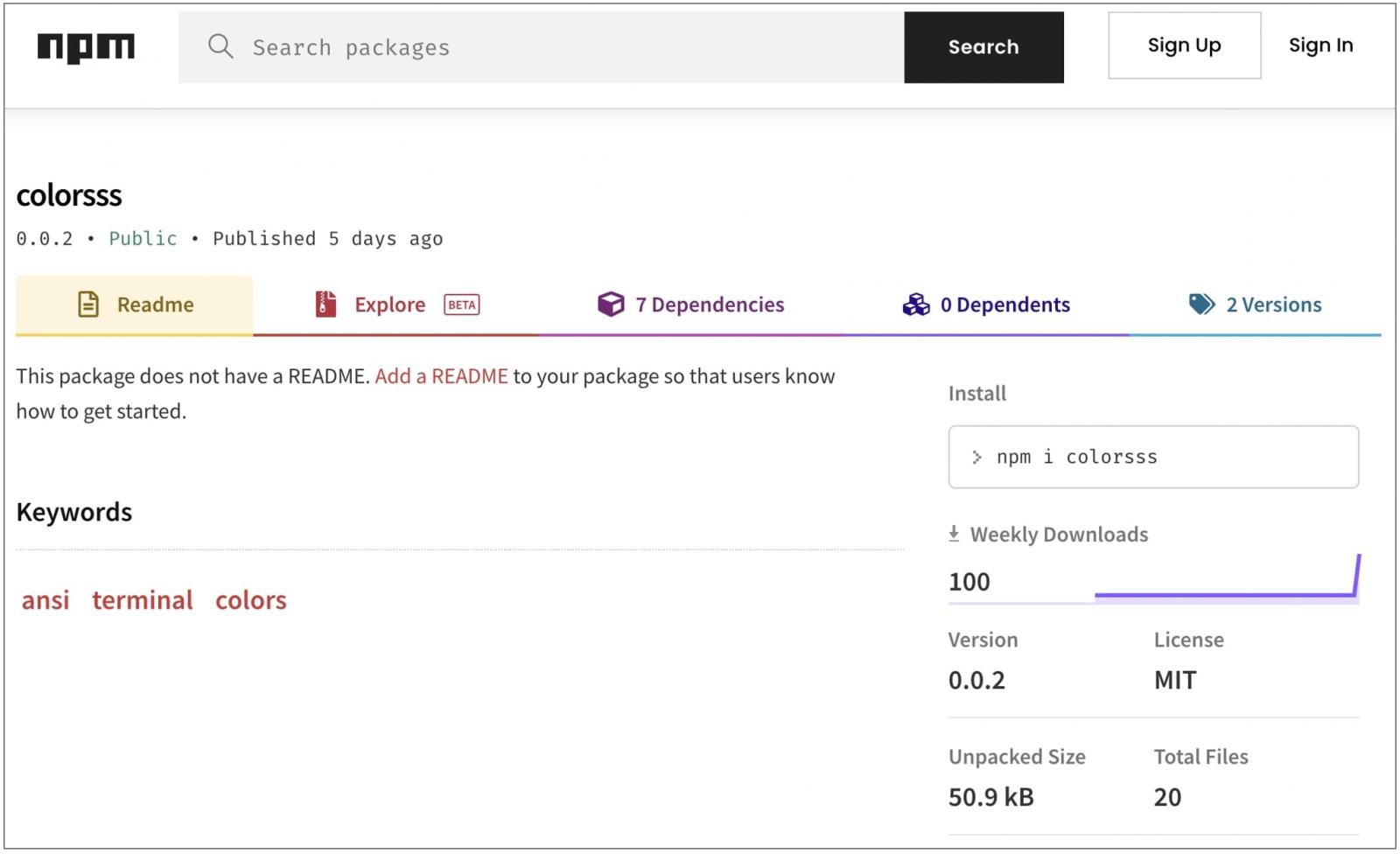
The ‘colorsss’ package is a typosquat of the popular colors npm library, select versions of which had been sabotaged by its developer this January, as first reported by BleepingComputer.
In addition to containing some legitimate files from the colors library, malicious ‘colorsss’ packs obfuscated malware, according to an archived copy of the package obtained by BleepingComputer from open source security firm Sonatype:
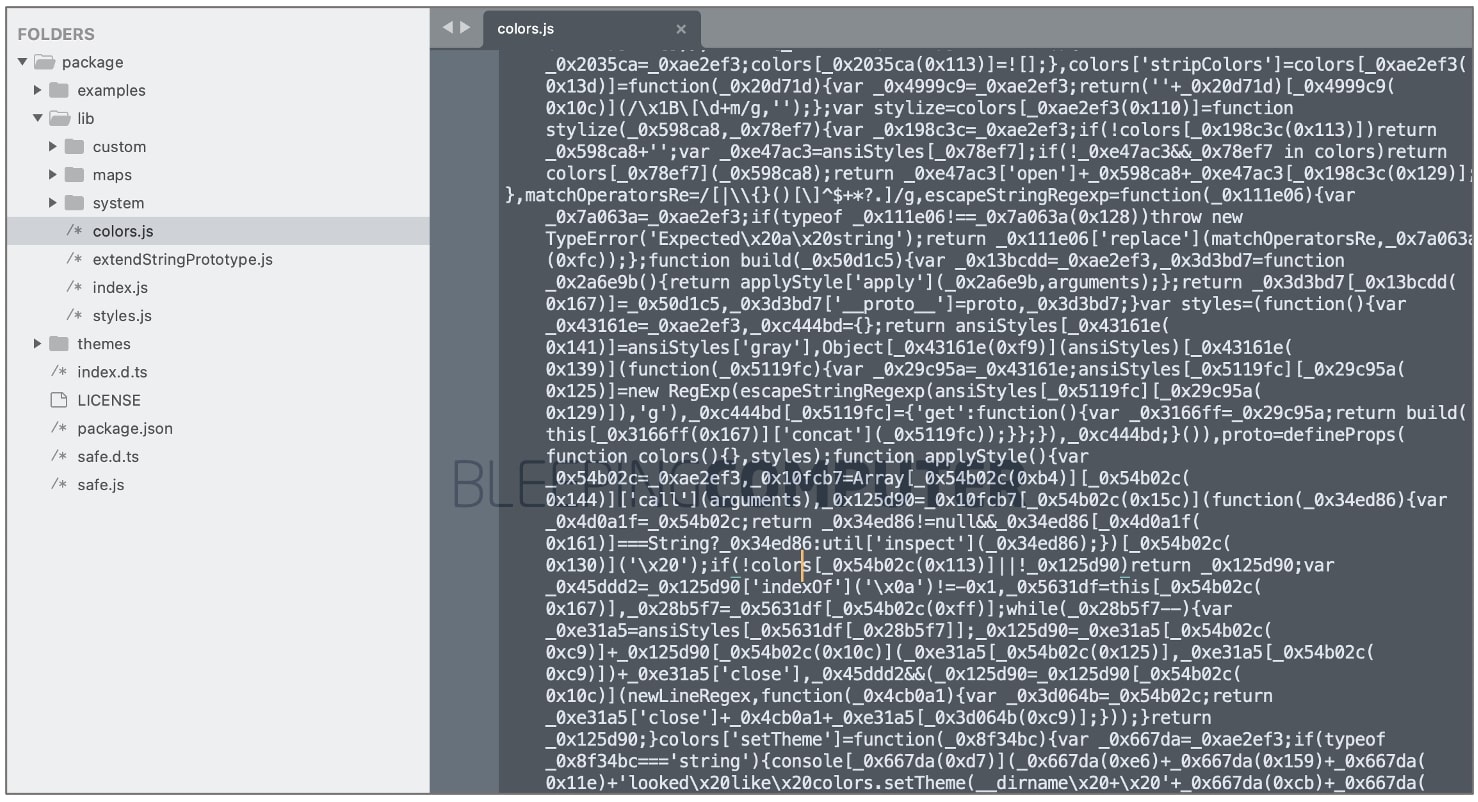
The obfuscated code in ‘colorsss’ contains Discord token stealers, a recurring theme among malicious npm packages.
“Though the project has been in development for a while, it has only recently become useful following extensive modifications based on initial experiences,” states OpenSSF in a blog post released this week.
“There are lots of opportunities for involvement with this project, and we welcome anyone interested in contributing to the future goals of… detecting differences in package behavior over time; automating the processing of the Package Analysis results; storing the packages themselves as they are processed for long-term analysis; and improving the reliability of the pipeline.”
See Also: OSINT Tool: MOSINT
See Also: Darkside hacker group, the group that provides ransomware as a service
Source: bleepingcomputer.com
Source Link













